Retro is a hard level room in Tryhackme but in my opinion it is a intermediate level room. The exploits for this room are way too easy to find. The objective is to get the user and root flag.

| Author | DarkStar7471 |
| Description | New high score! |
Deploy the VM and lets go.
Enumeration
First up is our usual nmap scan.
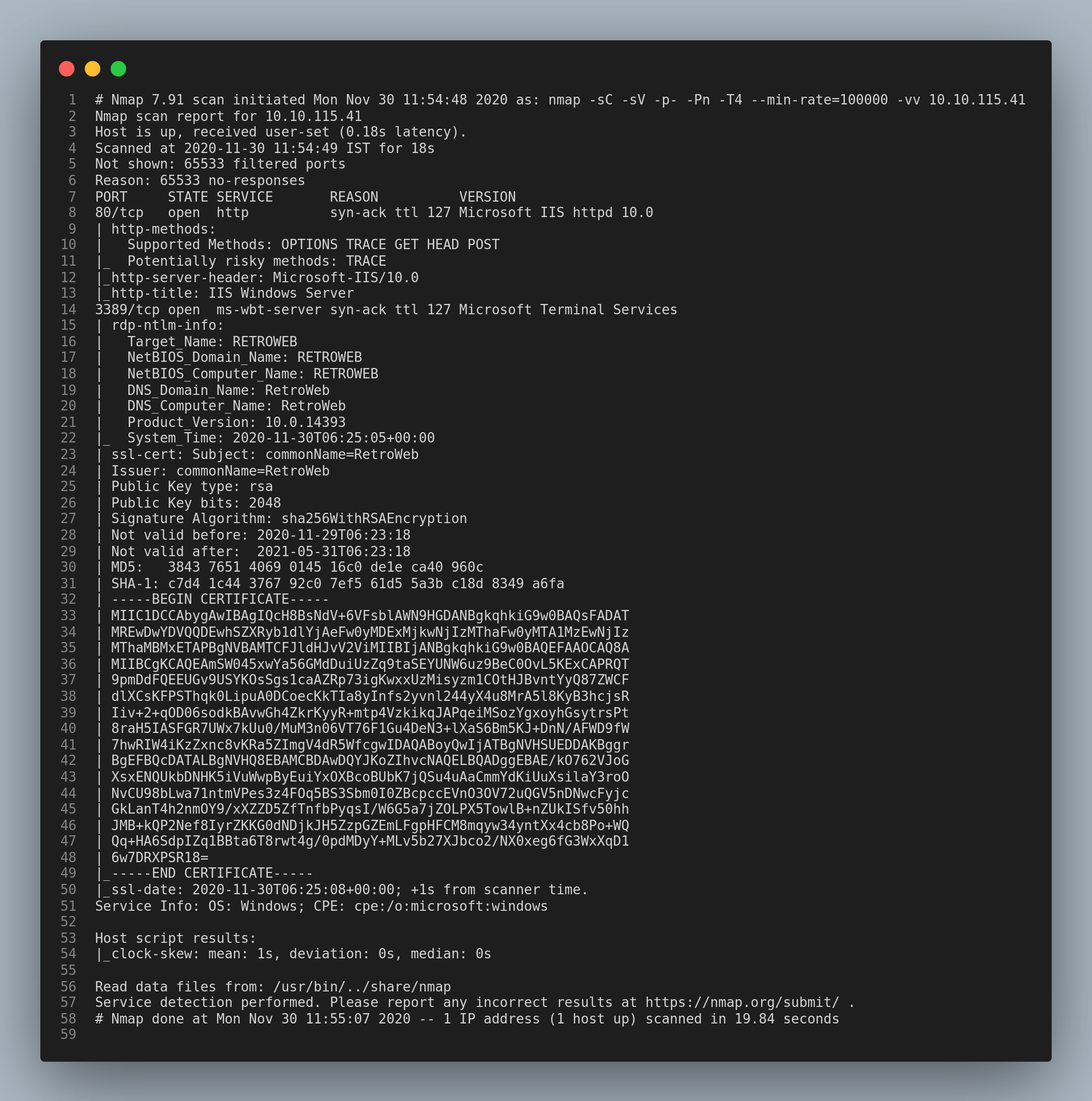
The ports 80/http and 3389/rdp are open.
The http service shows that the server runs Microsoft IIS service.
Run gobuster to bruteforce the hidden directories.
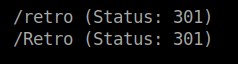
This answers the first question.
Moving into the directory the first thing I noticed is the username Wade.
After looking through some of his posts I found the password.

In case you can’t find the post, here is the link to post…
http://machine-ip-addr/retro/index.php/2019/12/09/ready-player-one/#comment-2
User flag
Fire up Remmina to connect to the RDP service. Fill up the credentials that we just found.
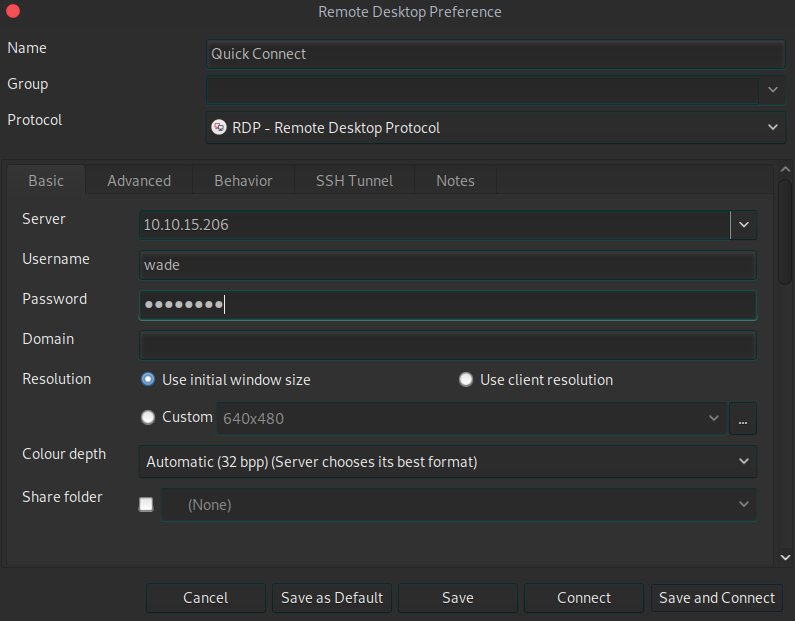
Click on Save and Connect and the wait for the windows desktop to show up.
In the desktop we can see the user flag.

We got the user flag. Let’s move to the root flag.
Root flag
I saw the hint given for the root flag and found that it was something to do with history. And this caught my attention…
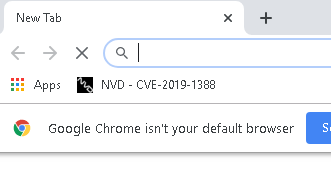
I also checked the history of chrome and saw that the user has visited the same website.
The exploit and demo on how to exploit the vulnerability was given in the github page of the author. And I found the exploit in recycle bin of the machine which made my work easier.

I tried to run the exploit by following the demo but I was stuck in the portion where the certificate should be opened in the browser.
Instead, I found this exploit on github.
Download the zip file, unzip it and transfer it to the remote machine using python.

And finally execute it.
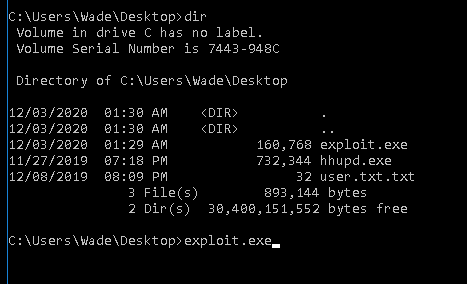
The Administrator’s command prompt pops up.

Bingo!! We got the root flag.
That’s it folks. Happy hacking!!!