Gotta Catch'em All! is a easy room in Tryhackme which is based on the pokemon series. The objective is to get the pokemon flags.
| Author | GhostlyPy |
| Description | This room is based on the original Pokemon series. Can you obtain all the Pokemon in this room? |
Deploy the VM and lets go.
Enumeration
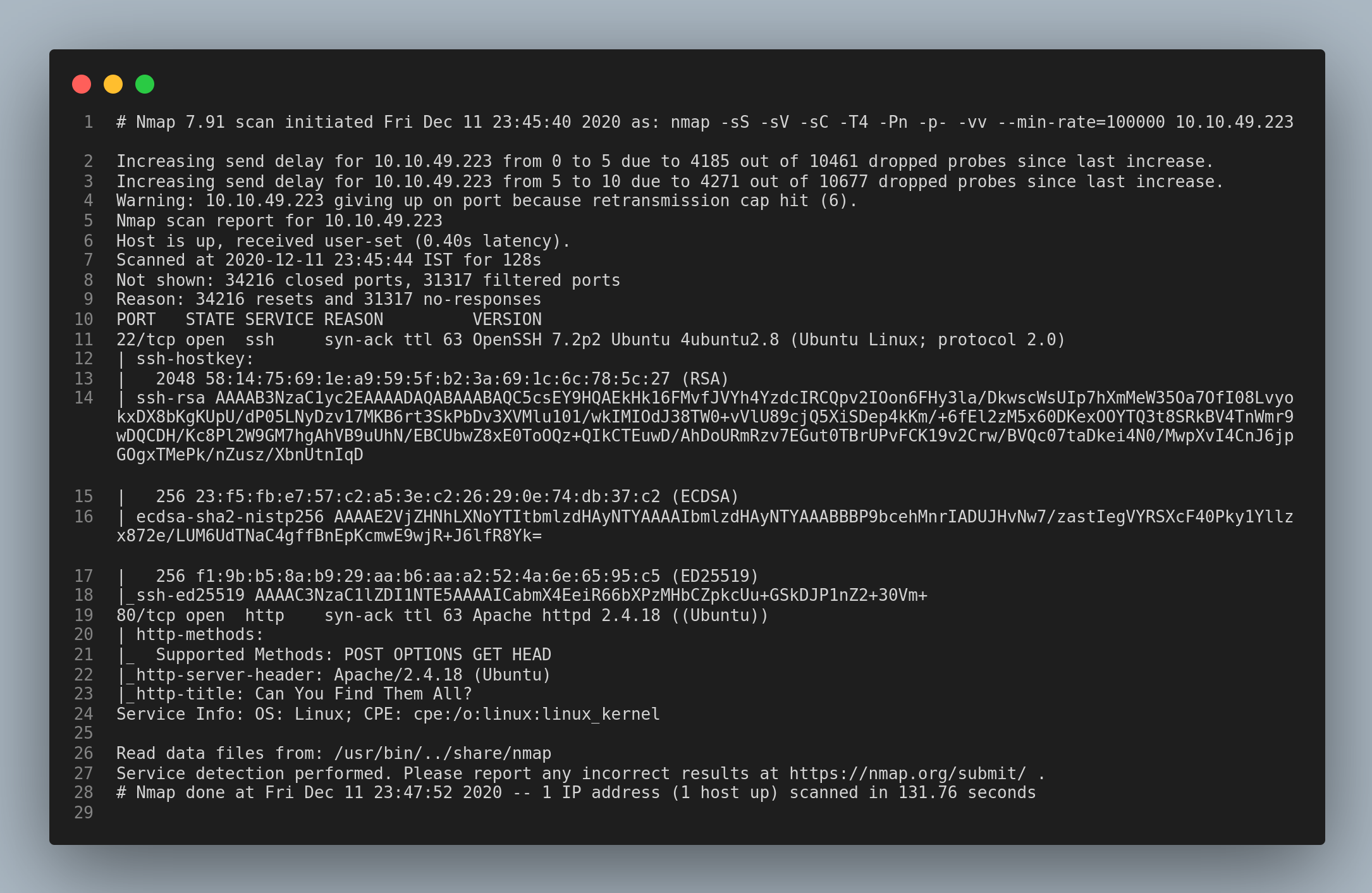
Let’s start with a nmap scan.
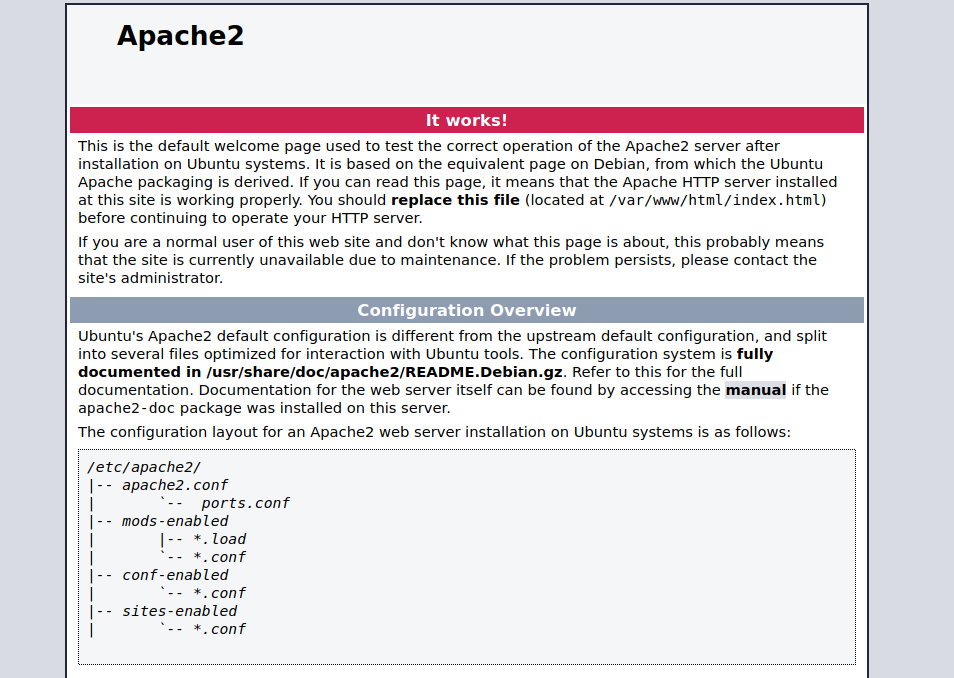
I checked the http service and I noticed the logo for the apache2 was missing.
So, I checked the source page and found this.
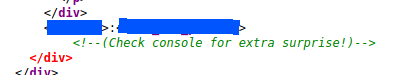
I tried this credentials for the ssh service and it worked.
Grass flag
After logging into ssh I found a zip file in the dir /Desktop.
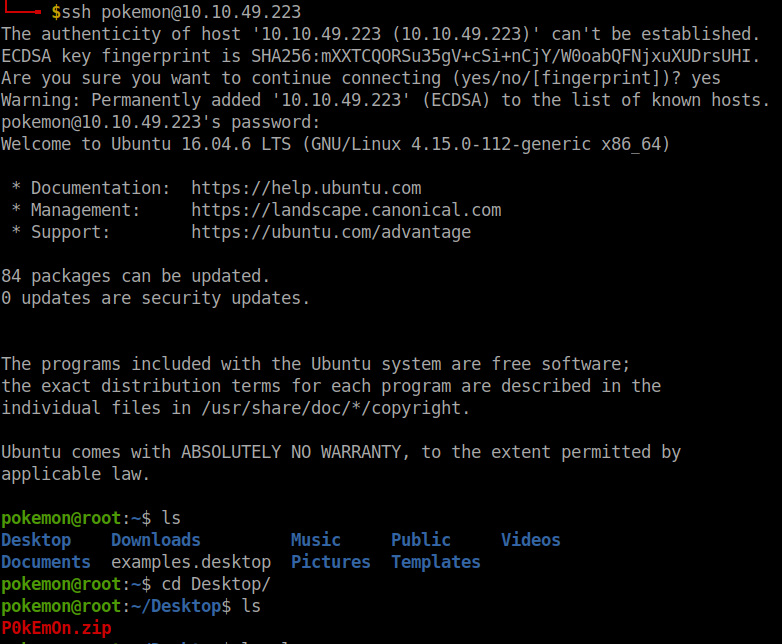
I unzipped the file.
unzip file-name.zip
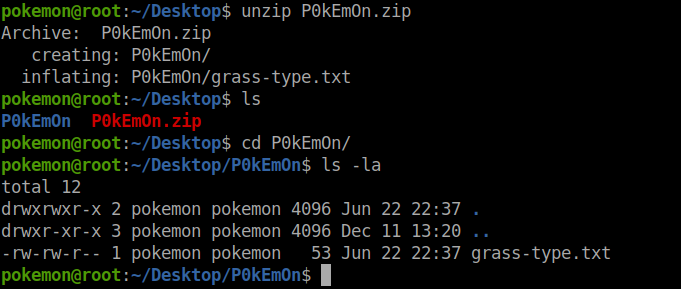
After reading the file inside the inflated directory I found that it is hex encoded.
I decoded it using cyberchef.
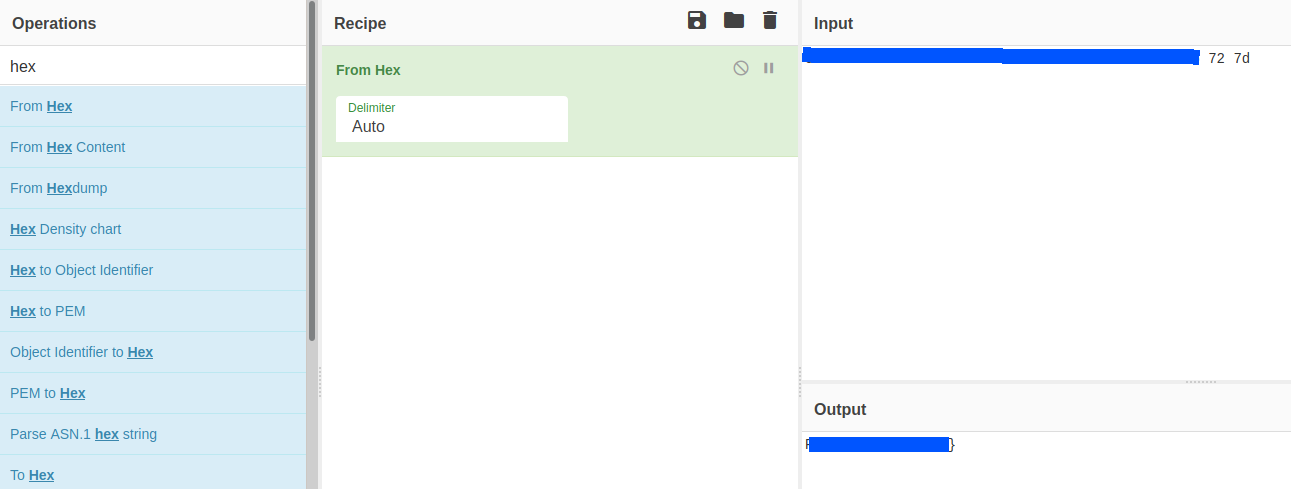
That’ll give the answer to the first question.
Water flag
Following the first flag, I figured the naming pattern and just used locate to get the flags location.
locate water-type.txt
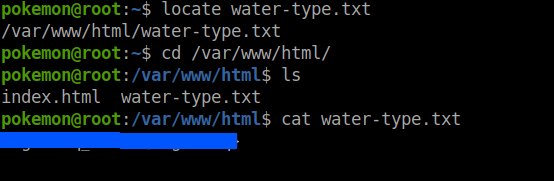
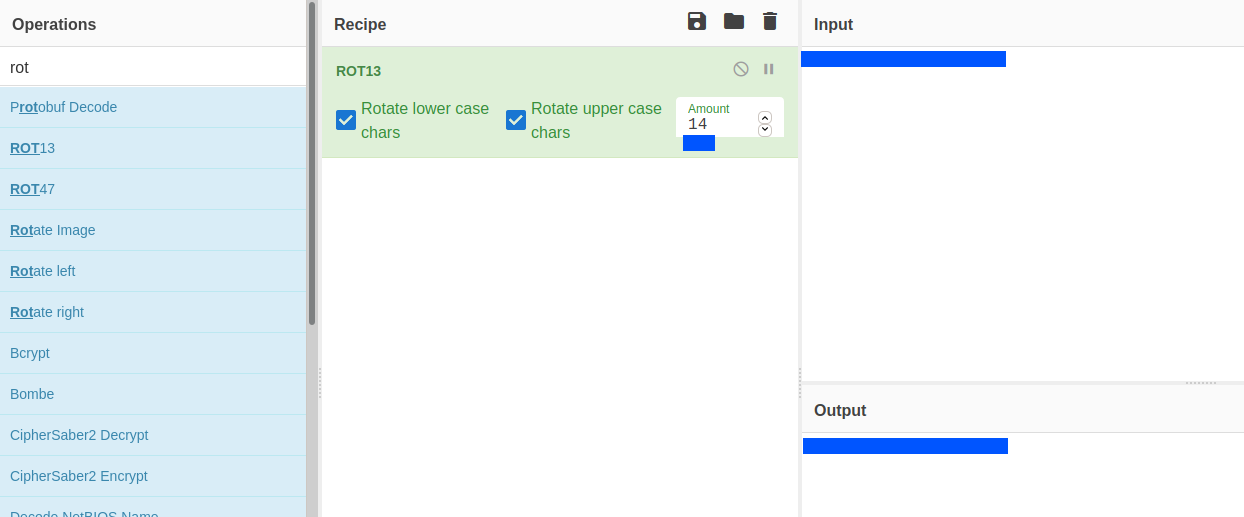
Again, I used cyberchef to decode the text but this time it was rot13 cipher with a key of 14.
Fire flag
Again, I used the same locate command to get the location of the flag.
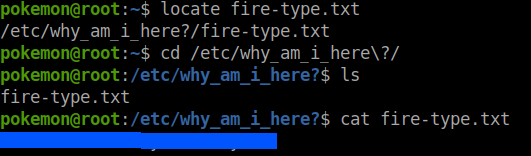
I used the command line base64 tool to decode the text.
echo "base64-content" | base64 -d

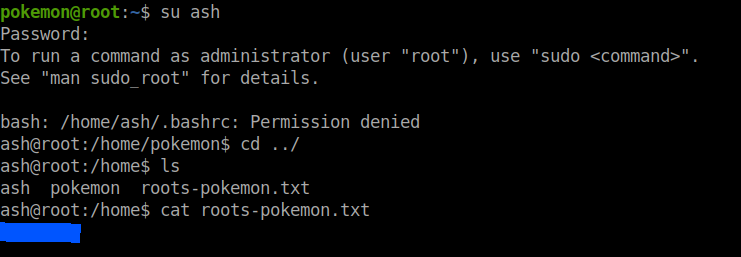
Roots flag
I had no luck with the locate command this time. So, I manually searched through the directories. And finally, I found this file which had the password for the user ash.
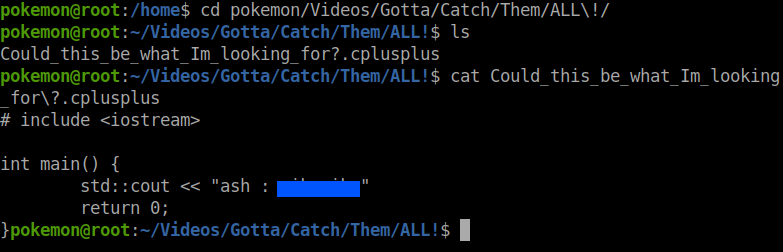
Then I changed the user to ash.
su ash
I found the roots flag in the /home directory.
Viola!! We got all the flags.
That’s it folks. Happy hacking!!!